Networks of pro-Kremlin Telegram channels spread disinformation at a global scale
Three networks comprising fifty-six channels targeted Telegram users in twenty countries and ten languages
Networks of pro-Kremlin Telegram channels spread disinformation at a global scale
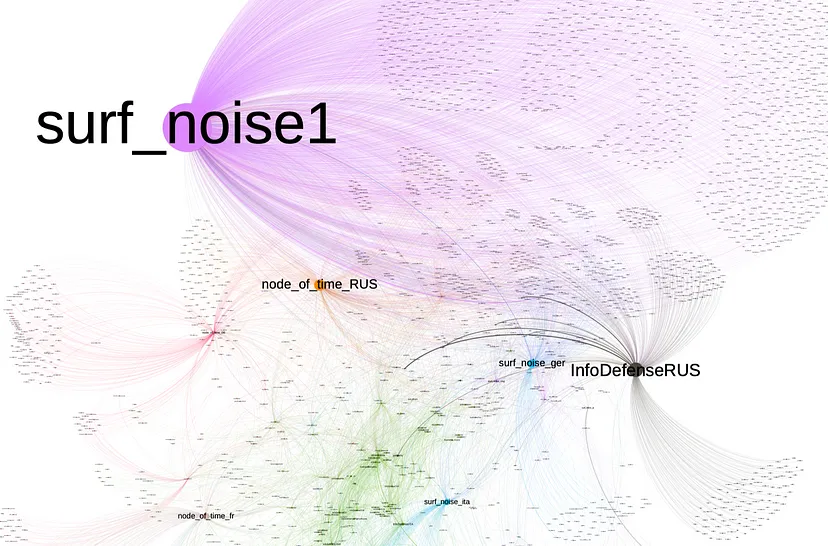
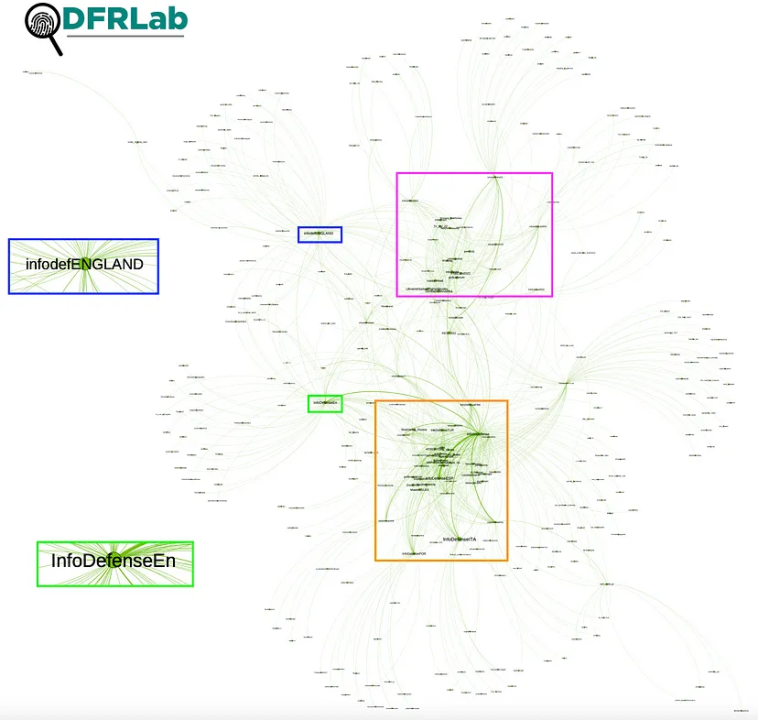
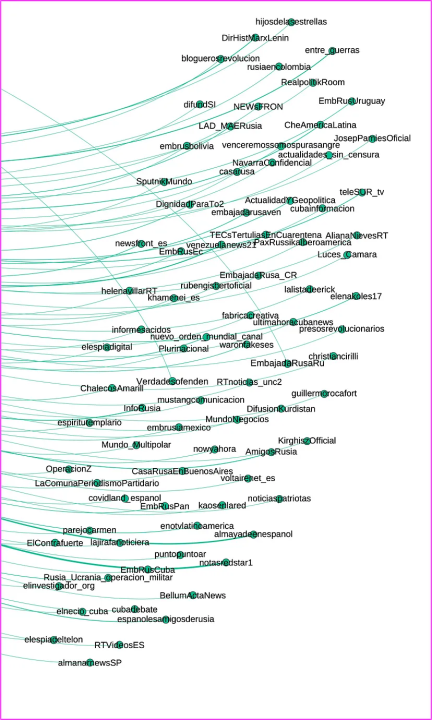
BANNER: Close-up view of a network graph showing forwarded messages from the fifty-six analyzed Telegram channels. (Source: @sayyara_a and @nikaaleksejeva/DFRLab via Telegram API, TGStat and Gephi)
Fifty-six pro-Kremlin Telegram channels divided into three networks of similarly named accounts are spreading pro-Kremlin narratives to users worldwide, including in Europe, Asia, South America, and the Middle East. The channels purport to share “truthful” information but are in fact conduits to help pro-Kremlin narratives reach people in other languages. A language assessment revealed that the channels’ content utilized both machine and human translations. Open-source analysis also revealed that one network is connected to a Kremlin-affiliated voluntary military training program called NVP ROKOT.
