Lingering Infektion: Latvian operation mimicked Secondary Infektion tactics
Faked documents pushed on fringe websites and social media, similar to operation uncovered in June 2019
Lingering Infektion: Latvian operation mimicked Secondary Infektion tactics
Faked documents pushed on fringe websites and social media, similar to operation uncovered in June 2019

The DFRLab has uncovered an influence operation using forged documents and a network of fake online accounts to undermine the credibility of the Latvian government. Similar to an operation identified by the lab in June, the effort carries the hallmarks of Russian intelligence services, though no link between the two operations was apparent.
In the newly uncovered operation, one-off Reddit accounts shared an article from a German self-publishing platform that featured two forged letters suggesting that Latvia would allocate €60 million for establishing additional cybersecurity units. The article used the letters as evidence to suggest that the Latvian government is conducting unnecessary spending in the information security sector while neglecting social programs.
In June 2019, the DFRLab uncovered a suspected Russian intelligence operation, dubbed “Secondary Infektion,” that employed the same strategy: using one-off burner accounts on self-publishing platforms to promote forged letters. While the strategy behind Secondary Infektion seemed intent on undermining Western foreign policy objectives, its execution was nevertheless fundamentally flawed: coming from one-off accounts, the reach of the faked documents was relatively limited. In other words, preexisting user accounts — if properly built and maintained — would notionally have a ready and waiting audience to receive and possibly amplify a faked document; by using a burner account, no such audience existed in this case.
In its Secondary Infektion report, the DFRLab identified seven cases that shared the strategy. Later, on November 13, a forged letter appeared that suggested Greenland is striving for independence from Denmark and greater cooperation with the United States. Most recently, in early December, Graphika released report detailing leaked documents, first posted online on October 21, that appeared to have been real but the spread of which closely mirrored that of the Secondary Infektion forgeries.
The operators of the accounts uncovered in Secondary Infektion — and more specifically the posts they published — demonstrated characteristics that allowed the DFRLab to get to a confident assessment that the perpetrators were likely Russian in origin. While the operation targeting Latvia resembles Secondary Infektion in structure, publishing strategy, and amplification pattern, there is no direct evidence that the two are related nor that the operators were Russian. That said, because of the similarities and the target country being a favorite for Russian interference, Russian actors are the most likely culprit for this particular campaign.
The local context
A week before the letters appeared, on November 25, the Latvian government allocated €60 million to increase the salary of medical workers. The government had previously promised an increase of twice that amount. As the annual budget approval process approached, medical workers gathered in front of the Latvian parliament to protest. On November 27, they demanded the dissolution of parliament and the resignation of the minister of health.
At the same time, a group of fringe activists, some of whom have previously amplified Kremlin narratives, such as advocating for Latvia’s withdrawal from NATO, started a petition also calling for the dissolution of parliament. In a short period of time, the petition garnered 20 percent of the 150,000 signatures required to initiate the referendum, and activists have a year to collect the remaining signatures.
Forged letters targeting Latvia
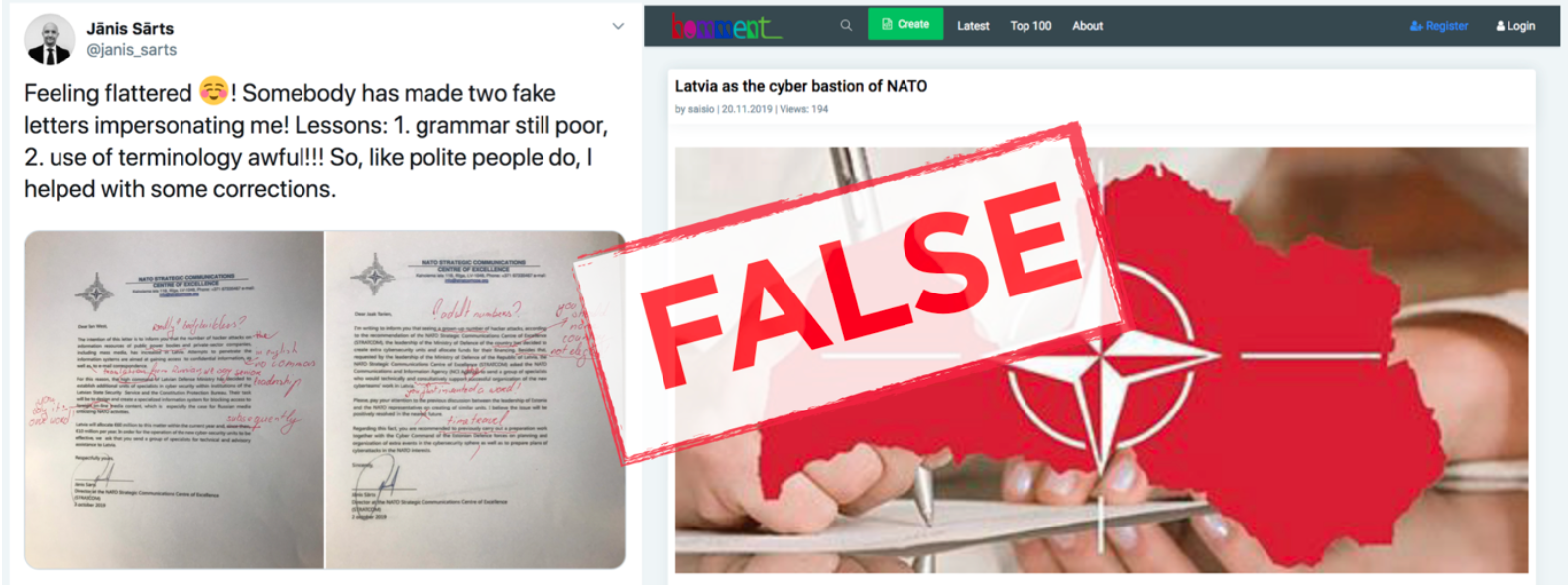
On November 20, 2019 a user named “saisio” published an article on Homment.com, a German self-publishing site, with two forged letters bearing the signature of Janis Sarts, the Director of the NATO Strategic Communications Centre of Excellence (NATO Stratcom COE). The letters claimed that Latvia had decided to allocate funds to establish “extra cybersecurity units.” The article interpreted the letters as evidence that “Latvian leadership is spending enormous funds to provide its informational security instead of supporting the public sphere.”
The author did not mention the medical workers’ protest or demands, but the amount of money — €60 million — that the forged letters claimed the government was willing to allocate to cybersecurity units was exactly the amount of shortfall from its initial promise to increase medical worker compensation. The figure may have been chosen to suggest that the government had lied about having insufficient funds to increase medical workers’ salaries, or possibly that it had reallocated the salaries toward cybersecurity.

