Malicious actors carried out operation after U.S. company announced plans to invest in Poland’s nuclear power program

By Givi Gigitashvili
A cyber-enabled information operation aimed at sowing fear about a non-existent radioactive threat targeted Polish government websites in March 2021, in the latest example of a hybrid disinformation campaign targeting the country. On March 17, hackers broke into two Polish government websites and planted false information about nuclear waste leak in Lithuania, which allegedly endangered people’s lives in northern Poland. Polish authorities acknowledged the fact that the websites were targeted by malicious actors, but they have not attributed it to anyone specific. The latest disinformation operation is similar to previous campaigns against Poland and Baltic countries that combined elements of a cyberattack with a disinformation campaign.
The information operation consisted of several steps. First, the hackers created a clone website that resembled the Lithuanian State Nuclear Power Safety Inspectorate (VATESI) website. Next, they broke into the websites of the Polish National Atomic Energy Agency and the European Healthcare Funds (administered by the Polish Ministry of Healthcare), planting fabricated content about a possible radiological threat, citing the VATESI clone website as a source. Subsequently, the attackers took over the Twitter account of Polish political analyst Marek Budzisz and used it to spread disinformation about the alleged radioactive accident. The hackers also compromised the Facebook account of a Polish politician Andrzej Rochmiński and Facebook pages belonging to the Polish ruling party, Law and Justice (PiS), which they then used to disseminate false information about the radiological danger in multiple Facebook groups.
Worth noting is the timing of this information operation. On March 3, 2021, the U.S.-Polish civil nuclear agreement entered into force. Under the deal, the two countries committed to preparing a joint report on the implementation of Poland’s nuclear power program. Poland intends to build six nuclear power units by 2043. On March, 15, 2021, the U.S.-based Westinghouse Electric Company publicly announced its plan to invest in construction of a nuclear plant in Poland. Currently, Westinghouse is preparing the technical part of the nuclear plant construction offer using funding from the U.S. Trade and Development Agency. Given this context, the possible aim of the hackers may have been to create fear or skepticism over Poland’s nuclear power program. Stanislaw Zaryn, a spokesperson for Poland’s Minister-Special Services Coordinator, told the Associated Press that “the whole story looked like a typical Russian attempt” to create suspicion. However, Polish authorities have not officially attributed this information operation to any specific actor yet.
Creation of the VATESI clone website
On the clone website resembling the Lithuanian State Nuclear Power Safety Inspectorate (VATESI), the hackers posted an announcement claiming that a disaster had taken place at the Lithuanian Maišiagala radioactive waste storage facility, resulting in a dramatic increase of tritium concentration in precipitation, soil, and groundwater. The announcement also asserted that tritium was the most mobile and radioactive isotope of hydrogen and that it could cause cancer and mutations, and advised citizens to abstain from using water due to the radioactive contamination. VATESI administration immediately denied this information and stated, “there was no any unusual event at Lithuanian nuclear facilities and no changes of radiation background in Lithuania were indicated.”
The hackers may have targeted the Maišiagala facility because of the ongoing discussion in Lithuania about its decommissioning. On March 12, 2021, VATESI announced that it had reviewed Maišiagala facility safety assessment documents and concluded that planned decommissioning activities of the facility comply with safety standards. Consequently, VATESI prepared a draft decision to transport radioactive waste from the Maišiagala facility to the Ignalina Nuclear power plant.
