Malware masquerading as Google Bard ads targets millions of Facebook users
Perpetrators presented hijacked pages as Google’s AI service and convinced Facebook users, including a Georgian TV network, to download malicious software
Malware masquerading as Google Bard ads targets millions of Facebook users

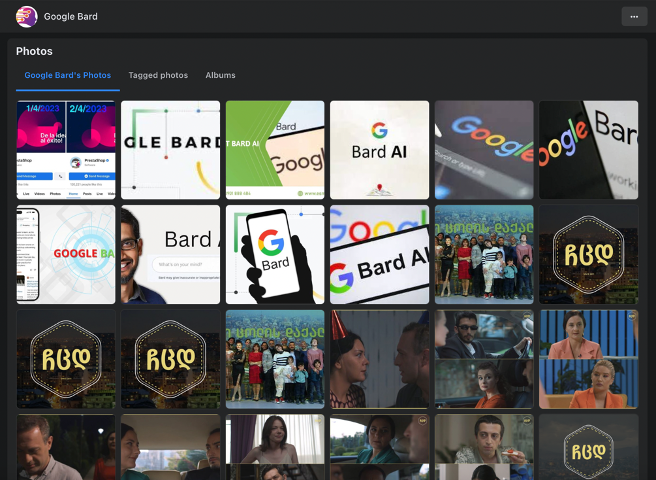
Screencap shows the photos section of a hijacked Formula TV Facebook page with newly posted images related to Google Bard, with older images from the TV network still visible. (Source: Facebook)
Threat actors hijacked various verified Facebook assets and renamed them to variations of the phrase “Google Bard,” using these assets to promote a link containing malicious software. The link targeted Facebook users in the country of Georgia, and may have targeted other countries as well.
Google Bard, an “experimental conversational AI service,” is a chatbot that has been described as Google’s answer to OpenAI’s ChatGPT. In March 2023, Google opened Bard’s waitlist to the public. The service and the waitlist, however, are not available in all countries. At the time of writing, access to the service was only available in the United States and the United Kingdom.
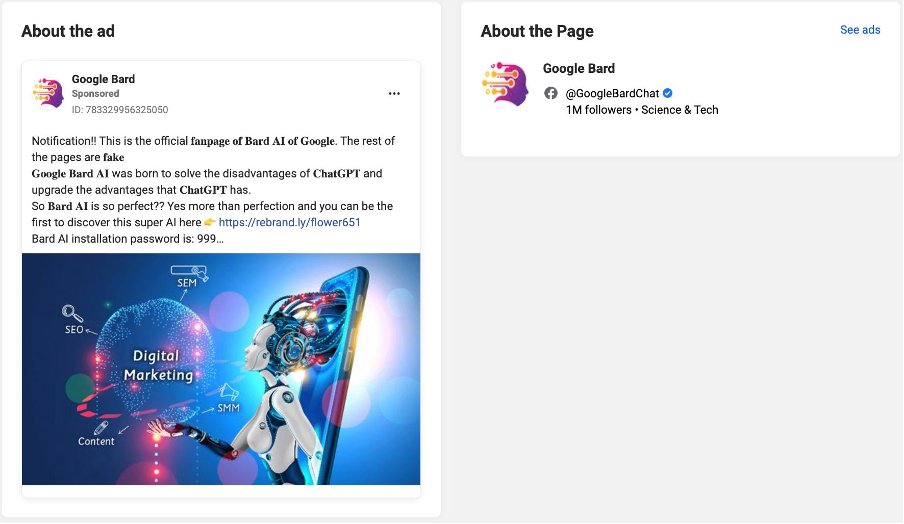
While Google Bard is not available in Georgia, Facebook users in the country have come across sponsored ads in their newsfeeds that encourage users to download Google Bard software via a provided link. The pages promoting these ads all have “Google Bard” in their name. Some of these pages are verified and have hundreds of thousands of followers.
The DFRLab spoke with an employee from the Georgian channel Formula TV, who clicked the link in one of the “Google Bard” ads, then downloaded and installed software. “The sponsored ad was promoted by a verified Facebook page, ‘Google Bard AI,’ with more than 10.5 million followers,” they told the DFRLab. “It did not raise any suspicions for me.” After downloading the software, the individual was locked out of their Facebook account. Threat actors seem to have used this software to gain control over their Facebook account, changing their profile photo and other information.
