High follower accounts leveraged to amplify the reach of a fraudulent crypto scam targeting South African Twitter users

By Jean Le Roux
A cryptocurrency investment scam using a network of Twitter-based sockpuppet accounts is targeting South African users by leveraging fabricated “testimonials” posted on the platform.
Since the start of the year, the network has posted more than 43,000 of these tweets, usually in reply to high follower accounts such as celebrities, news publications and journalists. A rise in the price of bitcoin and other cryptocurrencies since late last year has made cryptocurrencies an attractive lure to get users to part with their cash.
The network consists of two parts. The first layer is scores of sockpuppets that promote these accounts using tweets styled as fake “testimonials.” These accounts portray themselves as South African and are used to give the rest of the network credibility. This consists of several sockpuppet accounts that resemble successful U.S. based forex and cryptocurrency traders.
Despite claiming they hail from the U.S., the DFRLab has identified several links to West African countries, including Nigeria, Uganda, and Tanzania.
When a victim engages with the successful-seeming forex trader networks, they are ushered off-platform to instant messaging apps and websites where they are inevitably prompted to deposit cryptocurrency into the scammers’ cryptocurrency wallet address. These sites are little more than window dressing; despite the impressive looking dashboards, their only functionality is providing the user with the wallet address to complete the “investment.”
The Financial Sector Conduct Authority (FSCA), South Africa’s financial watchdog, issued two warnings against these cryptocurrency exchanges this year alone. On February 4, 2021, the financial regulator issued a press release cautioning South Africans and institutional investors against scams dressed as cryptocurrency investments, and deemed it necessary to issue a follow up on March 18, 2021, noting with concern increasing volumes of crypto assets related losses.
There are strong parallels between the tactics used by these scammers and those deployed by bad actors pushing other forms of disinformation. The accounts were given a veneer of credibility by employing inauthentic and coordinated testimonials, the use of sockpuppet accounts and artificially inflated follower numbers gained through follow-trains. The motive here was financial, but could easily be adapted for political and other forms of disinformation.
Trails from the Crypto
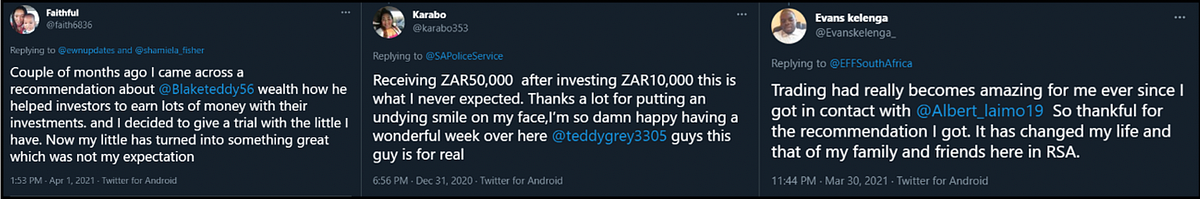
The majority of the tweets in this scam are published by the accounts meant to funneling users towards the crypto trader accounts. They do this using copy/paste testimonials posted in reply to large-following Twitter accounts, such as news publications and celebrities.
To identify the accounts operating in this network, the DFRLab identified three recurring tweets used by various accounts to lure users into the scam. The phrases in these tweets were used to perform keyword searches and create three datasets, one for each keyphrase.
Keyword searches performed on phrases from a selection of these copy/paste tweets found that the scam was active as far back as September 2020, albeit in relatively miniscule volumes. But as the price of Bitcoin increased, so too did the number of tweets fishing for victims.