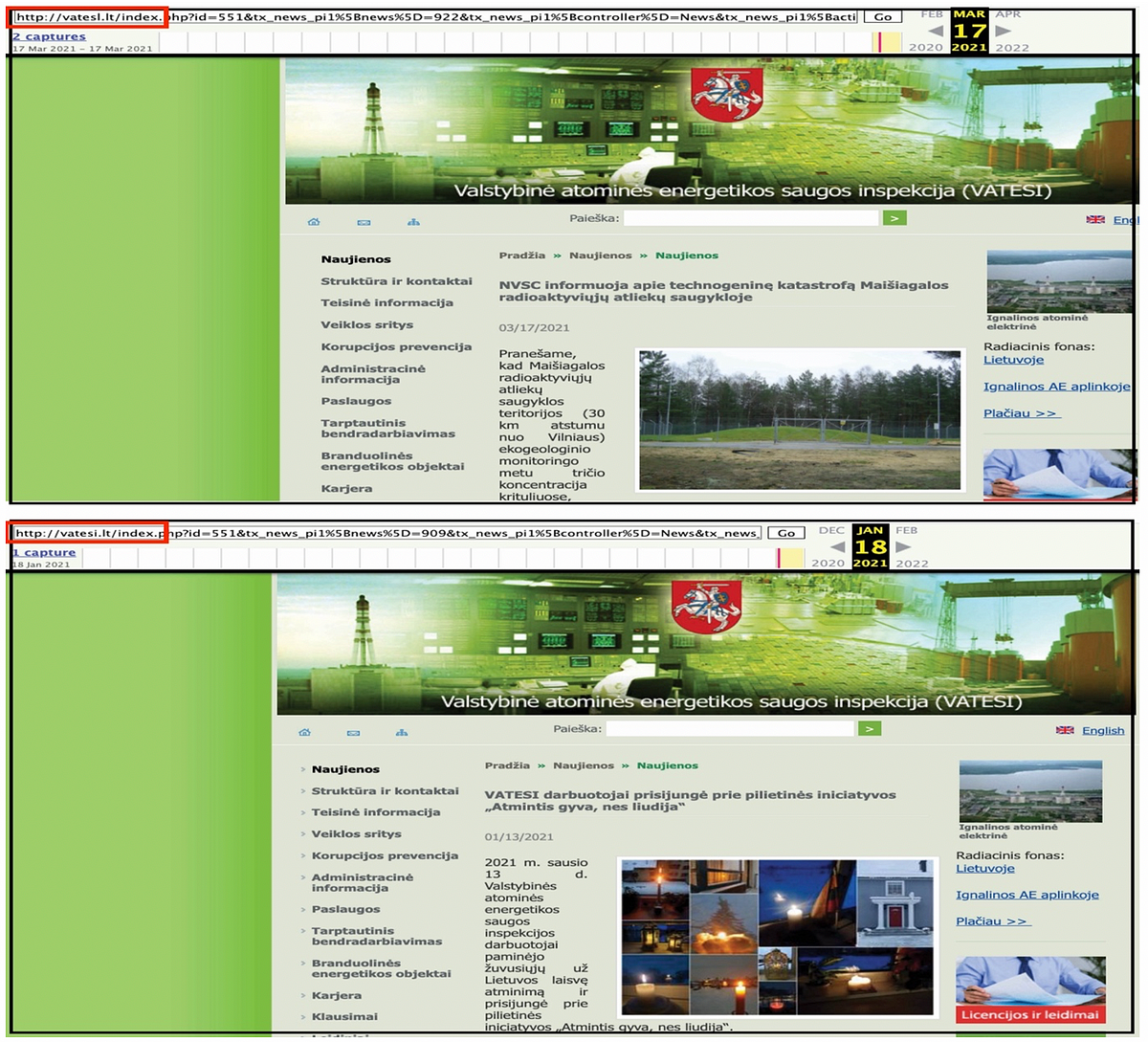
The DFRLab found that the hackers copied the majority of articles posted on the official VATESI website to a clone website in order to make the latter look legitimate. Archived pages of the website from the Wayback Machine showed that once visitors would click to open articles stolen and copied from VATESI, they would be automatically directed to the official VATESI website. The domain of the official VATESI website is Vatesi.lt, and hackers changed just one letter in the URL address — an “i” to an “l” — to create the Vatesl.lt clone website, before posting the fabricated announcement on its home page.
