Lukashenka’s regime confused about Belarus Cyber Partisans’ activity
Government reactions to attacks by the
Lukashenka’s regime confused about Belarus Cyber Partisans’ activity

Government reactions to attacks by the Belarus Cyber Partisans marred by defensiveness, contradictions and ignorance

Alyaksandr Lukashenka’s regime is lacking a unified and effective approach to counter activities by Belarus Cyber Partisans, an anonymous decentralized community of Belarus IT specialists who are fighting Lukashenka’s control over the country.
As of October 1, 2020, the Cyber Partisans had carried out at least 15 publicly known attacks on Belarus state-owned web resources. At first the group changed websites’ content for public awareness, but later started interfering with tax collection services, tenders and other online state infrastructure critical for the regime. In response, Lukashenka’s representatives feigned ignorance of the attacks, but eventually took a more defensive position by issuing an infographic for state officials on how to avoid phishing attacks, as well as instructions for programmers and developers at state enterprises on how to protect websites.
Political crisis in Belarus started right after presidential election on August 9, 2020. The lopsided vote count, the Belarusian people’s distrust in its veracity, and allegations of electoral fraud have led to ongoing mass protests around the country. Every week on Saturday women go on streets, while on Sundays general crowds of protesters gather across Belarus. In September, following the oppression of the Belarus IT sector by internet black outs and investigations into Belarus start-ups, the IT community joined the protests online.
On September 2, the office of IT company PandaDoc was searched as company founder Mikita Mikado collected money to financially support former law enforcement officers who resigned in protest from the government. The company was accused of “theft on an especially large scale,” and four of its employees were arrested. Mikado decided to pause the project, but the Belarus Solidarity Foundation (BYSOL) continues his work.
Cyber Partisans attack
Belarus Cyber Partisans began their activities in early September 2020. Their first publicly known hack, which took place on September 2, was the change of the front page of Belarusian presidency website to an image of a silly looking army general and the white-red-white flag.
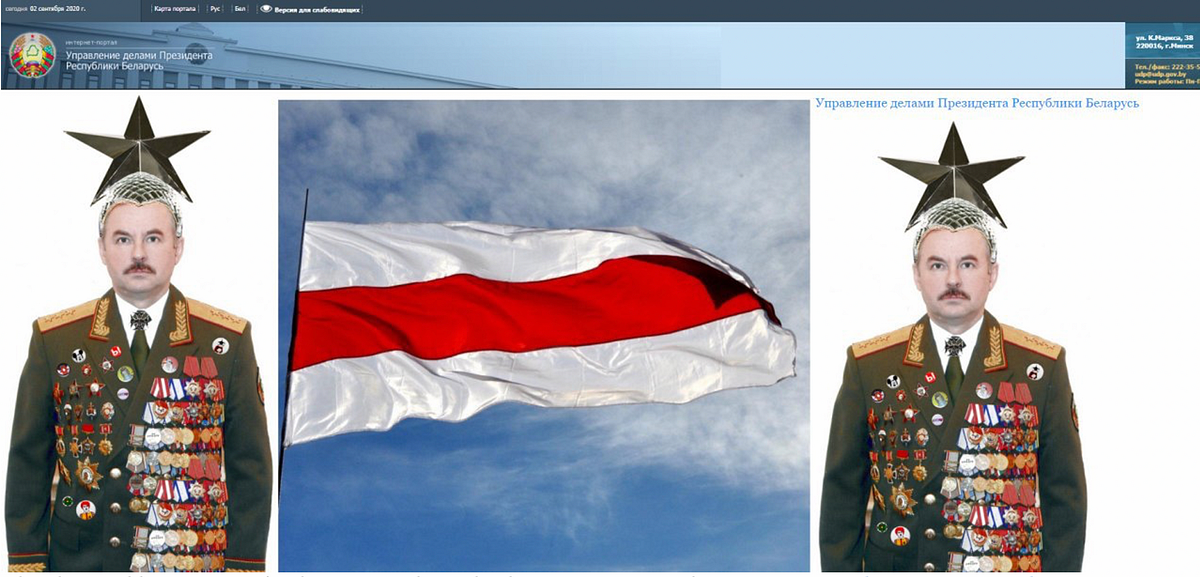
The group carried out similar attacks on the Belarus Chamber of Commerce’s web page (September 5) and the Belarus Lottery site on September 12 to welcome Sviatlana Tsikhanouskaya, the Belarus presidential opposition candidate, currently living in exile.
