The coordinated information attack attempted to fundraise for Sviatlana Tsikhanouskaya’s inauguration as the new President of Belarus

By Vaidas Saldžiūnas, Nerijus Maliukevičius, and Lukas Andriukaitis
A coordinated information attack involving hacked websites and social media accounts struck Lithuania in late April 2021. A number of small Lithuanian websites were hacked to display messages asking for money to fund the inauguration of Sviatlana Tsikhanouskaya, the Belarusian opposition leader. In addition, several social media accounts were hacked using phishing techniques, according to journalists from the outlet Delfi. Messages shared by these accounts included bank account numbers that traced back to a Polish hospice in Lithuania.
This attack bore several tactical hallmarks of a sophisticated influence campaign identified in July 2020 by the cybersecurity company FireEye, codenamed “Ghostwriter.” Ghostwriter started in 2017 and focused on Lithuania, Latvia, and Poland, targeting NATO troops in the region. On April 28, 2021, FireEye updated the report to indicate an expansion of narratives and targeted audiences and by attributing with high confidence some components of Ghostwriter’s influence activity to UNC1151, a suspected state-sponsored cyber espionage actor. While there was no conclusive attribution to a particular state actor, Ghostwriter generally pushes narratives aligned with Russia’s security interests.
The timing of the attack on Lithuanian targets — it first surfaced on April 29, just one day after FireEye updated its assessment of Ghostwriter’s influence activity — suggested that this may be the latest incident.
Operation Ghostwriter
On April 29, 2021, one day after the release of the Ghostwriter update, the Lithuanian newspaper Valstiečių žinios’s website Valstietis.lt was hacked and a fake article inserted into its news feed. One more hack appeared the next day, on April 30, with the placement of almost identical fake information. This information was removed from the website in a few hours, but still appears on a cached copy of the site accessible by Google Search.
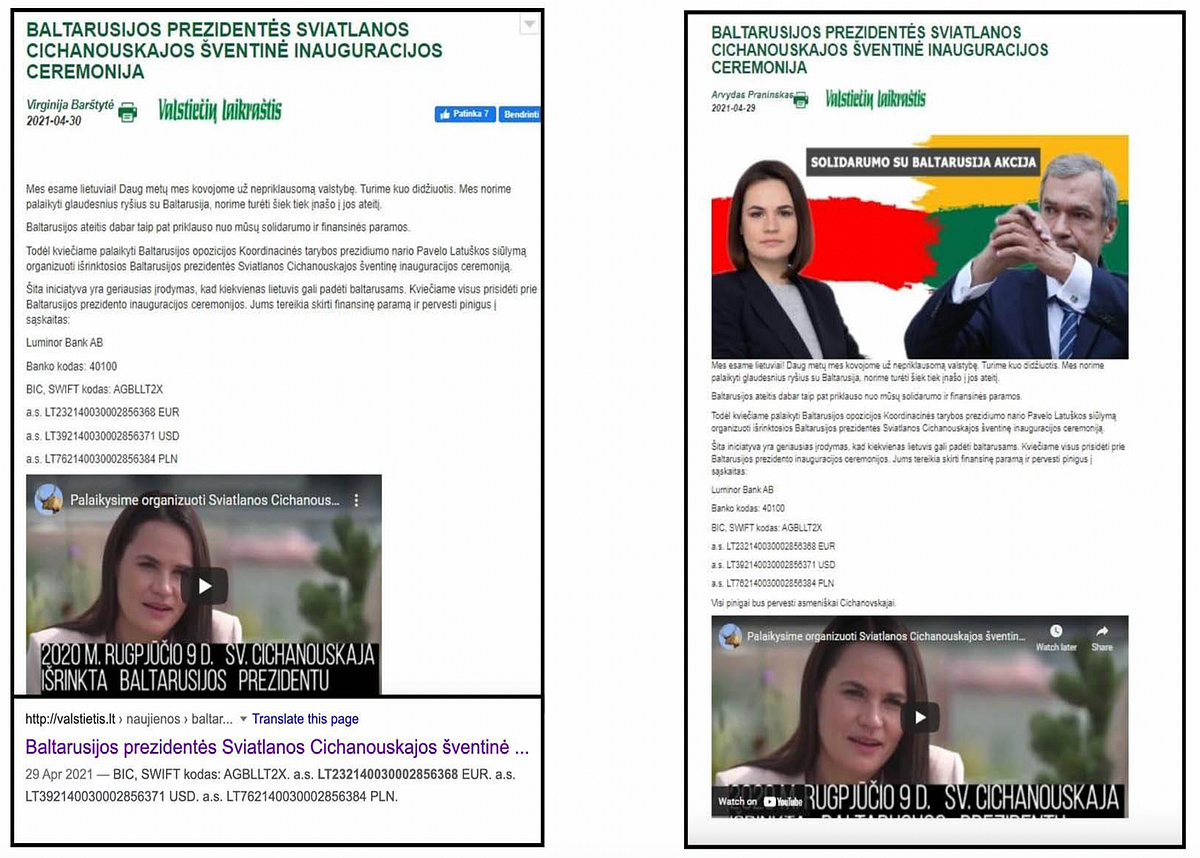
The fake message (with clunky Russian syntax and grammar) was accompanied by a video and alleged that Lithuanians, in solidarity with Belarusian opposition activist Pavel Latushko, should organize a presidential inauguration ceremony for Sviatlana Tsikhanouskaya. Both targets of this disinformation attack are Belarusian activists living in exile. Tsikhanouskaya is the leader of the Belarusian opposition and ex-candidate in the presidential election of August 2020, in which incumbent Alyaksandr Lukashenka claimed victory despite reports of electoral fraud and ensuing pro-democracy protests. She sought refuge in Lithuania after an intimidation campaign and attempted arrest by the Belarusian security services. In April 2021, Pavel Latushko, a former diplomat, announced plans for his own party and called for a new wave of protests in Belarus against the Lukashenka regime.