An analysis of forwarded posts, creation dates, and naming systems reveals that all three networks — Surf Noise, Info Defense, and Node of Time — are connected, with Info Defense and Node of Time being closely associated with one another and Surf Noise existing on the periphery. The cross-amplification efforts between the channels were most evident in Russian, German, Italian, and Spanish. A cluster of thirty-four Info Defense channels was the most interconnected, sharing each other’s posts despite language barriers.
This investigation sheds light on how pro-Kremlin Telegram channels try to reach users in other languages globally. Yet their simplistic approach, combined with a lack of obfuscation, suggests that the network operators are not sophisticated or well-resourced.
Telegram is the primary platform for sharing information about the Ukraine war. The platform has loose content moderation politics, making it fertile ground for disinformation.
General overview of the channels
The DFRLab identified three groups of Telegram channels employing similar naming patterns to coordinate across continents in various languages. There were ten channels containing “Node of Time” in their channel name. An additional eleven channels incorporated “Surf Noise,” while another thirty-five channels used “Info Defense” or “Info Def.” The channels operated in more than ten languages and targeted over twenty countries with Kremlin propaganda.
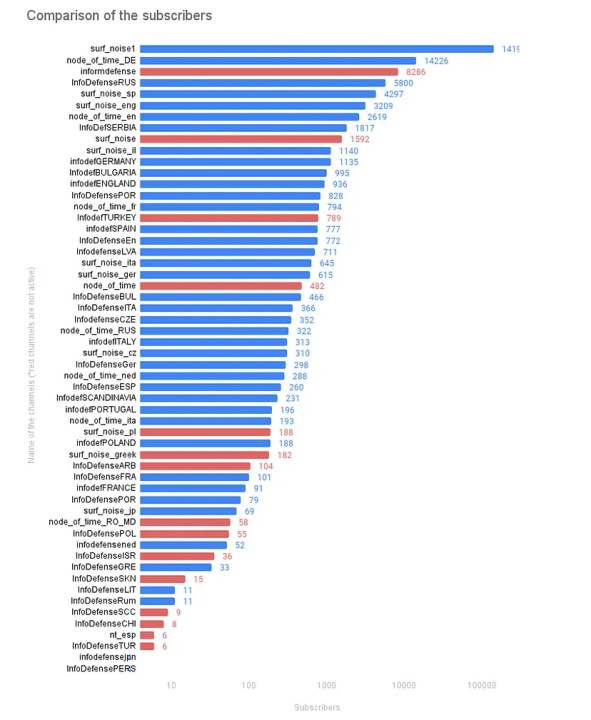
The channels with the largest subscriber count from each network were the Russian account @surf_noise1, the multi-language account @InfoDefense, and the German account @node_of_time_DE. Fifteen of the fifty-six channels have been inactive for at least one month.
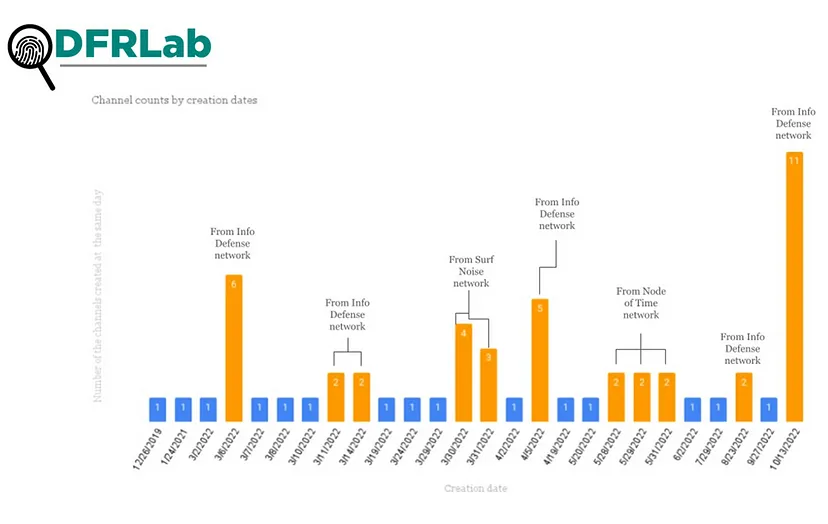
Several channels had creation dates in common. Twenty-eight of the thirty-five channels in the Info Defense cluster shared their creation date with at least one other channel in the cluster.
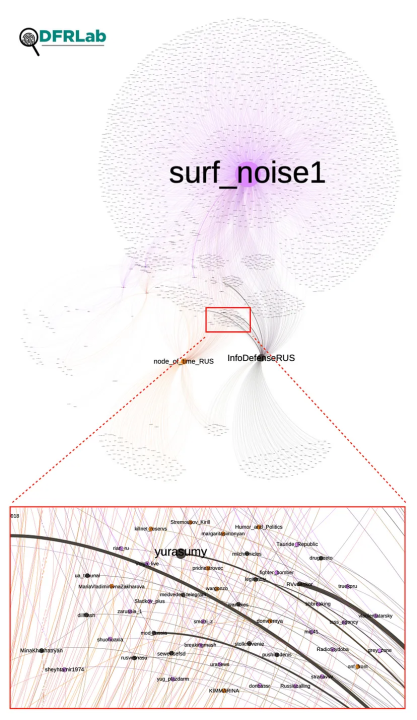
The DFRLab used Telegram’s API to collect 45,054 messages forwarded by the fifty-six Telegram channels, and TGStat to collect 12,593 messages forward from them by other channels. The observation period for this analysis began February 24, 2022 — on the day of Russia’s invasion — and continued through January 17, 2023. This data is represented in a network graph consisting of 3,871 Telegram channels, represented by nodes, and 57,646 forwarded messages, represented by edges. The direction of each edge starts at the source channel and goes to the channels where it was forwarded. The node size represents the number of incoming messages and highlights the amplifiers. A modularity analysis, which identifies accounts that are closely connected based on how they amplify each other’s content, detected nine clusters.