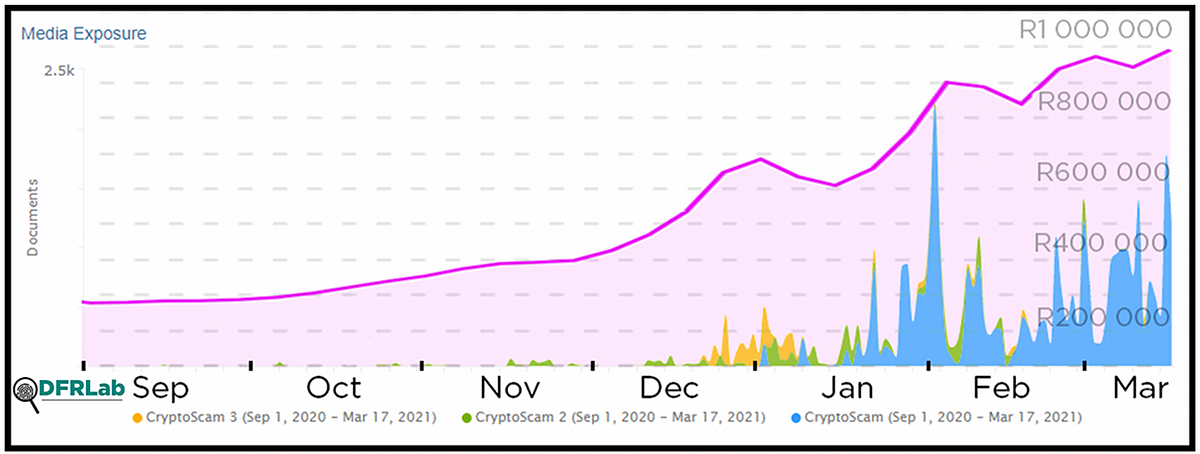
Using Meltwater Explore, the DFRLab identified tweets that contained a significant portion of these phrases within their text. The aggregated data around these results also revealed several flags that marked the network as suspicious.
Firstly, these phrases were used almost exclusively in replies to other users. In the sample of 51,216 tweets made between September 1, 2020 and March 17, 2021 that contained one or more of the phrases, nearly all of its use was in replies to other users. In an organic network, one would expect to find results consisting of a mix of replies, original tweets, quoted tweets and retweets as opposed to an almost-exclusive usage of any of these.
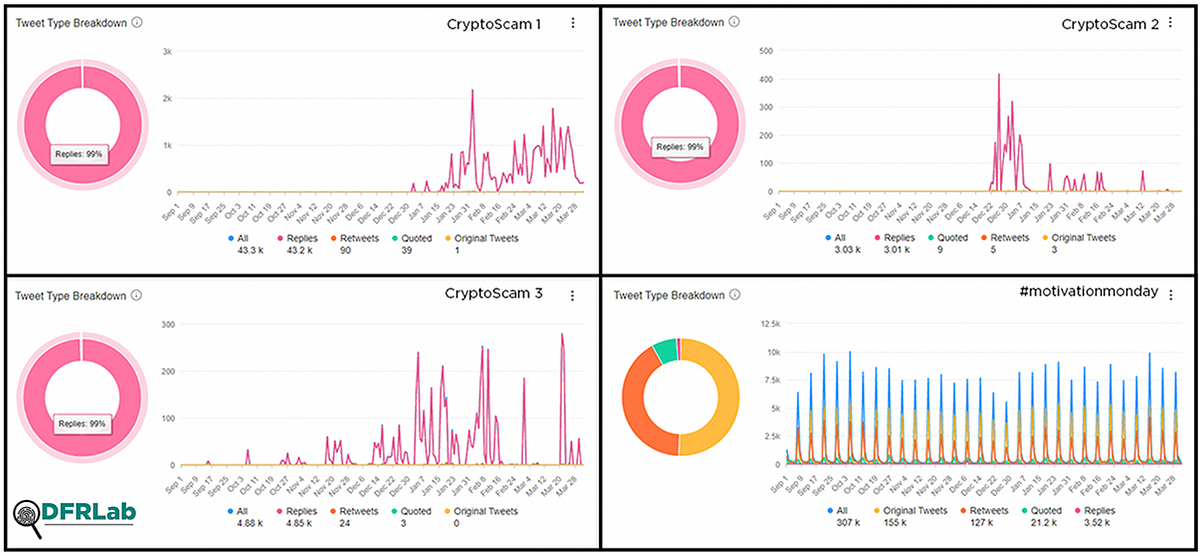
Secondly, a small number of accounts were responsible for a disproportionately large share of tweets using these phrases. Where tweets containing the specific phrases are concentrated among a small number of accounts, it is often indicative of a centralized attempt by those accounts to get their message across.