One of the letters was addressed to Ian West, Head of the NATO Communications and Information Agency’s Cyber Security Service Line, while the other was addressed to Jaak Tarien, the Director of the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE). Google search results did not return result for any other article by “saisio” on Homment.com.
The reaction in Latvia
A day later, Janis Sarts tweeted in English and in Latvian that the two letters were forged, providing redlined versions highlighting grammar and terminology errors.
Feeling flattered ☺️! Somebody has made two fake letters impersonating me! Lessons: 1. grammar still poor, 2. use of terminology awful!!! So, like polite people do, I helped with some corrections. pic.twitter.com/NXVeJc45D5
— Jānis Sārts (@janis_sarts) November 21, 2019
In an exchange with another Twitter user, Sarts suggested that the terminology appeared to have been directly translated from Russian. He pointed out that the term “high command,” for example, was a direct translation of the Russian term “vyshie komandovanie (высшее командование),” which describes the top of an organizational hierarchy.
The spread online
Saisio’s article with the forged letters garnered just two engagements on Reddit, according to Buzzumo, online content analysis tool. Two Reddit accounts, “saisioEU” and “santalaa,” posted it in the Reddit communities “r/Europe” and “r/Latvia,” respectively.

SaisioEU’s post on Reddit garnered four comments and two upvotes, and was eventually removed. Santalaa’s post remained on Reddit and garnered nine comments.
Three out of the 13 comments on both posts combined seemed to believe the premise of the article.

Conclusion
The use of burner accounts — anonymous accounts that posted the article once and never posted again — demonstrated a high degree of operational security (OPSEC): efforts made to keep activity covert. The attention to OPSEC was one of the forensic clues the DFRLab used to identify Secondary Infektion as emanating from a well-resourced and sophisticated actor, such as a state intelligence agency. Paradoxically, high OPSEC can limit an information operation’s success, as one-off accounts offer little opportunity to build an audience prior to deploying misleading or inauthentic material. The lack of a built-in audience, in turn, hampers the operation’s ability to gain traction.
Forged documents featured in six of the eight suspected Russian intelligence campaigns the DFRLab has previously identified. While the open-source evidence did not conclusively point to a single actor this instance, the underlying tactics were similar to Secondary Infektion and the target country, Latvia, was one in whose internal affairs Russia is infamous for meddling.
Follow along on Twitter for more in-depth analysis from our #DigitalSherlocks.