A Google reverse image search showed that a photo was used in the fabricated announcement was most probably taken from a Krašto žinios news article about the Maišiagala Radioactive Waste Storage Facility, published on March 17, 2021. As for the false announcement’s text, the DFRLab found that the majority of it was copied from various Lithuanian websites and it seemed to be written by someone with a decent grasp of the Lithuanian language.
Website hacking
Even though the hackers created a clone of the Lithuanian state agency website, their operation targeted Poland. After the first stage of their operation — creating a clone website with a fake disaster announcement — the hackers broke into the website of the Polish National Atomic Energy Agency (PAA), the state agency responsible for nuclear safety and radiological protection, and posted another fake announcement about the radiological hazard caused by the supposed tritium contamination accident in Lithuania. The false announcement on the PAA website asserted that as a result of the leakage of nuclear waste from the radioactive waste repository in Lithuania, radionuclides were released into the atmosphere, leading to significant radiation level increases in northeastern Poland. The hackers linked the fabricated announcement from the VATESI clone website as a source for the false alert on the PAA website.
The PAA has not clarified publicly how the hackers managed to compromise its website and publish the fabricated content. It is possible that hackers harvested user credentials to access the website’s content management system (CMS). Previous operations targeting Poland and the Baltic countries have used similar tactics. In an earlier cyber-enabled operation targeting Poland covered by the DFRLab, hackers