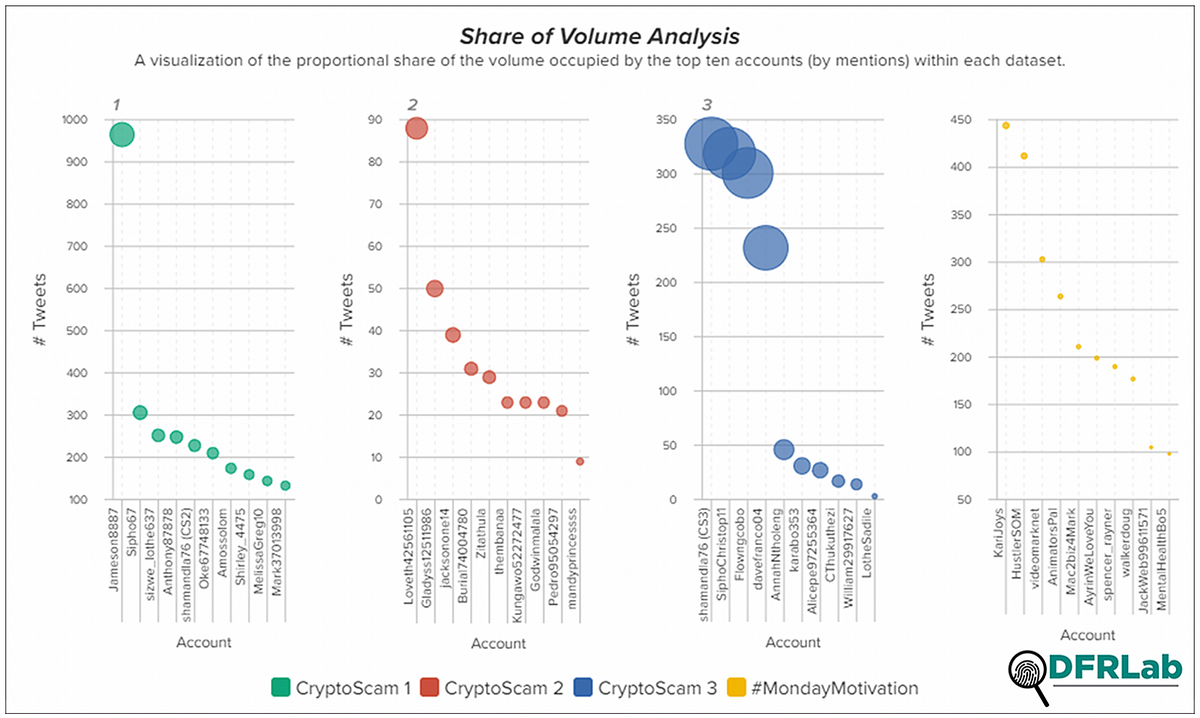
Thirdly, the volumes of tweets pushed out by these accounts were substantial, in some cases registering nearly 300 tweets per day. While it does happen that some users can be exceptionally active, a large number of tweets consisting of near identical content is suspicious.
Lastly, the responses and replies targeted news publications, celebrities, and influencers, all accounts having significant followings. The strategy appears aimed to provide these tweets a wider reach, but also seems somewhat counterproductive since the increased reach also meant more users were calling out the tweets as scams where they saw them.
Included in these spammy copy/paste replies were the accounts handles that the network was trying to amplify, usually alongside a glowing recommendation. Although these accounts changed over time, several of them showed marked similarities in the names they were using. Twitter has taken action against some of these accounts, resulting in their suspension.
The ultimate goal of this part of the network was to corral users to one or more of the forex trader accounts, which then engage the users more directly to get them off-platform for the exchange of funds.