This is not the first time Valstietis.lt has been hacked. During the previous attack, a fake article alleging the pollution of the Neris River with nuclear waste during NATO military drills, was inserted into the newsfeed. Regional media outlets with poor or no cybersecurity capabilities have become easy targets for hacking and disinformation campaigns recently in Lithuania.
This time the attackers used a novel spin in their fake article: people were invited to donate money for the alleged inauguration ceremony and directed to specific bank accounts for financial transfers, presenting the targeted Belarusian activists as financial fraudsters. Attackers used the bank accounts of the Hospice of Blessed Priest Mykolas Sopochka, well-known Polish charity organization in Vilnius. On May 7, 2021, the hospice denied having anything to do with this information campaign.
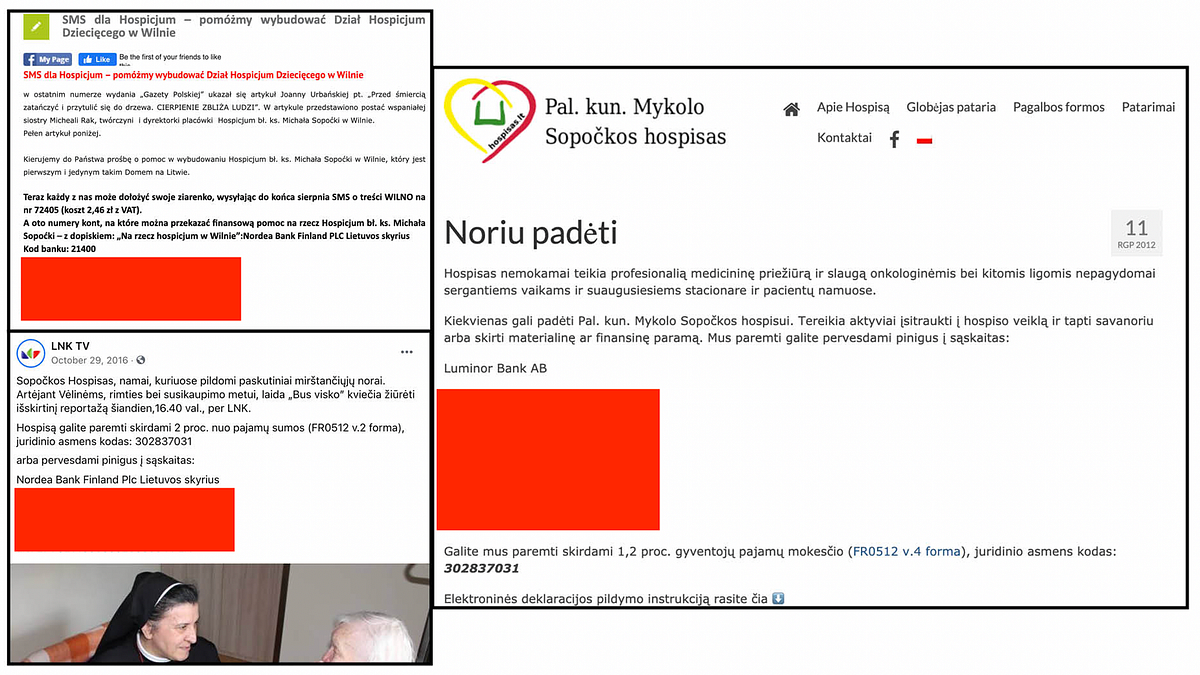
The Ghostwriter update by FireEye emphasized that recent disinformation operations have heavily targeted Polish organizations and public figures. It is no surprise, then, that a recent iteration may have taken advantage of the complicated history of Lithuanian-Polish relations. As security studies professor Thomas Rid pointed out, “The goal of disinformation is to engineer division by putting emotion over analysis, division over unity, conflict over consensus, the particular over the universal.” The recent attacks in Lithuania and Poland follow this “divide and conquer” pattern.