compromised the Polish War Studies Academy CMS and replaced content on the website with a fabricated letter. In contrast to this earlier attack, the hackers in this case posted an entirely new article on the site rather than altering an existing one. The DFRLab checked the source code of PAA website and confirmed that the falsified announcement was posted on March 17, 2021.
Apart from the PAA website, the hackers also broke into the website of the European Healthcare Funds in Poland, which is managed by the Ministry of Healthcare and contains information about EU-funded healthcare projects. The fake text planted on this website repeated the false information from the cloned PAA website regarding the alleged accident, and contained additional information on the harmful effects of radiation on human health. The DFRLab found that hackers copied text from an article about radioactive sickness published on Medme.pl, a commercial healthcare and lifestyle website.
Hacking social media accounts of Polish individuals
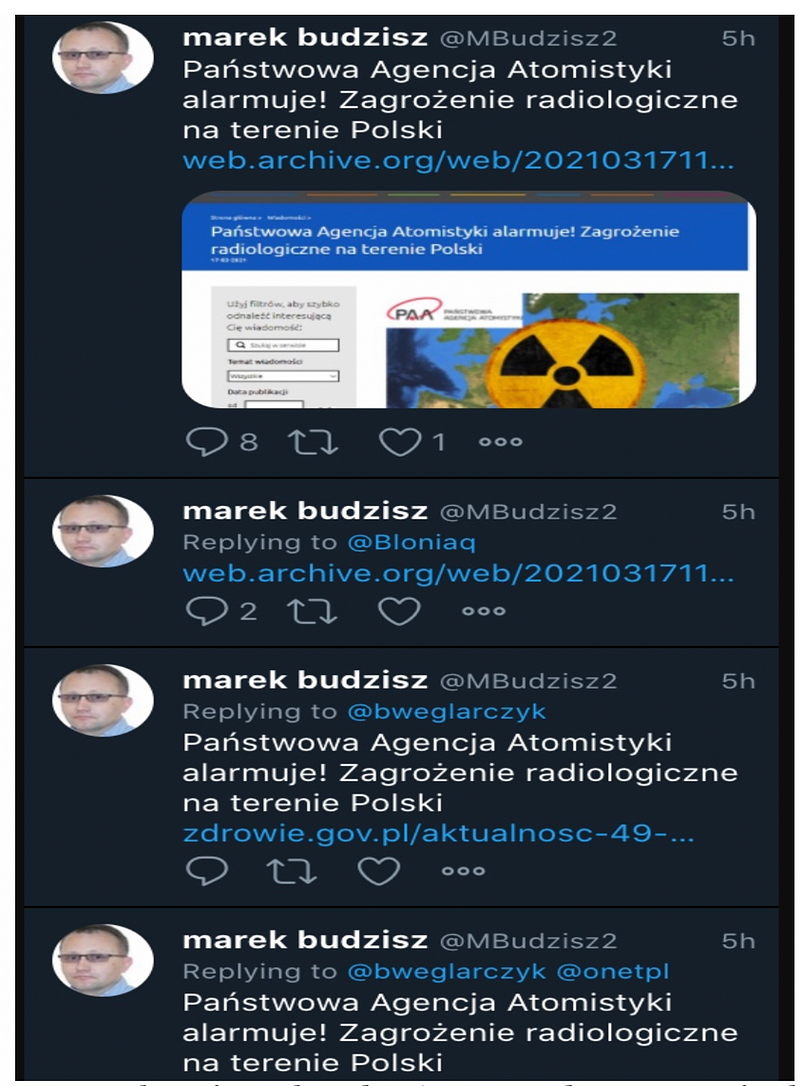
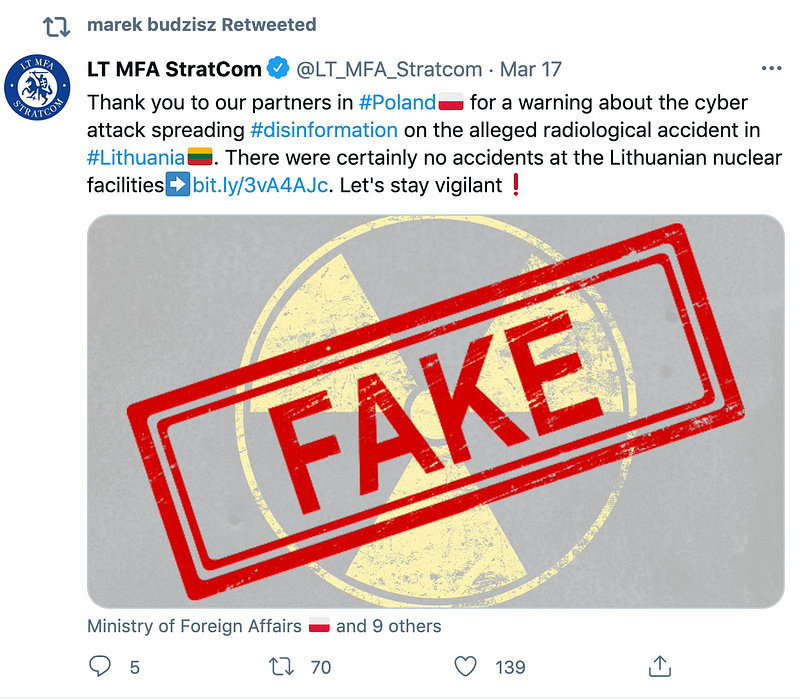
The hackers also took over the Twitter account of a Polish historian and political analyst, Marek Budzisz, who frequently tweets about Russian politics. They used his account to disseminate information about radiological pollution on Polish territory and posted an archived link to the fabricated story on the European Healthcare Fund website. (The false tweets were eventually removed, and Budzisz retweeted a post by Lithuania’s foreign ministry reporting that it had been a hoax.) By compromising Budzisz’s account and promoting the false announcement from it, the hackers were likely trying to expand the audience for the post and giving it an air of legitimacy.