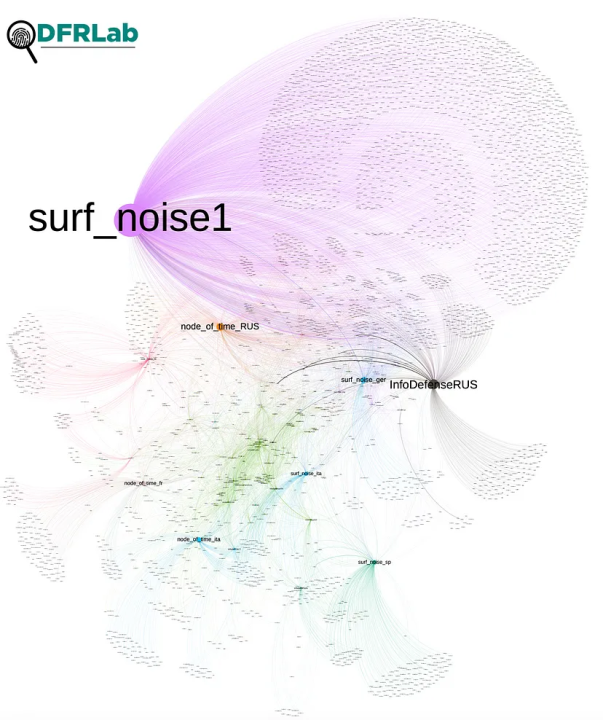
Surf Noise and peers
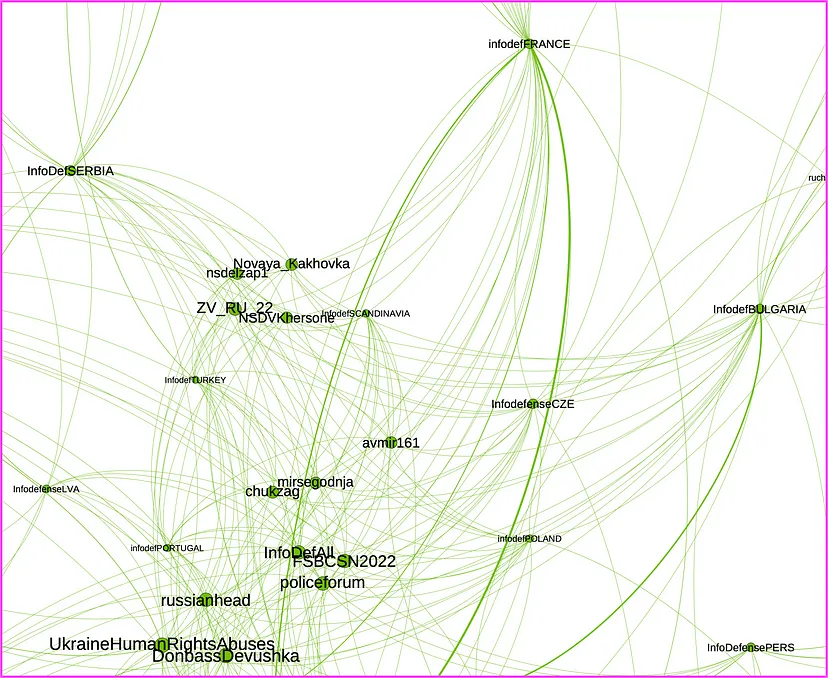
The network graph revealed that @surf_noise1 is the largest amplifier, but despite its size and activity, it exists on the margins of the larger network and is most closely clustered with the @node_of_time_RUS and @InfoDefenseRUS clusters. All three channels have different approaches to the content they post; @surf_noise1 often posts news about the activities of the voluntary military training program NVP ROKOT, while @node_of_time_RUS is more focused on international news and @InfoDefenseRUS posts updates from the front lines of the war.