Persona non ex gratia
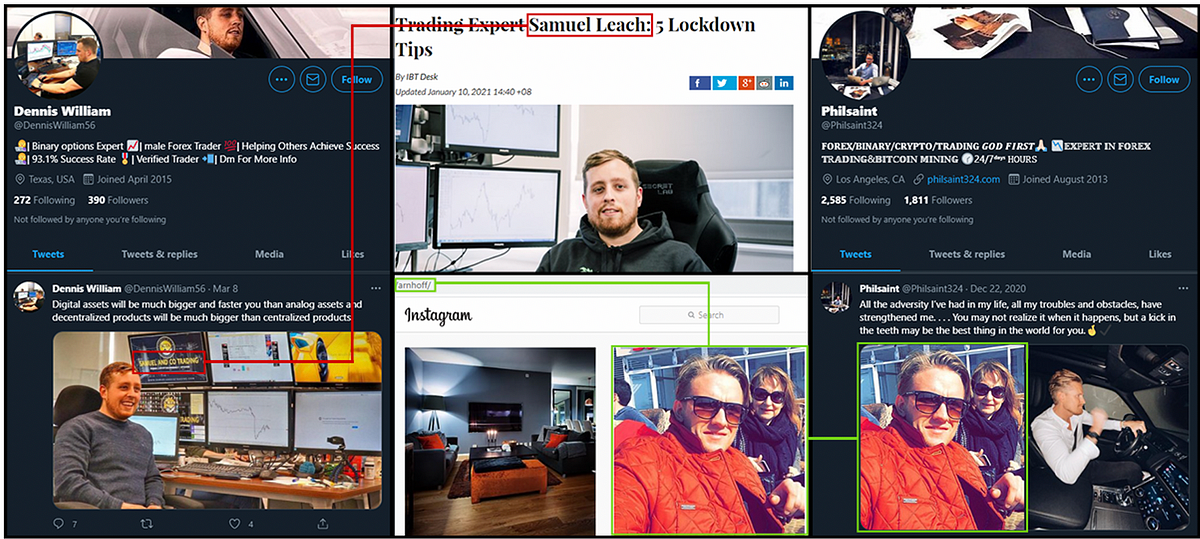
The second part of the network used several sockpuppets that took on the personas of successful U.S.-based cryptocurrency and forex traders. Even cursory OSINT analysis shows these accounts are fake: profile and bio images were appropriated from other social media sites, and the images used to flaunt “their” wealth could be found using reverse image searches.
For example, @DennisWilliam56 claims to be a forex trader based in Texas, but reverse image searches revealed the account is using images of Samuel Leach, a U.K.-based day trader. The selection of these images was careless — at least one image still shows the Samuel and Co. logo in the background, and another displays the U.K.-style number plates on the owner’s vehicles.
A deeper dive into the accounts show that the ostensibly U.S.-based accounts had African roots. Using a combination of Twitter’s advanced search and scouring the accounts’ favorites history, old tweets posted to so-called follow trains identified earlier usernames. Following these digital breadcrumbs showed the account recently pretended to be a South African.