Ghostwriter strikes again
Open-source clues suggested that preparations for the attack on Valstietis.lt started at least two days earlier. On April 27, the YouTube channel Miško broliai (“Forest brothers”) was created. The YouTube channel’s name refers to Lithuanian resistance fighters against the Soviet occupation, invoking patriotic themes. A few videos were posted on this channel over the next few days.
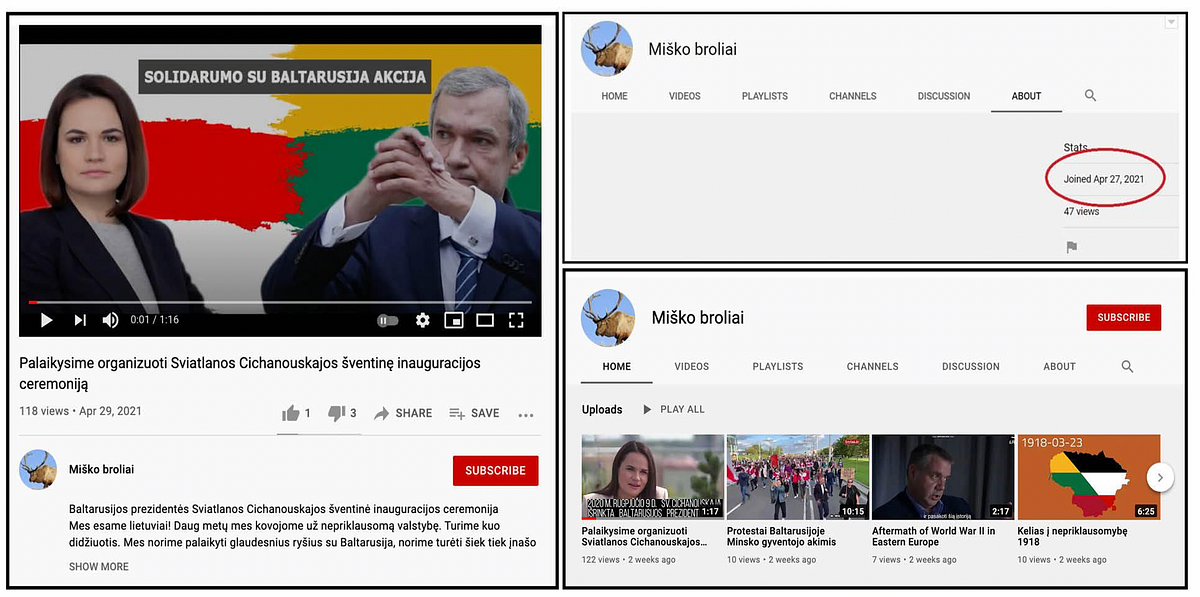
The videos focused on history, contemporary politics, and protests in neighboring Belarus. They were designed to attract some viewership and to mimic normal online behavior of an ordinary YouTube streamer. On April 29, the day of the attack, the hack that later appeared on Valstietis.lt was posted on YouTube by this channel.

The video contained excerpts from the inaugurations of French President Emmanuel Macron and Lithuanian President Gitanas Nausėda. The Vienna Waltz by Johann Strauss was used for the background music alongside the message, “We must organize a festive inauguration of Sviatlana Tsikhanouskaya.”
When the fake article with the video was inserted into the Valstietis.lt site, the cyber component of this operation was already in full swing: multiple internet sites had been attacked via security gaps in their web maintenance service, Synergy Effect.
Although this recent attack targeted Belarusian opposition leaders in Lithuania, it follows the pattern of previous attacks against NATO troops, extensively described by FireEye in its report on Operation Ghostwriter. One important feature of this disinformation attack stands out: the way the attackers intended to distribute disinformation across the social media ecosystem.
The perpetrators decided to use a “super spreader” technique. First, they hijacked the Twitter and Facebook accounts of a key member of the patriotic organization “Lithuanian Freedom Fighters Union.” Second, they used the accounts for spreading disinformation at scale: these messages purposefully tagged major Lithuanian media outlets, politicians, foreign embassies, and other key social media accounts to get their attention.