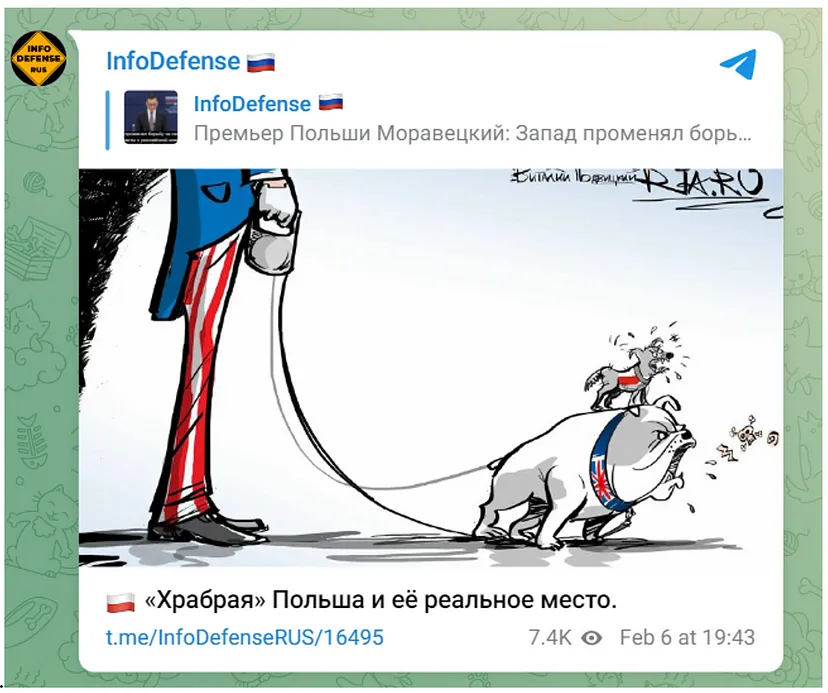
The second largest account in the Info Defense network is the Russian account @InfoDefenseRus, which spreads narratives that blame the United States and NATO for the invasion. For example, a February 6, 2023 post contained an old political cartoon that depicts Poland and the United Kingdom as dogs; Poland is shown as a small dog sitting on the back of the United Kingdom. The dog representing the UK is on a leash held by a figure dressed in garb resembling the US flag. The illustration is intended to convey that Poland is dependent on the UK, which in turn is dependent on the US. The cartoon was originally published in 2018 by Russian state-owned media outlet RIA Novosti.
When it comes to the sources of the forwarded messages, the accounts @surf_noise1, @node_of_time_RUS, and @InfoDefenseRUS all relied on similar pro-Kremlin channels for their content, including the accounts of Maria Zakharova, spokesperson for the Russian Ministry of Foreign Affairs; TASS, the Kremlin-owned news agency; Margarita Simonyan, editor-in-chief of RT and Sputnik; Denis Pushilin, head of the Donetsk People’s Republic; Semyon Pegov, a Russian blogger; and Dmitry Medvedev, the former Russian president.
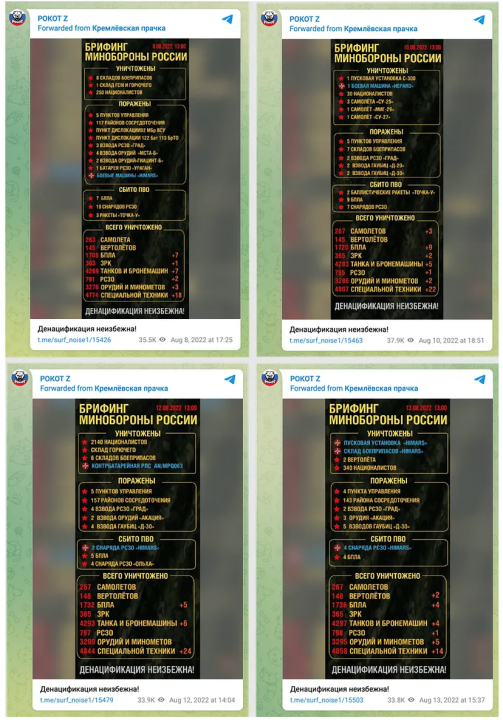
The network graph also shows a strong connection between @surf_noise1 and @kremlinprachka. The account @surf_noise1 forwarded seventy-one messages from @kremlinprachka that contained daily statistics published by the Russian defense ministry; every post included the caption, “Denazification is inevitable!” (“Денацификация неизбежна!”). In June 2022, the independent Russian media outlet Proekt analyzed daily defense ministry statistics and found the data was riddled with errors and falsehoods.
In 2022, there was a period of time in which Russian Telegram channels exposed the owners of other channels. The channel @Surf_noise was one of the accounts revealing the identities of other Telegram channel owners. One claim speculated that the deputy mayor of Moscow, Natalya Sergunina, ran @kremlinprachka. The DFRLab cannot confirm this allegation.
Affiliation with a Kremlin-approved military training program
The account @surf_noise1 frequently reports on the activities of the Kremlin-approved voluntary military training program NVP ROKOT. The program offers basic military training to volunteers and others to fight in Ukraine.
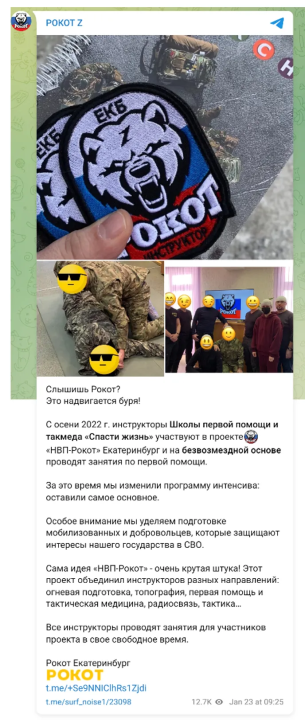
The NVP-ROKOT program originated in Volgograd but now operates across Russia, according to the state-owned outlet Gazeta. According to posts from @surf_noise1, NVP (“НВП”) is an abbreviation for “Наше дело правое, Враг будет побежден, Победа будет за нами,” which translates to “Our cause is right, the enemy will be defeated, victory will be ours.” The channel invites users to pick from a list of 120 closed groups, based on location, dedicated to trainings. The DFRLab could not further analyze these groups because users are vetted via a form that requests personal data before being accepted in the ancillary groups.