Notably, they had administrator privileges to Formula TV’s Facebook Business Manager, meaning they had access to all of Formula TV’s Facebook assets, including verified Facebook pages dedicated to Formula TV’s various programs. Soon after the individual lost control of their Facebook account, some of the Facebook pages they administered were taken over and renamed with variations of “Google Bard.” Malicious actors also changed profile photos and other information. They then used these pages to run another wave of sponsored ads feigning to promote Google Bard, further spreading URLs leading to the same malicious software.
The same operation targeted other Georgian Facebook pages, including a political party, marketing companies, and education pages, among others. In collaboration with Formula TV, the DFRLab found eighteen Facebook assets that were affected. A large amount of the malicious activity occurred on March 29 and 30, 2023.
Among the hijacked assets were verified Formula TV Facebook pages dedicated to the Georgian TV series “ჩემი ცოლის დაქალები” (“My Wife’s Friends”). The page, with more than one million followers, was renamed “Google Bard,” its profile and banner photos replaced, and its URL edited to facebook.com/GoogleBardChat. Meta, the parent company of Facebook, has since taken down the page.

The threat actors posted content masquerading as Google Bard, giving users the impression they were interacting with authentic Google content. Although the perpetrators added a number images related to the new Google service, older images showing scenes from the Georgian TV series remained visible.
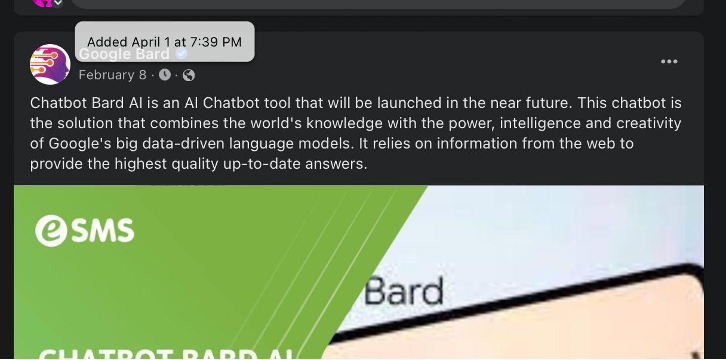
In a possible attempt to obscure the page being hijacked, the threat actors changed the dates of their posts. For example, they published a promotional post about Google Bard on April 1, 2023, then changed its posting date to February 8.
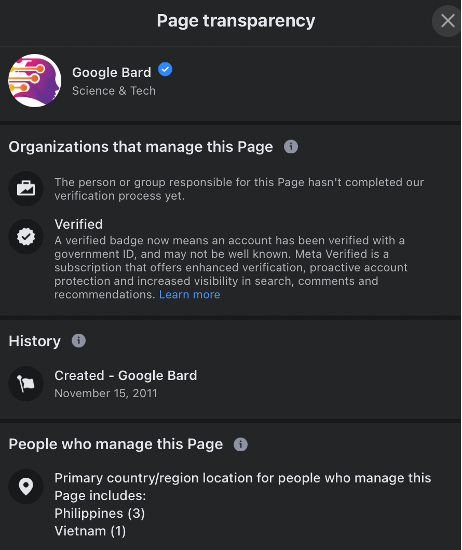
The page transparency section, which typically shows the name change history of a Facebook page, did not display the change, though it included the page’s launch date in 2011. Notably, the transparency section documented the changing of the administrator’s location from Georgia to the Philippines and Vietnam.
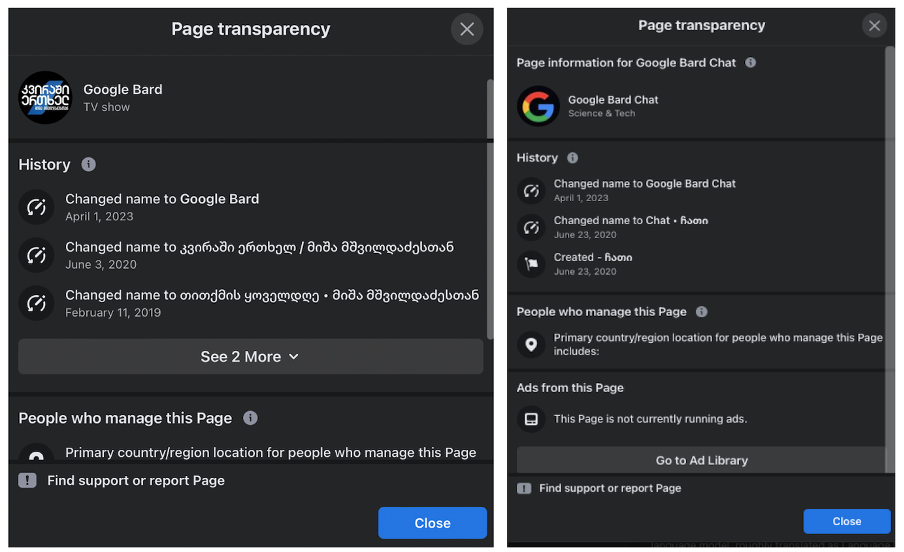
In other hijacked Formula TV pages, the page transparency section documented the malicious name change, including “Google Bard” and “Google Bard Chat,” the former still categorized as a “TV show” and the latter under the topic “Science & Tech.”