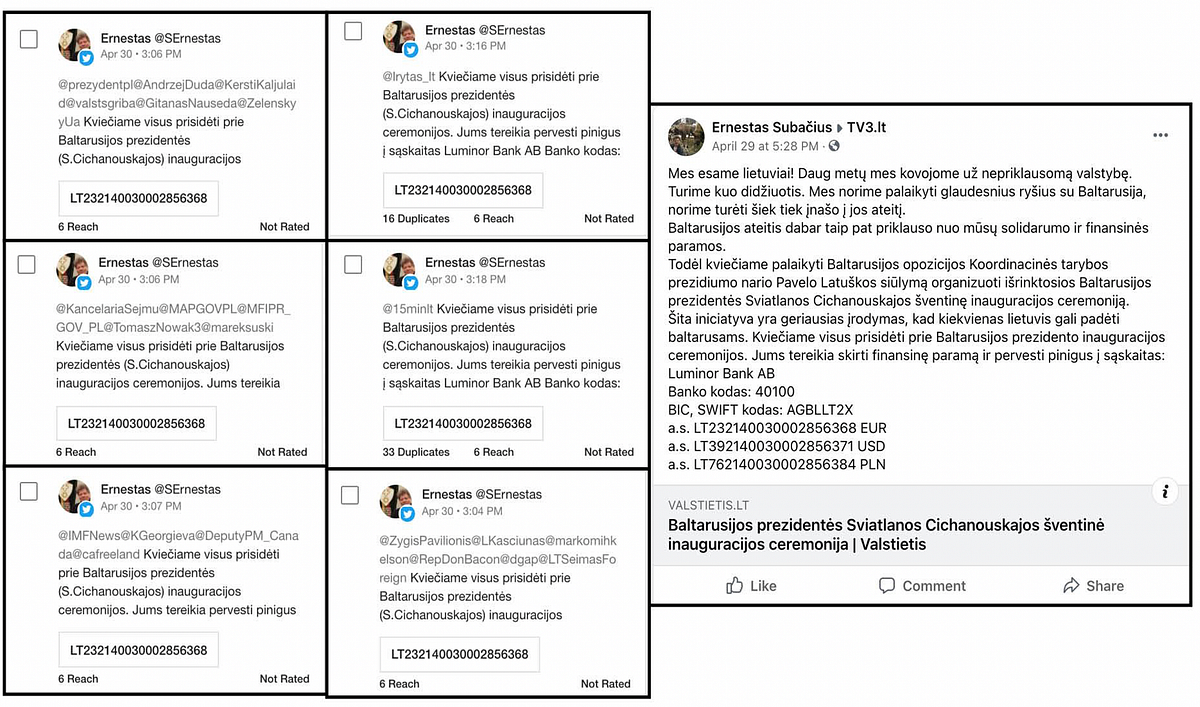
This account holder told Delfi (the largest Lithuanian media outlet that first reported on this and similar disinformation attacks in the past) that his social media accounts were compromised. He then realized that he was unable to access his accounts for several days (coinciding with the period of the disinformation attack). He told journalists that he personally did not spread the disinformation, and this was done by a malicious actor from his account, after he unwittingly disclosed his passwords by replying to a phishing email.
His Twitter account was registered in 2012, but until April 30 the account was empty and did not contain a single tweet. On April 30, though, the account published 163 Twitter replies to different posts by Lithuanian and international media, political parties, prominent political and public figures to amplify the disinformation message in the Valstietis.lt hack and the YouTube video. On Facebook, this account holder happened to befriend a large number of decision makers, including the Lithuanian Prime Minister and Ministers of Foreign Affairs, National Defense, Finance, Social Security and Labor, as well as key members of parliament. Doing so would allow the operator of the account to reach a much larger and more consequential audience.
This technique follows the patterns of Operation Ghostwriter, as Lee Foster, senior manager of the information operations analysis team at FireEye, outlined: “What’s interesting on the social media side here is the compromise of legitimate accounts to do this, rather than impersonating the accounts, because then you’ve got ready access to the followers of that account, and you have the credibility of the content that’s being pushed by that account.”
Although this recent attack was limited in terms of damage done, it once again showed that Operation Ghostwriter is expanding its narratives and targeted audiences, its cyber component becoming more and more complex. The use of super spreader tactics might be an emerging trend to watch for in social networks.
Vaidas Saldžiūnas is a defense journalist at Delfi.lt.
Nerijus Maliukevičius is a researcher of information warfare and propaganda at the Institute of International Relations and Political Science, Vilnius University.
Lukas Andriukaitis is an Associate Director with the Digital Forensic Research Lab.
Cite this case study:
Vaidas Saldžiūnas, Nerijus Maliukevičius, and Lukas Andriukaitis, “Info attack targeting Lithuania bears hallmarks of Operation Ghostwriter,” Digital Forensic Research Lab (DFRLab), June 15, 2021, https://medium.com/dfrlab/info-attack-targeting-lithuania-bears-hallmarks-of-operation-ghostwriter-2e2273d09c47.
Follow along for more in-depth analysis from our #DigitalSherlocks.