Meanwhile, on September 3, the Cyber Partisans added Lukashenka and Interior Minister Yury Karayev to the ministry website’s most-wanted list, for “war crimes against the Belarus people.” They also carried out multiple attacks on the Interior Ministry Academy website by changing its homepage on September 4, September 9 and September 24. The ministry took down its own page to “save previously published materials.” The DFRLab could not access either website on October 1, 2020.
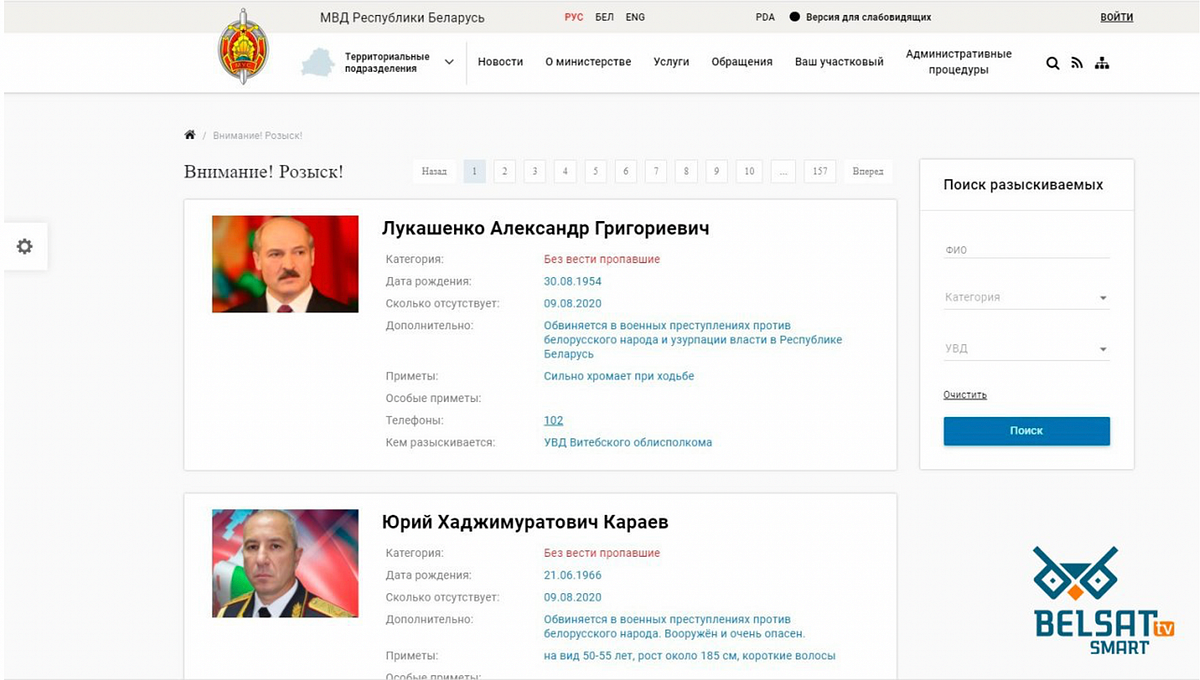
The most impactful activity by the Cyber Partisans was the leak of Belarus law enforcement officers’ personal data. The group shared the list of personal data with NEXTA Live, the biggest Russian-language Telegram channel about Belarus. On September 11, NEXTA Live threatened to publish the list if law enforcement officers continued to detain peaceful protesters violently. On September 19, NEXTA Live published the list. The next day, Yaroslav Lyhachevsky, the representative of Belarus Solidarity Fund BYSOL told independent Russian TV channel Dozhd that about 200 law enforcement officers resigned and applied to get an aid from the fund. On September 21, Interior Ministry Press Secretary Olga Chemodanova told a Russian state TV channel that the published list is four years old and the leak “did not negatively affect operations by the Ministry of Interior.”