Spreading malware with Facebook ads and engagement
To hijack additional pages, the perpetrators also deployed an ad campaign linking to pages containing the malware.
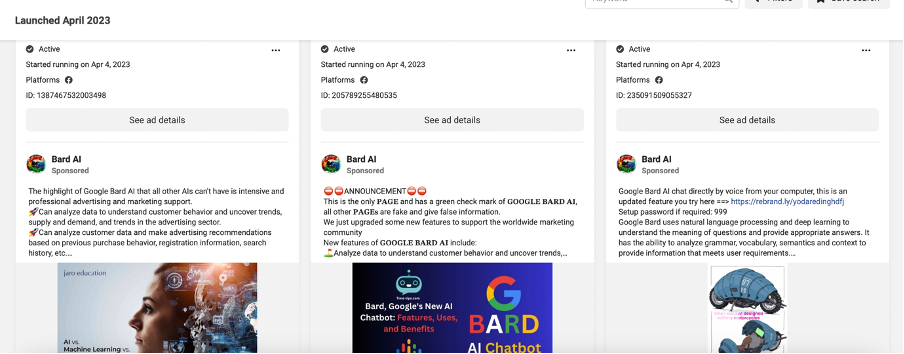
In an apparent attempt to imitate user engagement, perpetrators used a hijacked page to comment on another post. A Facebook page named “Elene Khoshtaria” originally belonged to Georgian politician Helen Khoshtaria, who publicly declared that her page had been hijacked and warned users not to click on any links from the page. Khoshtaria’s hijacked page was used to comment on one of the imposter Google Bard pages, writing, “Thank you this tool is very effective.”
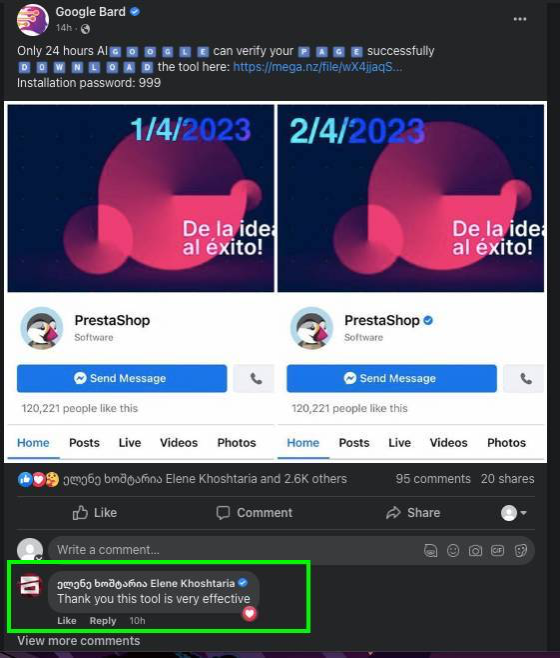
Facebook parent company Meta removed the assets identified by the DFRLab, though it remains unknown whether the malicious operation continues to target Georgia or elsewhere. The DFRLab also found hijacked pages that initially ran content in Spanish, Assamese, and English, among others.
Special thanks to Luka Liponava, Deputy Chief of Digital Communications at Formula TV, for assisting with this story and contributing to its research.
Cite this case study:
Eto Buziashvili, “Malware masquerading as Google Bard ads targets millions of Facebook users,” Digital Forensic Research Lab (DFRLab), April 17, 2023, https://dfrlab.org/2023/04/17/malware-masquerading-as-google-bard-ads-targets-millions-of-facebook-users.

