New York City’s open-source “cop watch”
How a group of civilian volunteers monitor police activity using open-source methods.
New York City’s open-source “cop watch”
Share this story

As police employed often severe crowd control tactics in response to the protests stemming from the police killing of George Floyd, a group of New Yorkers came together to monitor, document, and distribute information about police activity in their neighborhoods using open-source techniques. Amassing nearly 4,500 tweets since the account started posting in May, @NYPDPoliceRadio provides situational awareness for protesters and community organizers by monitoring publicly available police radio feeds.
Community monitoring of police activity, sometimes called a “cop watch,” is an example of sousveillance: a form of citizen-intelligence gathering that is decentralized and directed toward making authority more accountable. By monitoring the conduct of law enforcement, citizens work in an informal way to hold police to the same legal standards police are intended to enforce and transparency measures intended to limit overreach. In the case of @NYPDPoliceRadio, activists have taken sousveillance to the airwaves, providing protesters with live tweets of police activity. Such efforts, however, may also provide awareness of police movement to those intent on criminal activity, enabling them to better evade interdiction.
As protests began in cities around the United States, New Yorkers monitoring police activity congregated around the hashtag #NYCScannerDuty, eventually agreeing to combine their efforts. Since then, @NYPDPoliceRadio has grown to a decentralized group of about 40 people who work in shifts transcribing, tweeting, and mapping police movement across New York’s five boroughs.
The DFRLab reached out to @NYPDPoliceRadio to better understand the pop-up open-source community, agreeing to their request that they remain anonymous.
Open-source law enforcement monitoring
Although the New York Police Department (NYPD) broadcasts its communications on well-known and unencrypted channels, the hardware and know-how required to listen to radio communications go beyond the capabilities of the average open-source researcher, protester, or activist.
To circumvent hardware requirements, early members of the @NYPDPoliceRadio group turned to websites already hosting streams of radio transmissions. These sites serve as hubs for crowd-sourced radio feeds and rely predominantly on radio enthusiasts and hobbyists to volunteer their hardware in order to upload radio transmissions for audiences online.
One such site is Broadcastify, which hosts community-sourced transmissions pertaining to public safety, aviation, rail, marine, weather, and amateur radios. @NYPDPoliceRadio initially monitored and reported on police communications hosted on Broadcastify. As protests in New York City developed, however, members of the @NYPDPoliceRadio group identified outages of NYPD live streams posted to Broadcastify.
It is legal to monitor unencrypted airwaves, but contributors to Broadcastify’s catalogue of NYPD live feeds began to pull their streams. One independent user, who consistently streamed radio traffic of the NYPD Special Operations Division, stopped uploading the feeds “due to possible groups using this feed for nefarious purposes” — this removal was entirely at the uploaders discretion and, according to the DFRLab’s understanding, not by Broadcastify nor the NYPD.

The user did provide a short explanation as to the feed’s removal, saying:
Due to the ongoing unrest in the 5 boroughs, this feed will remain offline. Due to possible groups using this feed for nefarious purposes I have chosen this course of action.
It is unclear, outside of the brief explanation, to what “nefarious purposes” the Broadcastify user was referring. It is possible that they mistook the peaceful assembly that comprised the vast majority of the George Floyd protests as “nefarious,” or, perhaps, the user believed the increased attention the feed was receiving might also draw in an audience that included people with intent to undertake actual criminal activities.
Going DIY
In keeping with open source and within their budgets, the @NYPDPoliceRadio group adjusted their tactics to recover the channels lost from Broadcastify users, this time deploying their own radios, feeds, and website. Using cheap, $30 Software Defined Radios (SDR) coupled with $30-$40 Raspberry Pi computers, streams of the radio transmissions were routed to an Icecast streaming media server for broader distribution. Capable of capturing multiple channels on a single SDR + Raspberry Pi unit, the simple hardware was matched with a Web audio API to integrate seamlessly with a custom web interface.