Later on September 28, anonymous pro-Lukashenka hackers attacked the anti-Lukashenka media outlet KYKY.org regarding the law enforcement data leak. They left an audio message on the site, saying:
We are Lukashenka’s supporters. We are aware of your development of a facial recognition system that allows de-anonimizing law enforcement officers, as well as hacking their accounts. The enforcement officers earned this money honestly, dispersing the crowd of careless protesters, so we do not accept such an outrage and want to restore justice. Know, Cyber Partisans, you are not protected either! And we are not afraid of you. See you.
The face recognition system referenced in the message is in an early demonstration stage and reportedly did not work as of yet.
Below is a timeline of Belarus Cyber Partisans’ activities and responses by Belarus authorities. It includes the most recent hack of a live online broadcast on two Belarusian state-owned TV channels. The TV program was interrupted by videos showing OMON state security forces brutality detaining protesters.
Lukashenka’s regime pleads ignorance
To date, the response by Lukashenka’s regime representatives has been somewhat passive. Only recently, on September 30, the interior ministry published a statement about email phishing attempts and instructions for state officials to avoid opening suspicious emails and attachments.
On September 12, the Cyber Partisans threatened to take down Belarusian tax collection online infrastructure. At first a representative from the tax collection authority told KYKY.org that the “site works brilliantly.” The next day, their press secretary confirmed that the users of online tax collection services were experiencing problems, but had resolved the issue. Apart from that acknowledgement, Belarusian authorities did not release an official response to the apparent attack.
The pattern continued when the interior ministry denied their websites experienced significant harm, despite the embarrassing changes made to the sites. And no statement was issued in response to the hacker takedown of the state tenders’ website, nor the website of Belarusian Universal Commodity Exchange in response to a recent tender for 200 armor vests for the Minsk police, either.
Pro-Lukashenka Telegram channels lack unified approach
Mixed messages about the Cyber Partisans appeared on pro-Lukashenka Telegram channels the DFRLab covered previously. The channels contradicted themselves by describing the Cyber Partisans both as terrorists and school kids, unable to decide whether they were dangerous or unskilled amateurs.
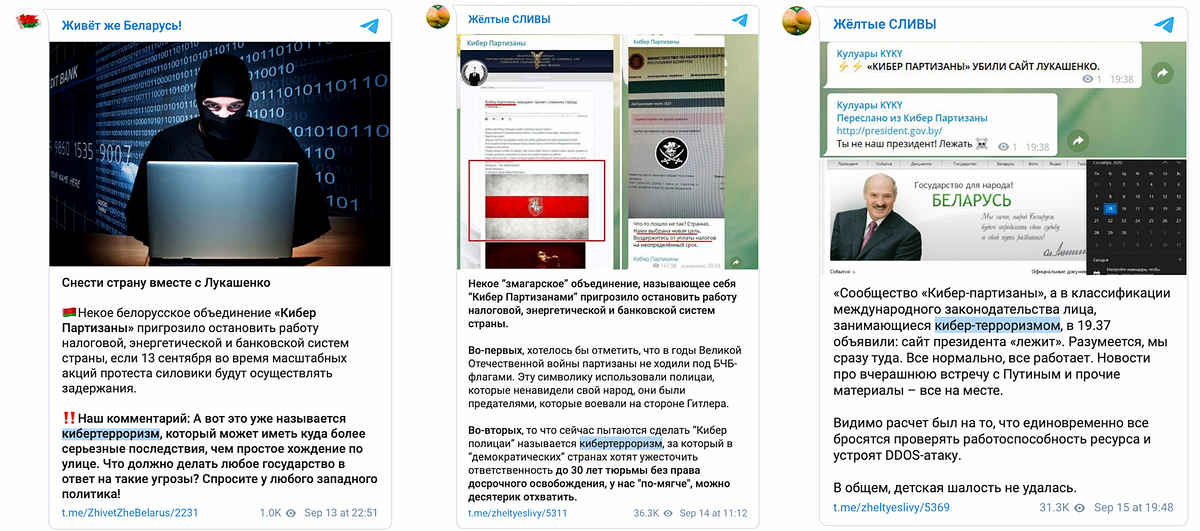
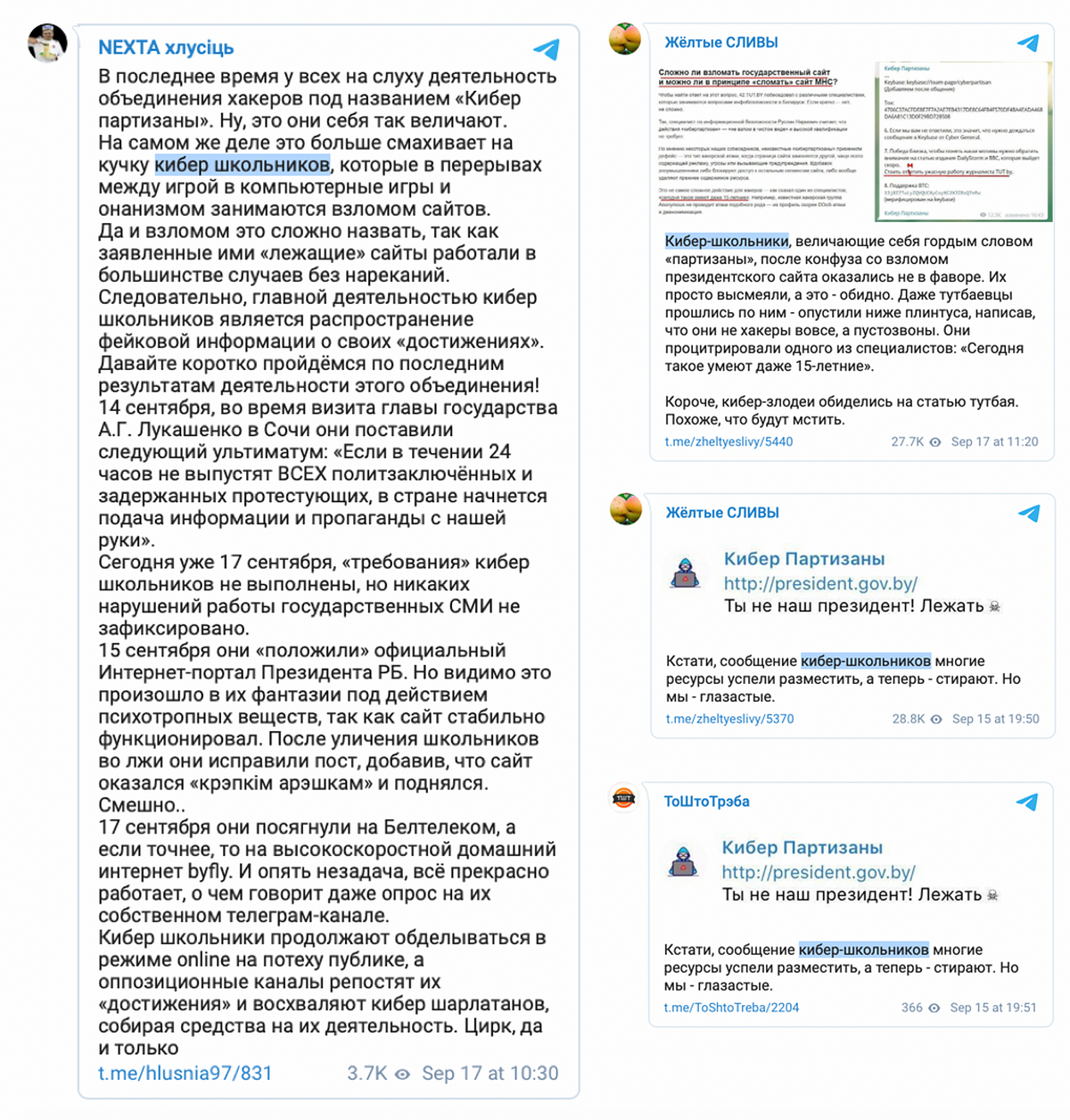
Meanwhile, pro-Lukashenka Telegram channels Belaruskaya Kuhnya and #InfoSpecNaz Belarusii amplified a third narrative in the form of a rumor that the Cyber Partisans were instead employees of NATO cyber centers carrying out information and psychological attacks.
