Venezuelan Pro-Regime Accounts Publish Personal Data of Phishing Victims
Phishing attack on website run by Venezuelan opposition exposed data of hundreds of sympathizers of Juan Guaidó, jeopardizing the victims’ safety
Venezuelan Pro-Regime Accounts Publish Personal Data of Phishing Victims

BANNER: (Source: @DFRLab)
A leaked database of Venezuelan opposition sympathizers published on February 17 by pro-Maduro Twitter accounts and websites was, at least in part, the result of a regime-linked phishing operation.
As some of the individuals whose names appear on the lists expressed in phone conversations with @DFRLab, the data leak put their physical security at risk by rendering them likely targets of harassment from the Bolivarian Service of Intelligence (SEBIN, Spanish acronym), the Maduro regime’s political police force known for brutality against opposition leaders and sympathizers, and possibly from hostile Maduro supporters not directly linked to the regime.
The cyberattack perpetrators violated the right to privacy of thousands of Venezuelan citizens. The incident further exposed the close affiliation between pro-regime websites and Twitter accounts, on one hand, and sectors of the regime, on the other.
The Attack’s Target
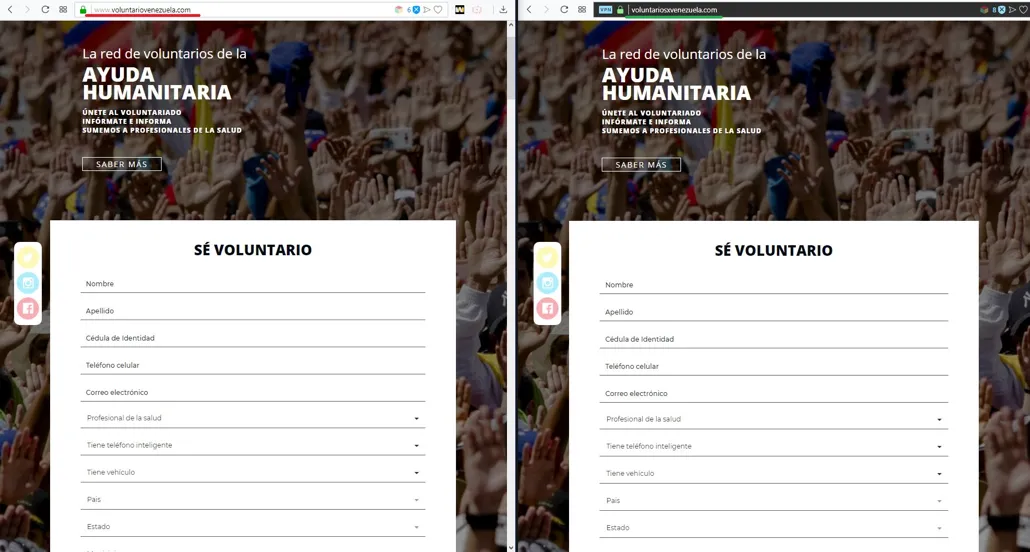
The attack targeted voluntariosxvenezuela.com (a transliteration of Voluntarios por Venezuela, Volunteers for Venezuela), a website set up by self-declared Interim President Juan Guaidó to recruit volunteers to deliver aid sent by the United States to people inside the country. The site allows volunteers to register with their name, email address, phone number, and cédula number, a government-issued ID.
When trying to access the site through both Cantv and Movilnet — the two state-owned internet service providers — users were automatically redirected to the now-offline website voluntariovenezuela.com (omitting the “s” and the “x” of the authentic site). The site was visually identical and also included a registration form.
On February 12, Venezuela Sin Filtro (VSF), an independent research organization that documents blockages and cyberattacks in the country, first reported the phishing attempt on its Twitter account. VSF published an in-depth report on February 15 that noted that the information captured on the deceptive site was stored on a server whose IP address had links with the regime. (Of note, as the phishing pages are now offline, @DFRLab was unable to replicate VSF’s findings.)
The VSF researchers discovered that the deceptive website shared its host server with several phishing domains known to target Venezuelan users. All of the domains were registered with a phone number associated with an office inside Conatel, the Venezuelan communications regulator.
Following the release of the VSF report, several internet browsers, including Google Chrome, Mozilla Firefox, and Microsoft Edge, flagged the deceptive website as dangerous. On February 22, however, Venezuela Sin Filtro reported on Twitter that the phishing attacks had resumed, this time redirecting to the URL voluntariosxxvenezuela.com (with a double “x”). The new false website is offline at the time of publishing.
