KEY FINDINGS: Iranian Propaganda Network Goes Down
Facebook pages laundered Iranian propaganda in India, Indonesia, and Africa
KEY FINDINGS: Iranian Propaganda Network Goes Down

Facebook took down over 500 pages, groups and accounts on March 26, identifying them as part of a pro-Iranian propaganda network that attacked Israel, the United States, Saudi Arabia, and the Gulf States.
The network operated in multiple languages and targeted multiple regions, including South Asia, East Africa, and West Africa, as well as countries such as Indonesia. In some cases, the network directly reproduced Iranian state messaging, steering social media users towards websites, which repurposed content from state outlets and passed it on as their own.
In a blog post, Facebook explained:
“The administrators and account owners represented themselves as locals and made-up media entities, often using fake accounts — and they impersonated real political groups and media organizations. They posted news stories on current events and frequently repurposed and amplified content from Iranian state media about topics including sanctions against Iran; tensions between India and Pakistan; conflicts in Syria and Yemen; terrorism; tensions between Israel and Palestine; Islamic religious issues; Indian politics; and the recent crisis in Venezuela.”
This article sets out the top takeaways from the takedown. In the interest of transparency and of preserving the activity of this network for future study, the detailed evidence is set out in a separate deep dive.
India, Indonesia, Africa
The pages targeted countries and communities around the world, but had a particular focus on Indonesia, India, and Africa. They covered at least 15 countries and a dozen languages. The sheer scale of the operation, combined with assets which were taken down in earlier clean-ups, suggest that this was a state-backed effort.
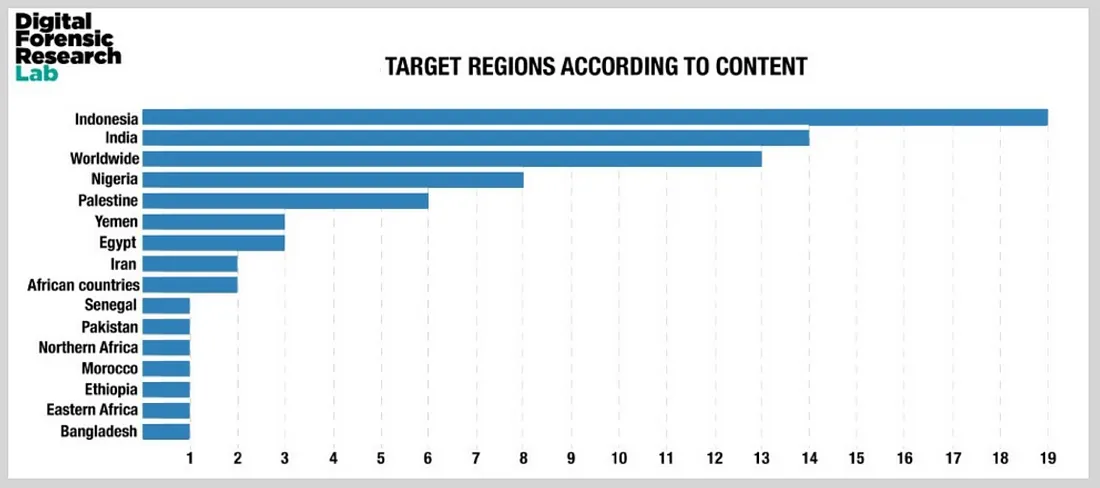
Iranian narratives
The pages routinely amplified Iranian state narratives, targetting Israel, the United States, and Saudi Arabia, especially for their roles in the Middle East, and focusing on the Yemen and Palestine conflicts.