A pro-Kremlin Russian blog reported that the trainings were organized by the administers of the ROKOT Telegram channel, which appears to be a reference to @surf_noise1, which uses the handle ROKOT Z (“Deadline Z”). Further, the Russian outlet Volga News reported that the administrators of the program are Maryana Kudryashova and Anastasia Andreichenko.
According to posts made by @surf_noise1, NVP-ROKOT had a contract with DOSAAF (ДОСААФ), the Volunteer Society for Cooperation with the Army, Aviation, and Navy. DOSAAF was a paramilitary sport organization in the Soviet Union re-formed in December 1991 as the Russian Defense Sports-Technical Organization (ROSTO). The organization reverted to its old name in 2009 after President Putin signed a government decree on renaming the organization. The decree lists “tasks given by the state” to DOSAAF, including “maintenance of infrastructure facilities of DOSAAF of Russia in order to fulfill tasks during the period of mobilization and in wartime.”
According to posts from @surf_noise1, there were conflicts between NVP ROKOT and DOSAAF. NVP ROKOT, citing Kudryashova and Andreichenko, accused DOSAAF of not providing a physical space for their program and complained that the free program was being charged rent. Later posts suggest that the conflict was resolved, as ROKOT thanked DOSAAF for helping to organize trainings.
The Telegram channel @Surf_noise1 took over operations from the oldest channel in the network, @Surf_noise. The latter channel was created on December 26, 2019, and has not been active since January 24, 2021, when the former was created. The third post by @Surf_noise1 claimed that @surf_noise was suspended after a mass reporting campaign was carried out against the channel “from the territory of Ukraine.”
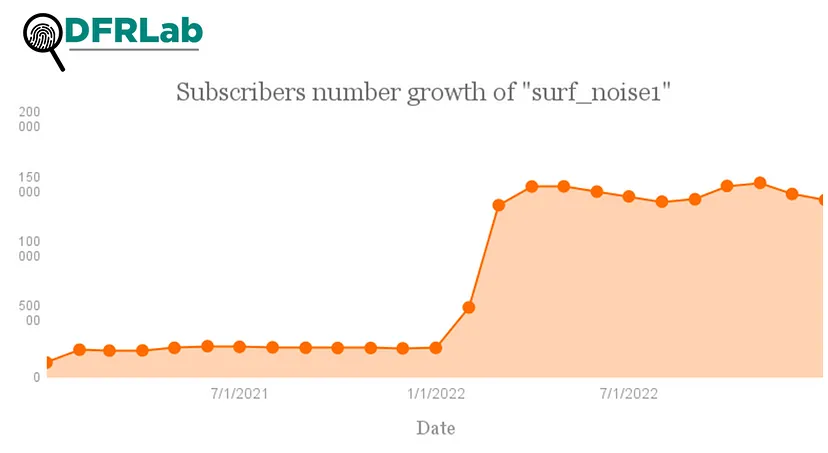
Russia’s invasion of Ukraine boosted @surf_noise1’s audience. Between February 24 and 25, 2022, the channel gained 8,677 new subscribers. On February 26, the channel gained an additional 12,706 subscribers.
Info Defense and volunteer translators
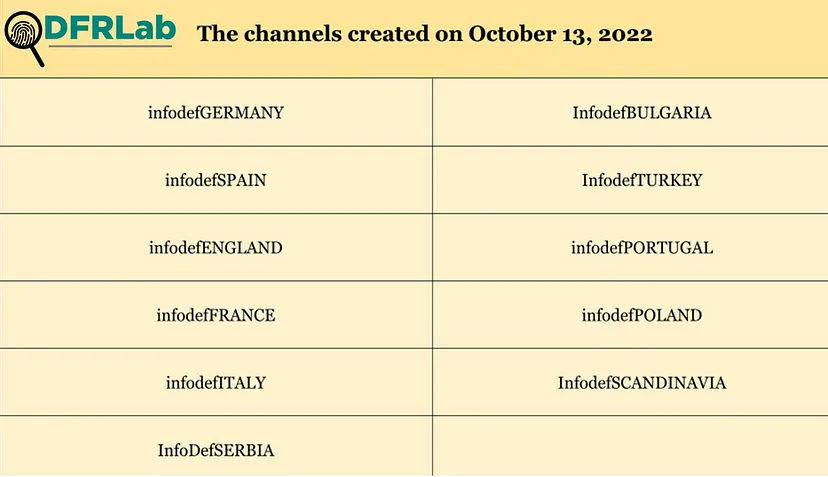
Info Defense is the second-largest cluster identified in the network graph. The cluster consists of many channels targeting specific countries. Eleven channels in the Info Defense network were created on October 13, 2022.