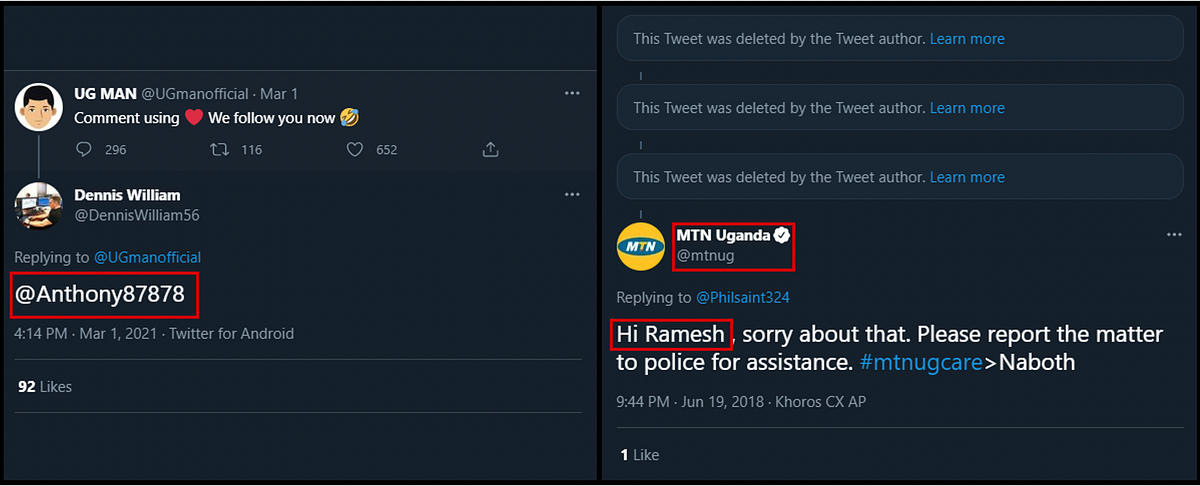
Similar exercise performed on other day trader accounts yielded similar results, with some accounts originating in Tanzania, Uganda, and South Africa before becoming U.S.-based personas. This does not exclude the possibility that the accounts may have been hacked or bought, however.
Off-platform engagement
The next step in the scam occurs when a prospective victim engages one of these day trader accounts. They are ushered off-platform to one or more instant messaging sites. They provide seeminglt legitimate U.S.-based numbers with a request to be added to instant messenger apps. From here, the victim is sent to one of several websites where they will receive their investment “instructions.”
Checking the carrier of two of the mobile numbers provided (one by @DennisWilliams56, and another for their site’s “customer support”) shows that although the numbers look like U.S. phone numbers, they are instead voice-over-IP numbers bought from a Raleigh, North Carolina-based company called Bandwidth.com.
Cobwebsites
The DFRLab has found several examples of these “investment” platform sites from former victims, and by reaching out to the scammers directly. Although there are differences between the domain names, logos, and images used on these sites, their basic premise is the same.
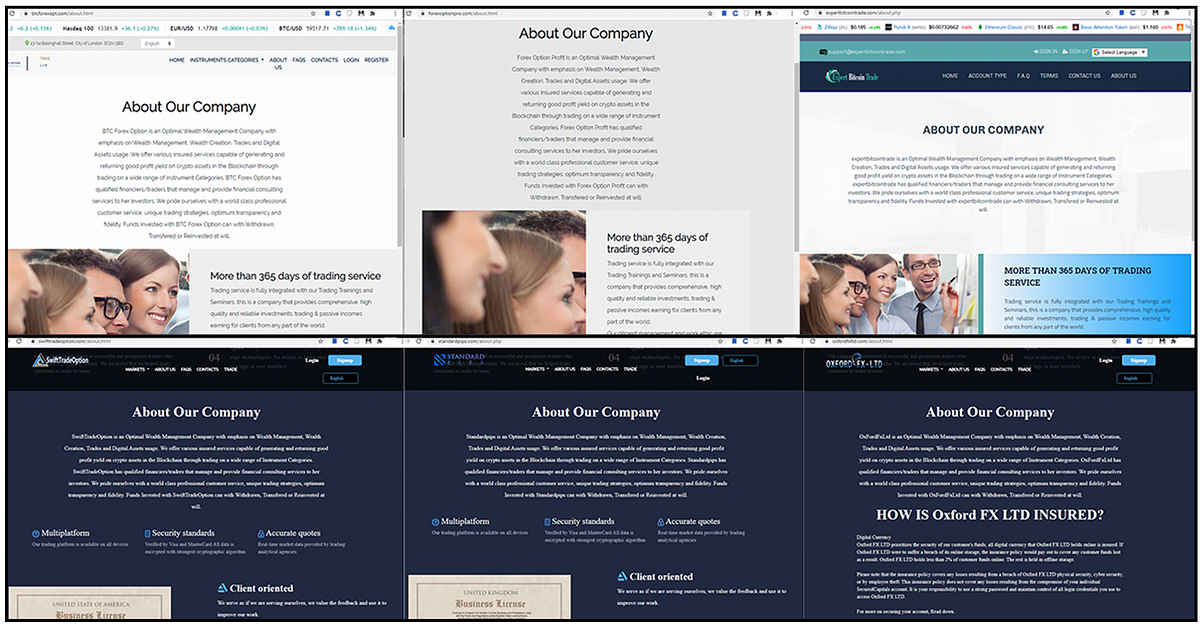
A user is met with a professional-looking website promising impressive returns, and prompted to register to access the site’s trading platform. Once registered, the user is prompted to make their first deposit into a bitcoin wallet.