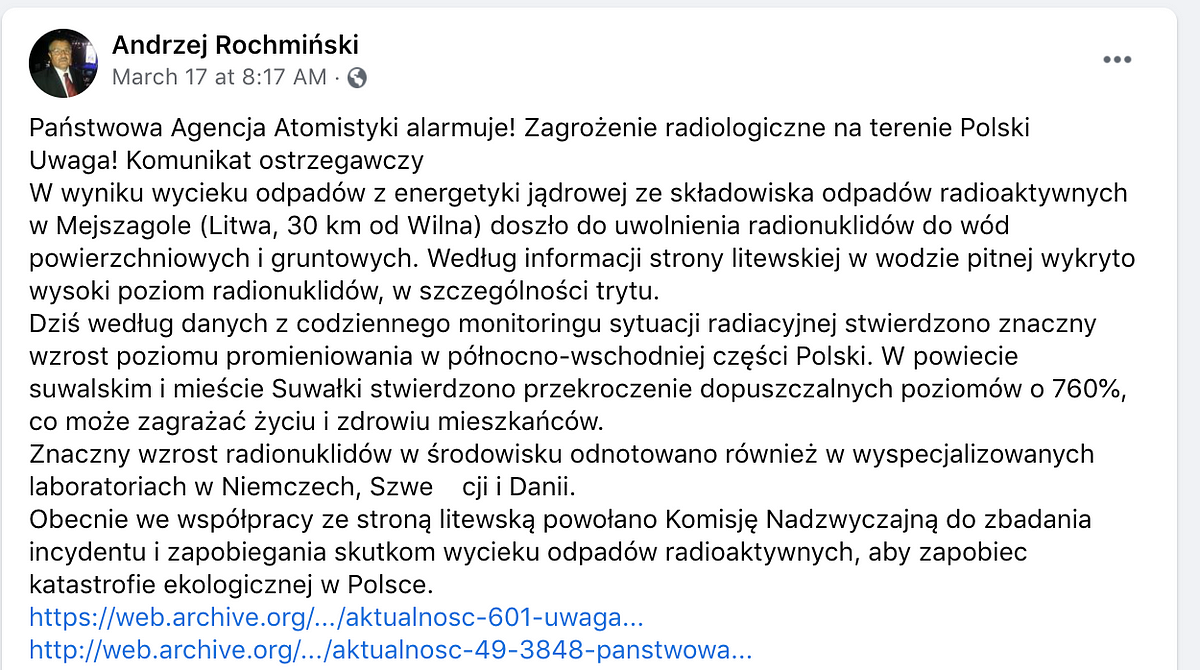
Apart from Budzisz’s account, hackers also hijacked the Facebook account of Andrzej Rochmiński, a Polish politician and member of the ruling Law and Justice party. They posted a false story from his account about the radioactive threat on Polish territory, along with archival links to the hacked PAA website. “State Atomics Agency alerts! Radiological threat in Poland,” it announced. “Attention! Attention! Warning message.” Rochmiński’s account was also used to post the PAA link in several Facebook political groups created for supporters of the Polish president Andrzej Duda.
Finally, hackers also took over the Facebook page of the ruling Law and Justice party regional branch in the city of Krosno Odrzańskie, Poland, and posted links with the fabricated info on the page’s timeline and in several political groups. CrowdTangle analysis showed that both links from the PAA and Zrdowie.gov.pl websites were disseminated in similar groups. However, engagement on these posts was almost close to zero; a third party fact-checker promptly labeled the story as false information, and this label appeared on posts containing the links in the Facebook groups.
The available evidence seems to indicate that this multi-stage operation primarily targeted a Polish audience, even though the false content was originally created in the Lithuanian language. The main objective of the operation appeared to be to sow fear over the risk of radiological disaster in Poland, and more specifically, promote skepticism toward the Polish nuclear power program. Moreover, the operation’s timing indicates that malicious actors may have also intended to obstruct the participation of the United States in the construction of the power plant in Poland, given the recent entry into force of the U.S.-Polish civil nuclear agreement.
Givi Gigitashvili is Research Assistant, Caucasus, with the Digital Forensic Research Lab.
Cite this case study:
Givi Gigitashvili, “Cyber-enabled information operation targets Poland with radiological leak hoax,” Digital Forensic Research Lab (DFRLab), March 31, 2019, https://medium.com/dfrlab/cyber-enabled-information-operation-targets-poland-with-radiological-leak-hoax-28a5b1fb6776.
Follow along for more in-depth analysis from our #DigitalSherlocks.