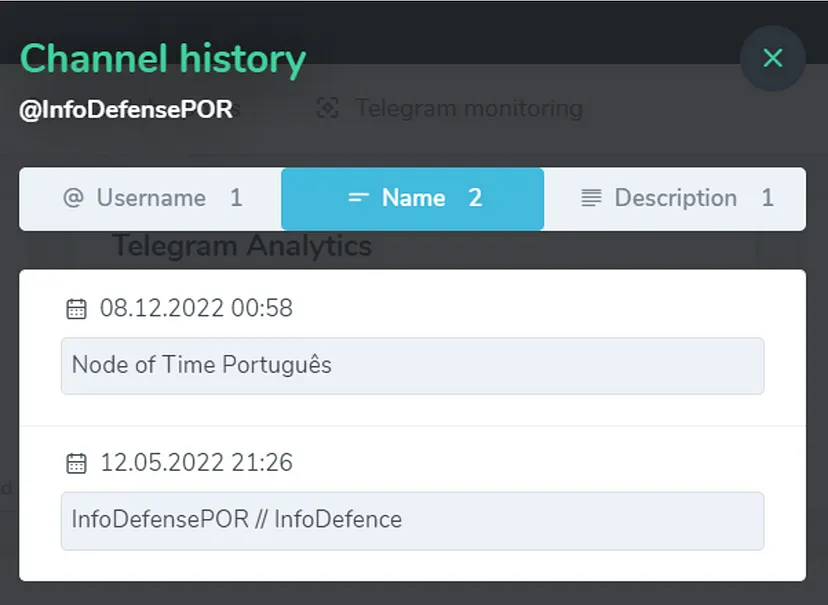
Channel history data from TGStat reveals connections between the Info Defense network and the Node of Time network. For example, the channel @InfoDefensePOR was created on March 6, 2022, and used the name “InfoDefensePOR // InfoDefence” until December 8, 2022, at which point it changed its name to “Node of Time Português.”
The channel description for @InfoDefenseSerbia suggests a possible affiliation with Yuri Podolyaka, a popular pro-Kremlin blogger of Ukrainian origin, as it presents itself as “The channel of Yuri Podolyaka, the most famous military blogger in the Serbian language.”
A modularity analysis conducted via Gephi revealed that the Telegram channel @InfoDefense is central to this network, as seen in the box below outlined in orange. Channels in the network dedicated to various geographies frequently forwarded pro-Kremlin posts from @InfoDefense, including @InfoDefenseESP (74 forwards); @InfoDefenseEn (71 forwards); @InfoDefenseARB (51 forwards); @InfoDefenseGer (39 forwards); and @InfoDefenseFRA (36 forwards).
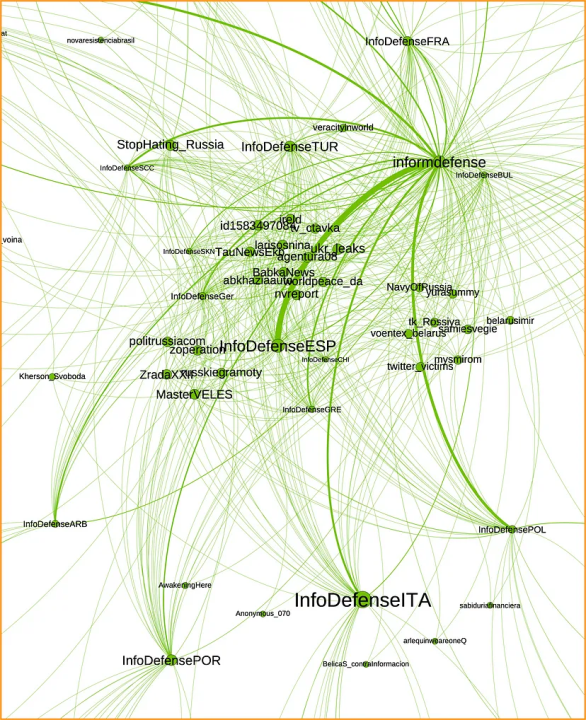
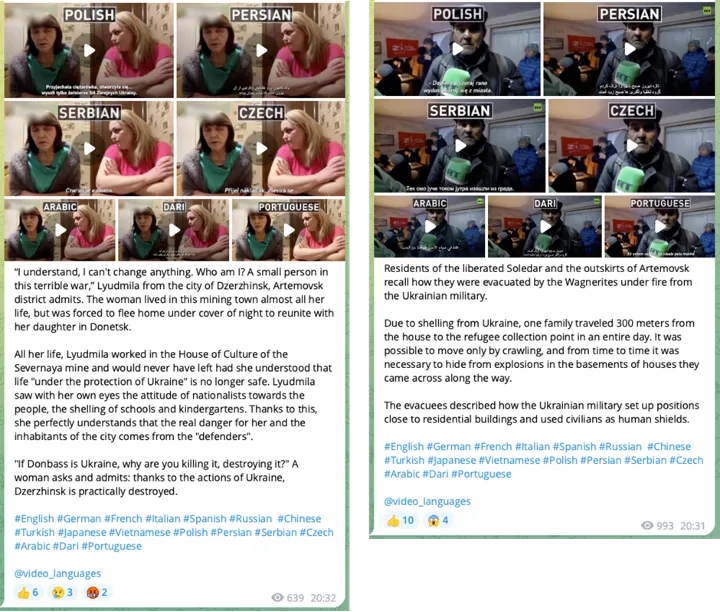
The amplification went in the opposite direction as well. For example, @InfoDefense forwarded the same Russian-language video from each respective account, using captions written in Arabic, English, Greek, Spanish, and German. The account also directly posted the same video with captions written in French, Ukrainian, Swedish, Polish, Portuguese, and Italian. The DFRLab could easily locate the videos because they each included Russian text that read, “Ukraine: castrate wounded Russian soldiers!” (Украина: Кастрировать раненых русских солдат!).