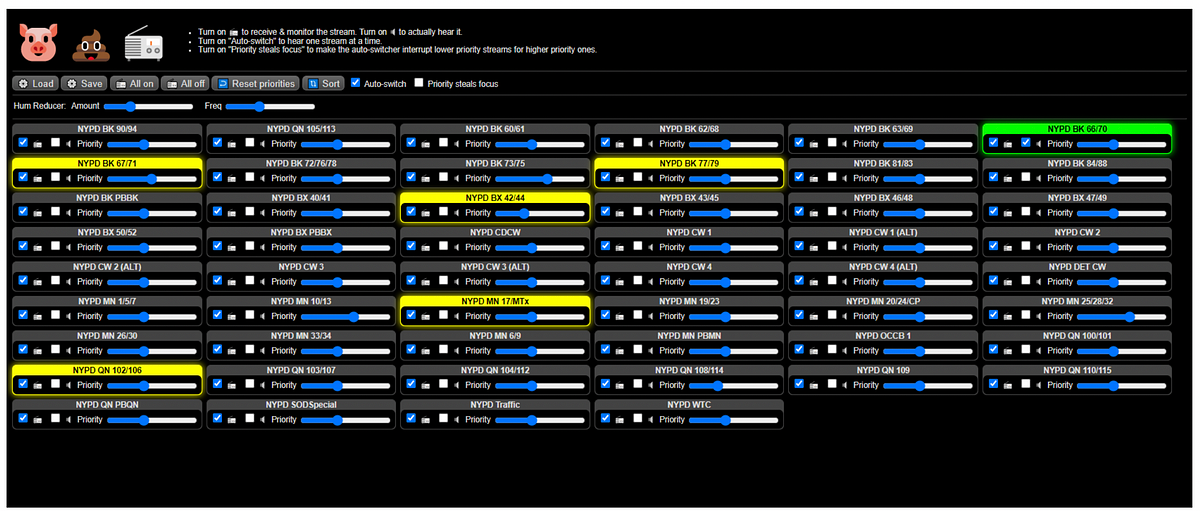
Working in shifts, contributors to @NYPDPoliceRadio signed up for timeslots to monitor radio communications. During times of peak activity, the team was said to have had around six volunteers listening to more than six channels concurrently to keep up with the torrent of radio traffic. At its current pace, the team has averaged 179 tweets per day in the 25 days since the account opened.
Once instances were transcribed and posted to Twitter, they were plotted on the group’s associated map interface to provide users with a bird’s-eye view of police operations related to social justice protests.
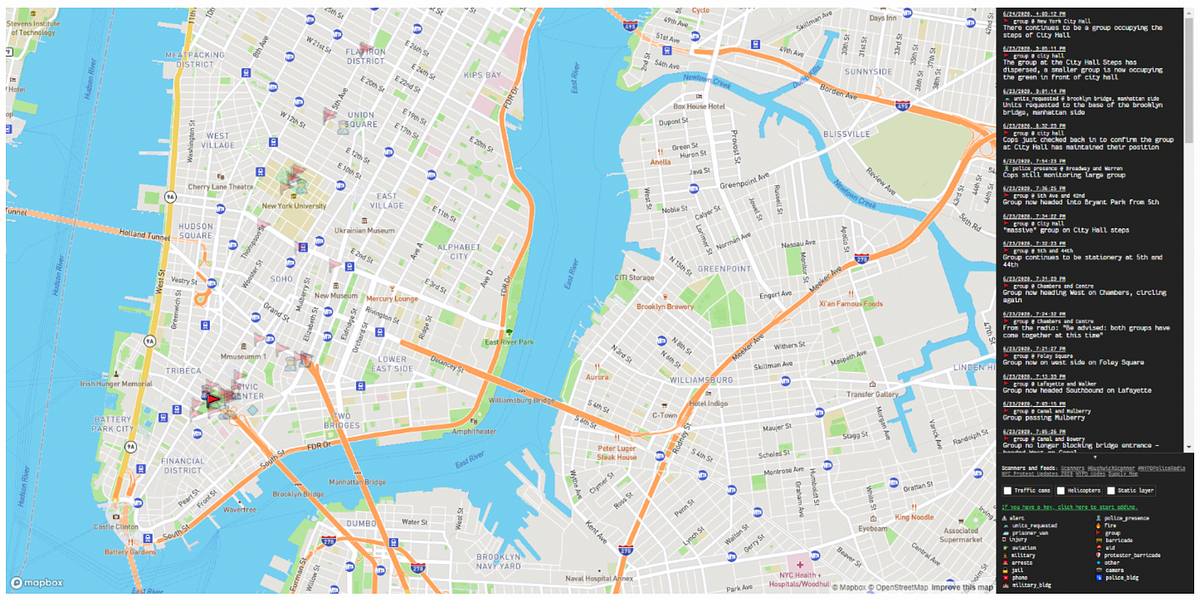
The @NYPDPoliceRadio group also uploaded audio files of police radio traffic to a newly created SoundCloud account. Without any recourse for civilians to access historic police communications, archives posted to SoundCloud serve as a unique and open-source history of the protests in New York City, which had drawn a combined total of 3,513 plays at the time of analysis.