Most recently, pro-Lukashenka Telegram channels shared instructions for “fighting with cyber-zmagaryki,” meaning Cyber Partisans. The posts targeted “programmers and developers at Belarus state enterprises” but the instructions were specific for system administrators.
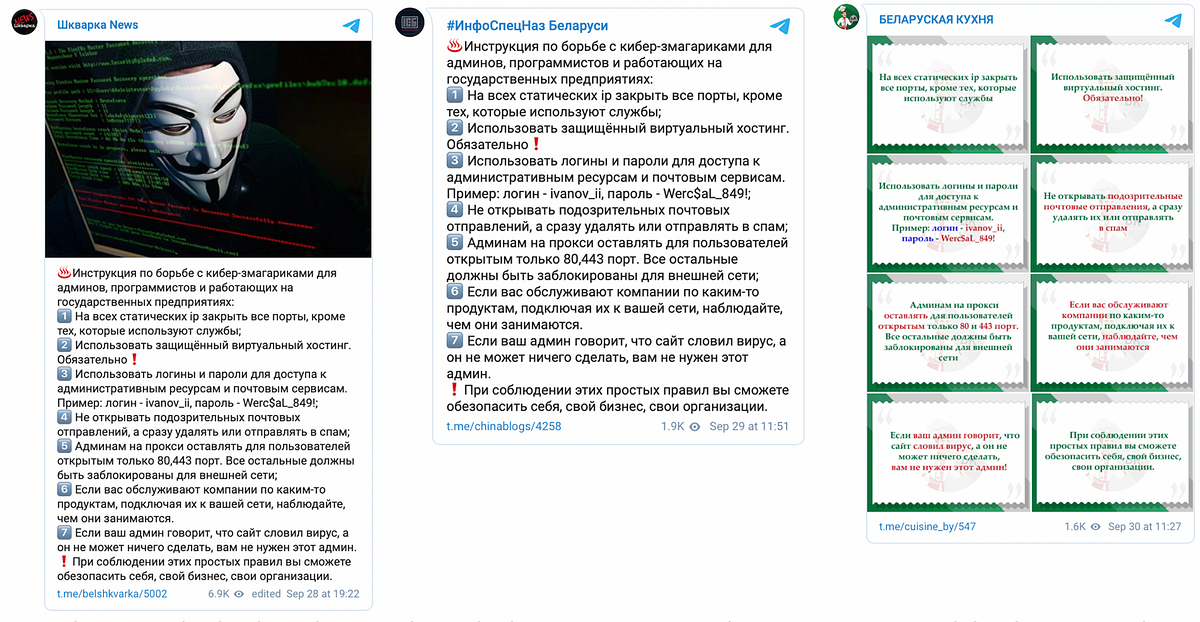
Lukashenka’s regime initially cast itself as ignorant of the Cyber Partisans’ activities, but the most recent announcements about increased cyber-attacks on state web facilities, the counter-cyber-attacks on an anti-Lukashenka media outlet, and contradicting rhetoric on pro-Lukashenka Telegram channels, suggest that regime is still figuring out how to best respond to the cyber-enabled side of the Belarusian protest movement.
Nika Aleksejeva is a Research Associate, Baltics, with the Digital Forensic Research Lab.
Follow along for more in-depth analysis from our #DigitalSherlocks.