But the page source code for these sites reveals that a number of them are simply copy/paste clones with minor interface changes. Despite asking a user to register, the entire “back end” is entirely open and accessible even without registering an account in the first place.
Even the displays on the website are fabricated. The trade view window showing cryptocurrency market movements is little more than a plugin, and the frequent “earning notifications” that pop up while visiting the site is generated by a JavaScript code that randomizes the name, location, and amount of these fictitious earnings.
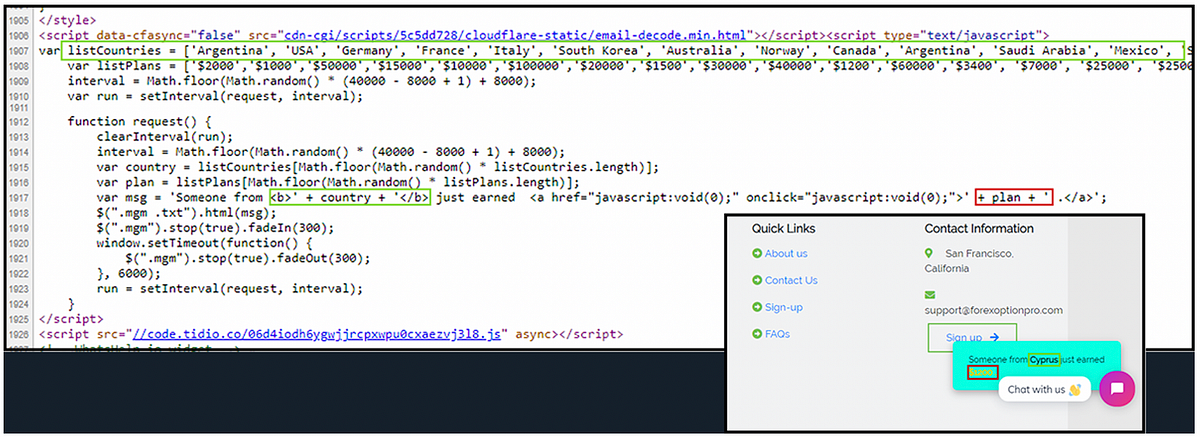
The sole point of this website to provide the victim with the bitcoin wallet address. Once payment is made, the scam is complete, and the money lost.
In essence, this cryptocurrency scam is not dissimilar from traditional scams, and the underlying premise remains aimed at separating victims from their money by providing an enticing “investment.”
Leveraging the oft-mysterious nature of cryptocurrencies with a network of sockpuppet accounts aggressively posting testimonials for the scammers has, however, allowed even middling scammers to reach significantly larger populations of users.
Jean Le Roux is a Research Associate, Southern Africa, with the Digital Forensic Research Lab and is based in South Africa.
The DFRLab team in Cape Town works in partnership with Code for Africa.
Cite this case study:
Jean Le Roux, “Anatomy of a Twitter-augmented crypto scam,” Digital Forensic Research Lab (DFRLab), April 7, 2021, https://medium.com/dfrlab/anatomy-of-a-twitter-augmented-crypto-scam-1d54a875bd06.
Follow along for more in-depth analysis from our #DigitalSherlocks.