@DFRLab obtained a screenshot of the database with 24 names and cross-referenced the national ID numbers of individuals listed in the database with the National Electoral Council’s (CNE, Spanish acronym) electoral register, the top elections authority in the country. The ID numbers of 22 of the individuals corresponded with the ID numbers registered in the official database. The other two IDs did not appear on the census.
Afterwards, @DFRLab called each of the 24 phone numbers. Of the 24 individuals, @DFRLab reached 15 of them. All 15 confirmed that the email addresses listed on VoluntariosXVenezuela were correct, and seven of the individuals confirmed that they had attempted to login to VoluntariosXVenezuela from a Cantv connection before the attack was first reported. Some of them said they did not receive a confirmation email after their registration, which made them wary of the website.
Who Published the Data?
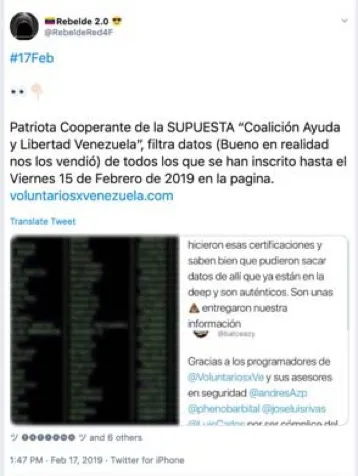
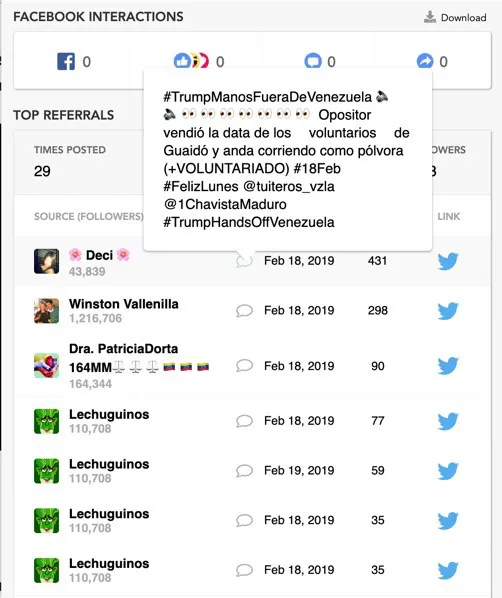
On February 17, several pro-regime-Twitter users, including @RebeldeRed4F, posted a list of 24 names, national ID (cédula) numbers, and phone numbers that allegedly belonged to people who registered on the VoluntariosXVenezuela website before February 15.
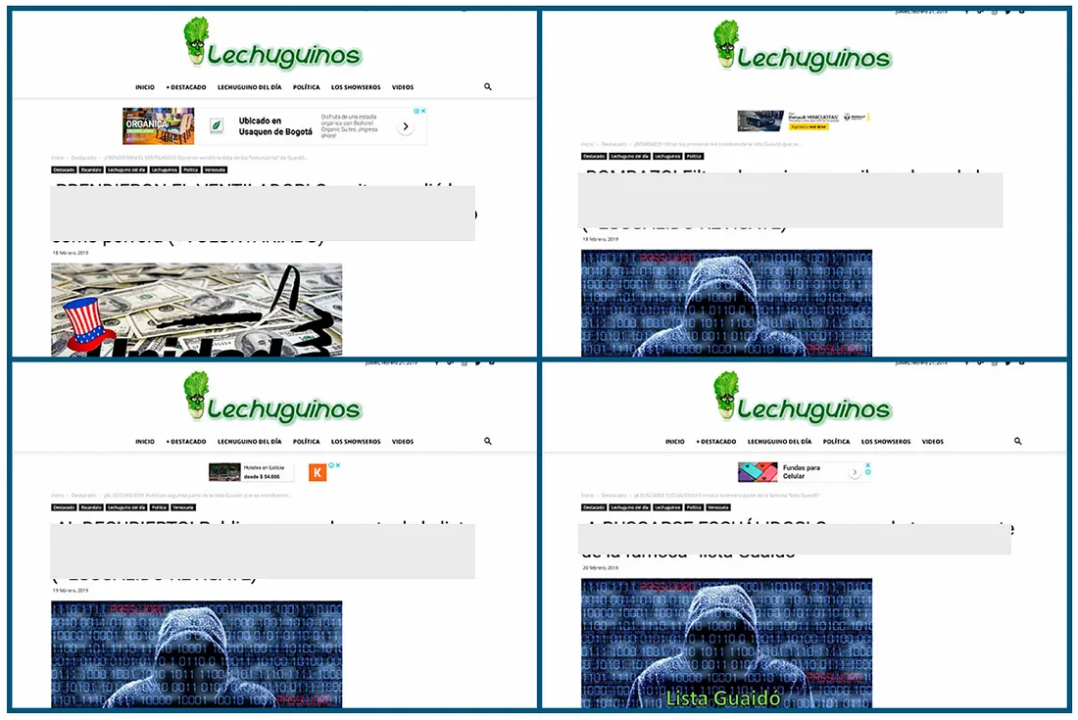
Later that day, Lechuguinos, a pro-regime media outlet, published the same list, as well as an additional list with hundreds of names. The outlet also posted a third list of names on February 20 and a fourth list on February 21.
