Data and Defense: The Case of Strava
The unexpected role of civilian technology in warfare in the light of Strava heatmap incident
Data and Defense: The Case of Strava
The unexpected role of civilian technology in warfare in the light of Strava heatmap incident

Sensitive information about the location and staffing of military bases and outposts was inadvertently revealed by Strava, a fitness tracking company. Over the weekend, researchers and journalists raised the alarm about how much sensitive data can be gathered from the freshly released Strava Global Heatmap. This situation served as a reminder for how much warfare and civilian technology are interrelated in this day and age.
@DFRLab collected a few examples of the type of information extracted from the Strava heatmap.
Overview
The Strava heatmap was first released in November 2017, but the potential security implications were not identified until this weekend. The Strava app is operational on a variety of devices — including smartphones, trackers, and smartwatches. If the user doesn’t turn data transmission off, the user’s data automatically feeds into Strava’s full, and now public, data file. For users in sensitive locations, users must manually opt-out.
Reporting put a spotlight on the fact that not all soldiers turned off the tracking function while on duty, which revealed sensitive data. This is not the first time irresponsible use of civilian devices led to unintentional exposure of sensitive information.
The revelations shown in the VICE Documentary Selfie Soldiers, illustrated a similar case. Then @DFRLab and the open source investigative collective Bellingcat teams proved the presence of Russian troops in Ukraine using photos posted publicly on social media. Each example clearly demonstrate how deeply modern warfare is interconnected with technology, including devices, apps, and platforms for personal — or civilian — use.
Bellingcat recently published a guide explaining how to use and interpret Strava data and how trustworthy it actually is. We took took a closer look into a few examples.
Known Military Bases and Facilities
One of the ways to use this data is to view the Strava visualizations with satellite imagery of known military establishments. In doing so, the popular jogging routes were observed, giving away information about personnel movement within the base. Judging by the intensity of the lines on the map and uploaded workout segments, even the numbers and identities of personnel can be projected.
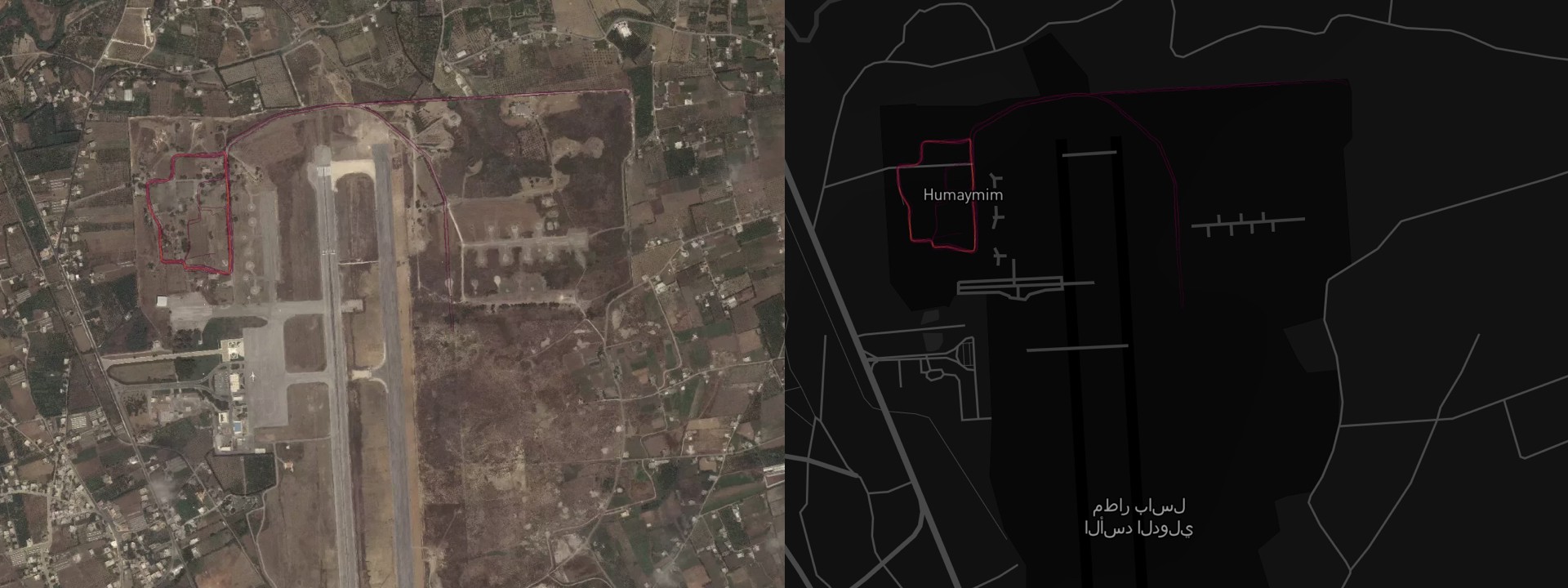
Knowing the zones where soldiers spend their off-duty time, potential adversaries are armed with a powerful piece of intelligence. In the case of Russian airbase in Khmeimim, we found that most of the movement concentrated in the top left corner of the base.