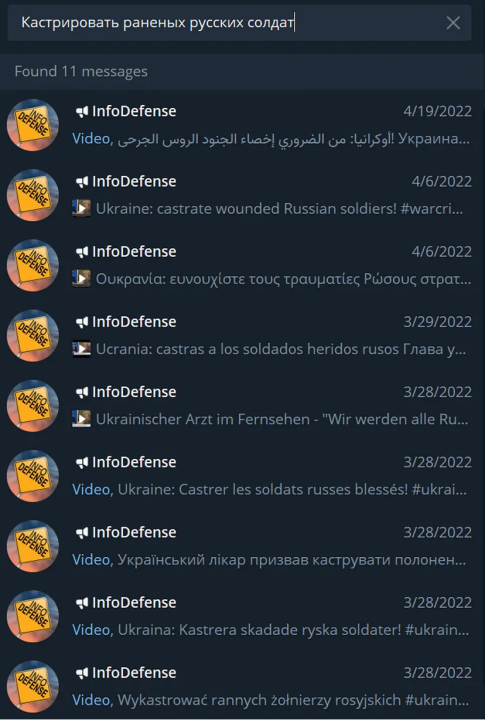
This behavior suggests that the channel serves as a hub for content to be amplified in other languages. A call to action, written in Russian, is pinned to the @InfoDefense channel, asking people to translate and disseminate the channel’s content and “break through the information blockade TOGETHER.”
The DFRLab consulted our global team of researchers to examine the accuracy of the @InfoDefense network’s translations. The translation quality suggests that non-native speakers and machine translations were involved. For example, at 00:40 in the Italian video, the wrong article, gli, is used, instead of i. In the Ukrainian translation, the word prizvav (“призвав”) might have been used by a bilingual person as a direct adaptation of a Russian word meaning “mobilization,” but the correct word in Ukrainian would be zaklikav (“закликав”). In Spanish, a voiceover was done by an individual who appears to have a Russian accent, while the translation uses confusing sentence structures. In German, the voiceover was done by a non-native speaker. The Arabic version contains many errors, suggesting the use of machine translation. The French version also includes poor language quality.
The channel @InfoDefense ceased operations on October 21, 2022. Its last post redirected users to its new channel, @InfoDefAll, which has only posted three times. The first two posts, made in October 2022, were a Russian and English version of the call for “translators, editors, people available to assist with information distribution.” On January 25, 2023, the same post appeared in Spanish.
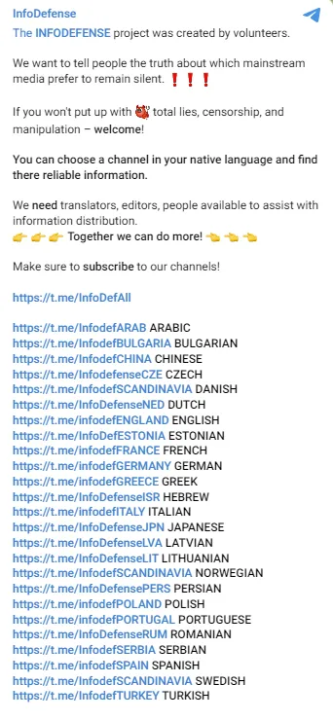
Twenty-seven region-specific channels from the InfoDefense network remained active at the time of writing.
Country-specific clusters
The accounts targeting Italian and German speakers appear to have a strong connection. Gephi’s modularity analysis suggested that @surf_noise_ger is in the same cluster as @node_of_time_ita, @infodefITALY, and @surf_noise_ita. However, @infodefGERMANY and @node_of_time_DE were detected in a separate cluster, despite some instances of forwarded messages connecting the accounts.
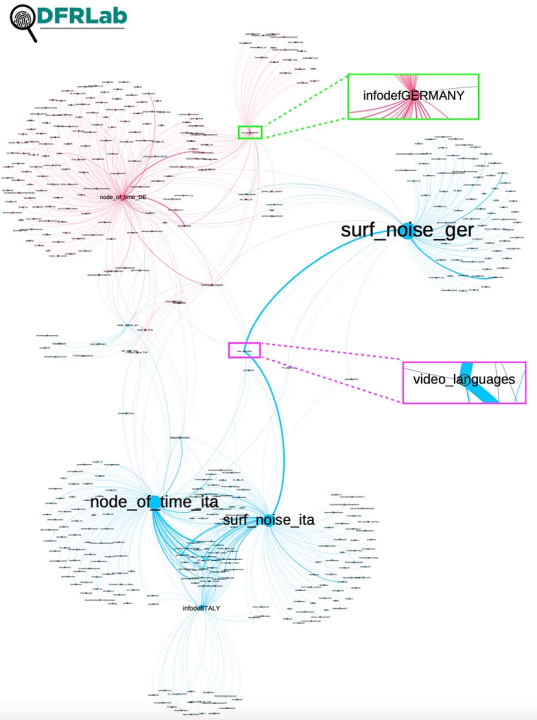
Both @surf_noise_ger and @surf_noise_ita forwarded more posts from @video_languages than any other accounts — 348 and 342 times, respectively. The official name for the @video_languages channel, РОЛИКИ НА РАЗНЫХ ЯЗЫКАХ, translates to “Video Clips in Different Languages.” The channel’s purpose is similar to @InfoDefense, but it includes subtitles in its videos, making them more accessible to a larger audience. The quality of subtitles produced varied but was generally of better quality than the translations offered by the Info Defense network. For example, the Serbian translation indicated the involvement of a native speaker, but it was written in cyrillic, which Serbian nationalists mostly use. The Chinese translation also was correct, and it used casual forms of expression, suggesting that it was done by a person familiar with Chinese. The German, Arabic, and Persian translations also seemed to be generated by people rather than machine translation. However, the French and Italian videos appeared to be machine-translated.