Twitter activity
Of the 3,200 tweets made between June 3, 2020, and June 25, 2020 (timespan bound by limitations of the unpaid Twitonomy service), @NYPDPoliceRadio has been retweeted 2,078 times and amassed 5,642 favorites. Often, the group’s efforts continued until the early hours of the morning, as shown by the group’s twitter activity.
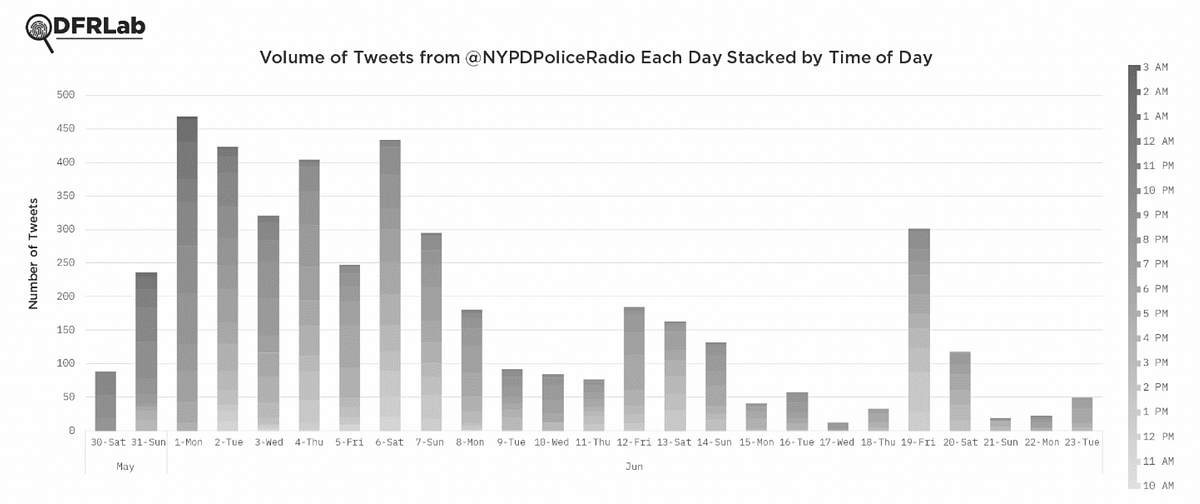
@NYPDPoliceRadio is not the first to monitor police via open source, but it has received considerable engagement from the activist community as a resource. According to organizers, activists in other cities have reached out to @NYPDPoliceRadio group for guidance in launching their own open-source “cop watch” operations.
Some on the team, however, predict difficulties for future radio eavesdropping efforts as encrypted police radios see increased usage in departments around the United States. Many municipalities have already begun phasing in encryption on police radio communications in the interest of officers’ safety and in opposition to criminal or terrorist efforts to evade law enforcement.
A push toward the commercialization of police communications technology, such as AT&T’s FirstNet and Verizon First Responder, raise increased concern that police communications as a service may leverage successful law enforcement activities on third-party telecom infrastructure — a departure from simple and robust radio communications. That said, police have already been cited using cellphones in place of police radios, rendering the communications inaccessible to both civilians as well as the officers own police departments.
The group fears that, without this civilian-led monitoring effort on police communications, incidents of law enforcement misconduct may go undocumented, despite the risk that people actually intent on criminal mischief might also use the same information to avoid the police, and that it will therefore become more difficult to hold police accountable for their actions.
Until then, @NYTPoliceRadio plans to continue its operations in New York City. In the words of one NYPDPoliceRadio contributor, “People appreciate live coverage of cops and protest activity; it can be difficult to follow what is happening on the fly without this kind of service. It means a lot to me to see people thank us during our nightly sign off — folks who followed us during the day to contribute to the movement.”
Cite this case study:
Max Rizzuto, “New York City’s open-source ‘cop watch’,” Digital Forensic Research Lab (DFRLab), July 2, 2020, https://dfrlab.org/2020/07/02/new-york-citys-open-source-cop-watch/.