The same patterns were clearly visible at the Russian naval facility in Tartus. The most popular route was at the bottom left corner of the dock.

Taking a look at the U.S. Department of Defense’s Pentagon in Washington, D.C., we did not find the most popular jogging routes, but some interesting walking patterns were observed. The majority of data surrounding the Pentagon corresponded with major highways and thoroughfares adjacent to the building. No data was revealed on walking patterns in the building itself, which suggested a data blackout or areas of low public connectivity.

Less Known or Unknown Bases
Another way this data can be used is to search for lesser known or secret bases around the globe. Over the weekend, researchers shared various locations of potential military facilities. Most of these establishments showed up on the Strava map as bright circles or rectangles in remote areas. Since the soldiers that were stationed in the bases were unable to leave the premises, they usually jogged in the same patterns every day. The same rule applied to stadiums and tracks — bright outlines of ellipses tended to stand out.
This pattern applied to the Russian base in Dushanbe, Tajikistan. The 201st Motor Rifle Division’s base stood out from afar. The location of the base was confirmed after cross-checking the data with WikiMapia.

A good example of how to look for potential military establishments was found in Vladikavkaz, Russia. Even though this building complex in North Ossetia was not marked as a military base on the maps, the running patterns suggested military presence. When the location of a potential military facility is established, satellite imagery can be used to inspect it more thoroughly.

Here are the above-mentioned establishments pinpointed on the map.
Personal Data
Lastly, Strava can be used to extract data about individuals serving in military facilities. One of the options that Strava offers is to share the segments of your workouts with the public and compare your best times with friends. These segments were uploaded on the Strava map, showing exact workout routes. When these segments were cross-referenced with WikiMapia data, or the location from the heatmap, individuals working out in the territories of military facilities were found.

When the segment is found, the profile can then be accessed. Most of the users uploaded pictures of themselves and their friends from past workouts. These photos revealed the identities, including some families. Some users even used their real names, which can then be useful in further analysis to find more of their digital footprints.
In this case, a Strava user named Igor was found jogging inside military facilities in Sevastopol, Crimea. Pictures of himself, his family and his jogging routes were posted to his profile.

Additionally, the profile contained a list of Igor’s friends, which can be also used in research to get a better view of the personnel serving in the Sevastopol military facility.
Some researchers even provided suggestions on how to make the anonymized data in the heatmap visible. If these loopholes are not fixed by the Strava company, a lot of sensitive identities could be compromised.
Conclusion
The information released by Strava was detailed enough not only to find military bases, but also to investigate them and the personnel serving inside. A user-friendly interface on the Strava application gave away sensitive information to the public.
This episode included one forced and one unforced threat. The forced threat was military facilities revealed by a commercial tool designed for civilian use. The unforced threat included irresponsible behavior and mistakes made by the soldiers serving in these facilities making personal data available with potentially fatal consequences.
Once again, personal data demonstrated how interconnected modern warfare is with personal technology and devices. Commanders running military facilities need to re-think their security strategies to cover not only the enemy actions, but their fellow soldiers, as well.
Follow along for more in-depth analysis from our #DigitalSherlocks.