Amplifying Russian embassies abroad
Other language-specific networks identified in Gephi’s modularity analysis were centered around @surf_noise_sp’s connection to @node_of_time_fr, @surf_noise_jp, and @infodefSPAIN. Notably, @surf_noise_sp actively spread the Kremlin narrative that falsely alleges that Ukrainians are Nazis, using the word word “Nazi” in its posts 404 times.
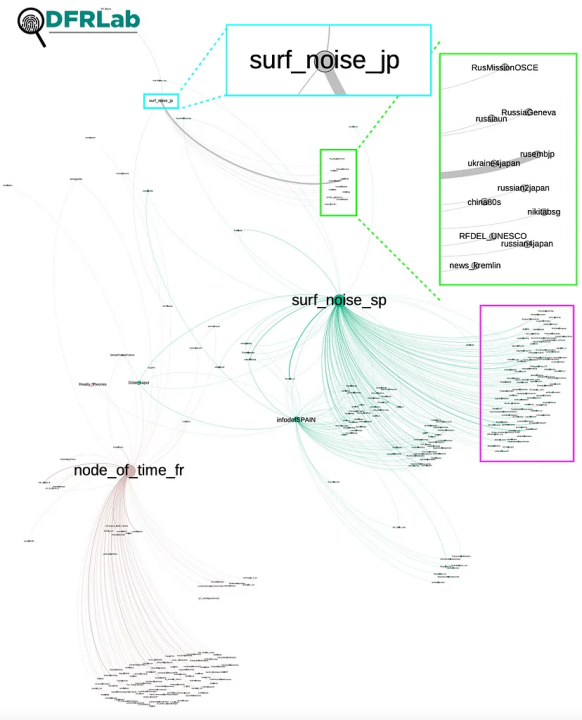
Several channels also forwarded Telegram content from Russian embassies in Japan and Latin America. For example, @surf_noise_jp forwarded messages from the Russian embassy in Japan 1,254 times. In addition, both @infodefSPAIN and @surf_noise_sp forwarded messages from Russian embassies in Spain (101), Argentina (48), Nicaragua (32), Venezuela (32), Panama (22), Chile (20), Uruguay (17), Ecuador (15), Mexico (9), Cuba (3), Costa Rica (1), and Bolivia (1). The DFRLab has previously identified Russian embassies as amplifiers of Russian disinformation in Latin America. Russian embassies also disseminated false fact-checks about the Bucha massacre.
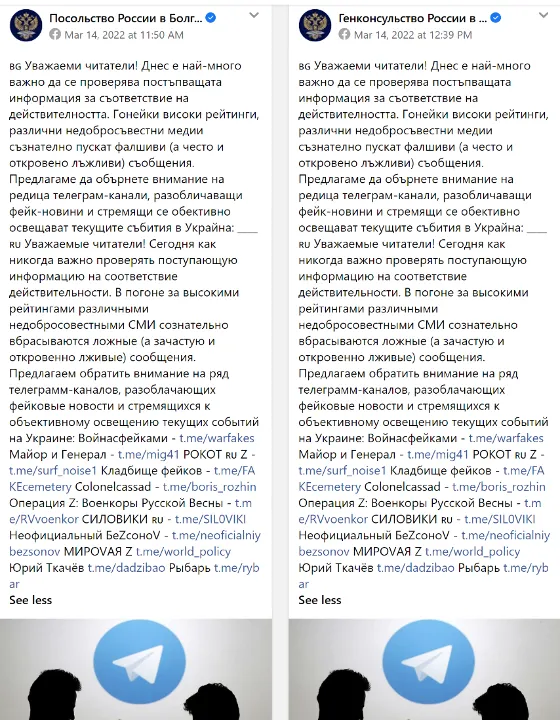
Additionally, the Russian embassy in Bulgaria and two of its consular branch offices promoted @surf_noise1 and eleven other Telegram channels, describing them as “channels that cover the current events in Ukraine objectively” and “expose fake news.”
Conclusion
The three networks of Telegram channels uncovered by the DFRLab actively spread Kremlin propaganda and disinformation about Russia’s invasion of Ukraine to a global audience. Despite the large number of countries the channels targeted globally, the number of subscribers, average readership of posts, and content quality suggest that the networks have limited resources, which potentially explains their call-outs for translation assistance. Further research will hopeful shed more light on country-specific targeting on Telegram, as well as local Telegram influencers that amplify pro-Kremlin propaganda.
Cite this case study:
Nika Aleksejeva and Sayyara Mammadova, “Networks of pro-Kremlin Telegram channels spread disinformation at a global scale,” Digital Forensic Research Lab (DFRLab), March 1, 2023, https://dfrlab.org/2023/03/01/networks-of-pro-kremlin-telegram-channels-spread-disinformation-at-a-global-scale/.