Both @RebeldeRed4F and Lechuguinos pushed a narrative that aimed to blame the team running the VoluntariosXVenezuela website for the data leak. The @RebeldeRed4F account claimed that “the opposition sold the data to us,” while Lechuguinos claimed that the website’s staff “took advantage of the data from Guaidó’s ‘volunteers’ to do their business.” The overwhelming evidence that the data came from a phishing attack, however, discredits these claims.
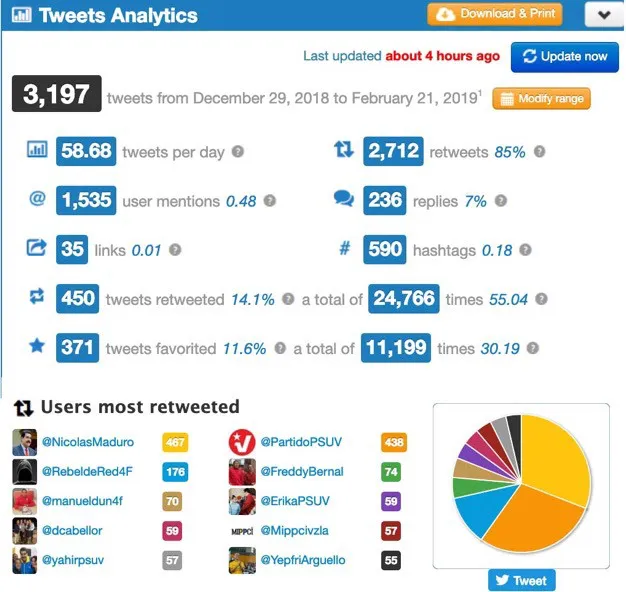
The fact that both the pro-regime account @RebeldeRed4F and Lechuguinos had access to the phishing database reveal the close links between these online-media entities and the orchestrators of the phishing attack. @RebeldeRed4F is a 28,800-follower-strong regime loudspeaker account, active since February 2012. Roughly 79 percent of the account’s tweets over the last two months are retweets, mostly of posts by accounts belonging to regime officials or parties, including Nicolas Maduro; Diosdado Cabello, the President of the National Constitutional Assembly; and the United Socialist Party of Venezuela (PSUV), the ruling party.
Lechuguinos has had an online presence since at least July 2016, when its first articles appeared online, according to Google search results. Still, its 111,000-followers-strong verified Twitter account has been live since 2011. The Twitter account publishes short statements that echo the Maduro regime’s narratives about the opposition, the United States, and Colombia. The Lechuguinos articles that included the lists of Guaidó supporters were in turn amplified by regime sympathizers on Twitter and Facebook.
Conclusion
After a phishing attack hosted on servers linked to the Maduro regime — as revealed by the February 15 VSF report — targeted the VoluntariosXVenezuela website, several Twitter accounts and websites known to serve as the regime’s loudspeakers published a database containing victims’ personal identifying information. This jeopardized the safety of hundreds of civilians who had signed up to support the opposition led by Juan Guaidó.
While the phishing attack briefly paused after VSF exposed it, it later resumed at a different URL.
The evidence of the phishing attack contradicts claims by pro-regime media outlets and social-media accounts that the data was sold to them by members of the opposition.
@DFRLab and the Adrienne Arsht Latin America Center will continue to monitor the digital information environment in Venezuela.
EDITOR’S NOTE: @DFRLab faced an ethical dilemma on whether to publish links to the leaked data as evidence of the attack in order to expose the actors likely behind it. In not republishing the links, @DFRLab is refusing to amplify data that can be easily accessed elsewhere on the internet out of respect for the privacy of the individuals affected.
Follow along for more in-depth analysis from our #DigitalSherlocks.