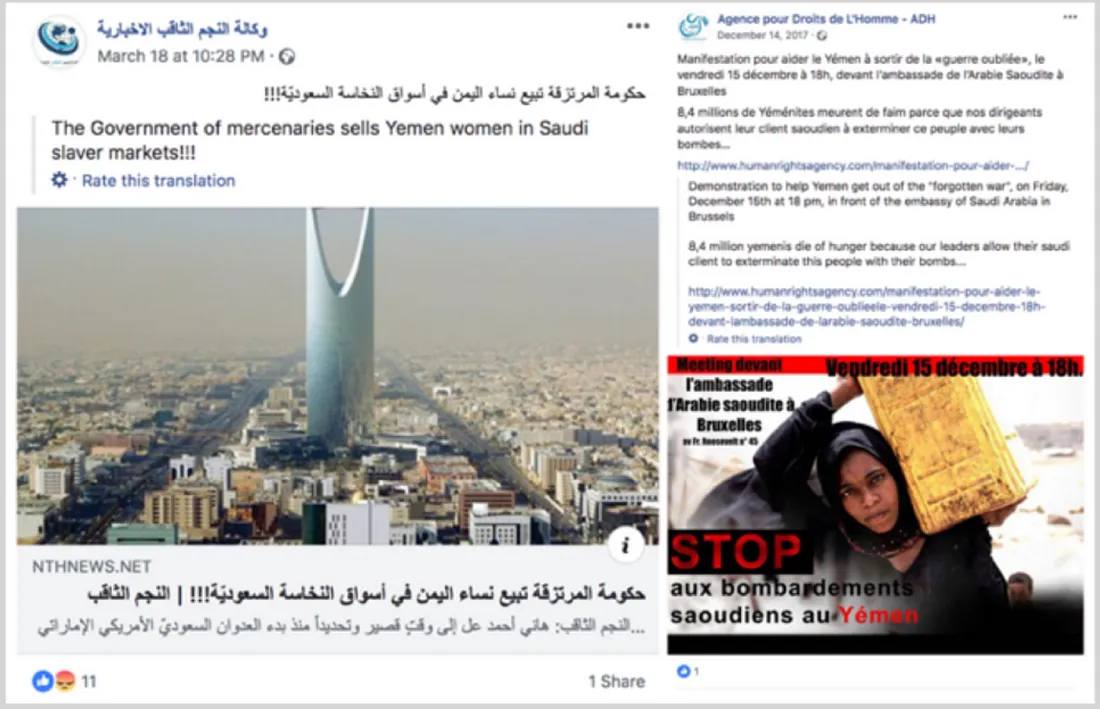
 Examples of anti-Saudi content. (Source: وكالة النجم الثاقب الاخبارية/archive, left; Agence pour Droits de L’Homme — ADH/archive, right)
Examples of anti-Saudi content. (Source: وكالة النجم الثاقب الاخبارية/archive, left; Agence pour Droits de L’Homme — ADH/archive, right)Laundering propaganda
The pages often shared articles from websites which reproduced, verbatim, content from Iranian state or state-allied outlets, such as PressTV. They functioned as a virtual laundromat for Iranian propaganda, stripping it of its attribution and passing it on to unsuspecting readers as an independent product.
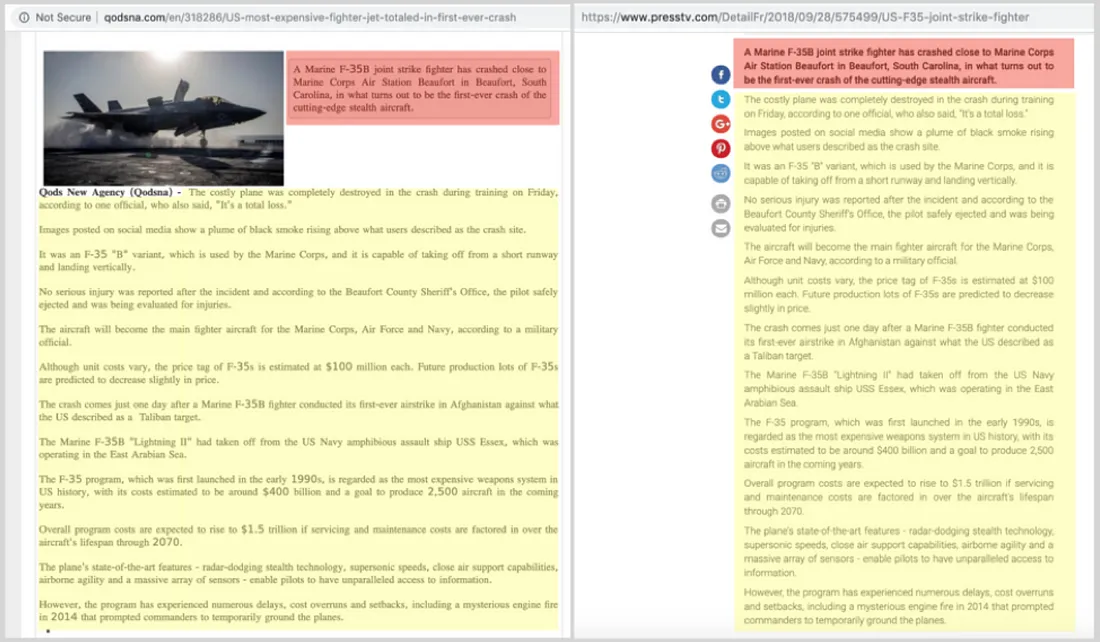
Run from Iran
Despite their focus on a wide range of countries, and their claims to be based in those countries, most of the pages were largely run by users in Iran.

Low engagement, low impact
In general, individual posts had low impact and scored little engagement. Some of the pages boasted large numbers of followers, but these appeared not to engage with the content, and may have been acquired fraudulently, by taking over or repurposing popular pages on unrelated issues.
Same-same, but different:
The operation strongly resembled an earlier operation called the International Union of Virtual Media (IUVM), which the DFRLab exposed in August last year as a key launderer of regime messaging. Facebook did not attribute the operation to IUVM directly, but the latest operation used the same techniques and pointed to some of the same websites, making attribution to the same network likely, although not confirmed.
Follow along for more in-depth analysis from our #DigitalSherlocks.

