Deceptive marketing ads used fake images of Polish politician
Digitally altered photos deployed as clickbait in Facebook ads drew users to promotional campaign for sketchy cryptocurrency operation
Deceptive marketing ads used fake images of Polish politician
Share this story

BANNER: Sławomir Mentzen, co-leader of Confederation far right political alliance, delivers his speech during the final day of campaigning for the parliamentary elections in Rzeszow, Poland, October 13, 2023. (Source: Patryk Ogorzalek/Agencja Wyborcza.pl via Reuters)
This report was produced as part of the international election monitoring project of the Polish Election Watch network, implemented by Alliance4Europe, OKO.press, and the Atlantic Council’s DFRLab.
The DFRLab found over thirty Facebook pages that have been running clickbait ads displaying digitally altered photos of right-wing Polish politician Sławomir Mentzen as a means of drawing an audience to a dubious cryptocurrency operation. The ads used images of Mentzen portraying him in a negative light but seemed mostly to use the photos as a driver for financial gain, as they all ultimately directed Facebook users to the operation via a number of suspicious websites.
Facebook is the most frequently used social media platform in Poland; over 75 percent of Polish internet users visited Facebook in April 2023, the last month for which data was available. Given that this campaign launched in the lead-up to Poland’s parliamentary elections on October 15, 2023, the political nature of the fabricated content had the potential to negatively affect Mentzen’s electoral prospects by presenting him in a questionable light, despite the underlying motivation most likely being a financial one.
Mentzen is chairman of the libertarian political party, Nowa Nadzieja (“New Hope”), the largest far-right group in the Confederation alliance. Previously, he was vice president of the KORWiN party (New Hope’s predecessor) and unsuccessfully ran for the Polish parliament, known as the Sejm, in 2019. Ahead of the October 2023 parliamentary elections, Mentzen was one of the most active Polish politicians on social media; according to pre-election polling, he received the greatest support among people aged 18-39. However, in the final results, the Confederation alliance received only 7.16 percent of the vote, much lower than expected, though Mentzen did secure a seat in the Sejm.
According to Google Trends, Mentzen was among the five most frequently searched for Polish politicians on Google between September 14 and October 15, 2023. Drawing on this popularity, the Facebook ad campaign at the center of the DFRLab investigation used clickbait text and, as mentioned, manipulated photos of Mentzen. Clickthroughs would then redirect users to what seemed to be fraudulent websites either that appeared to have a goal of signing users up to sketchy cryptocurrency operation BitQT, or that included a dubious registration form with an unclear end-use for the data it collected, though that too often appeared alongside ads for BitQT.
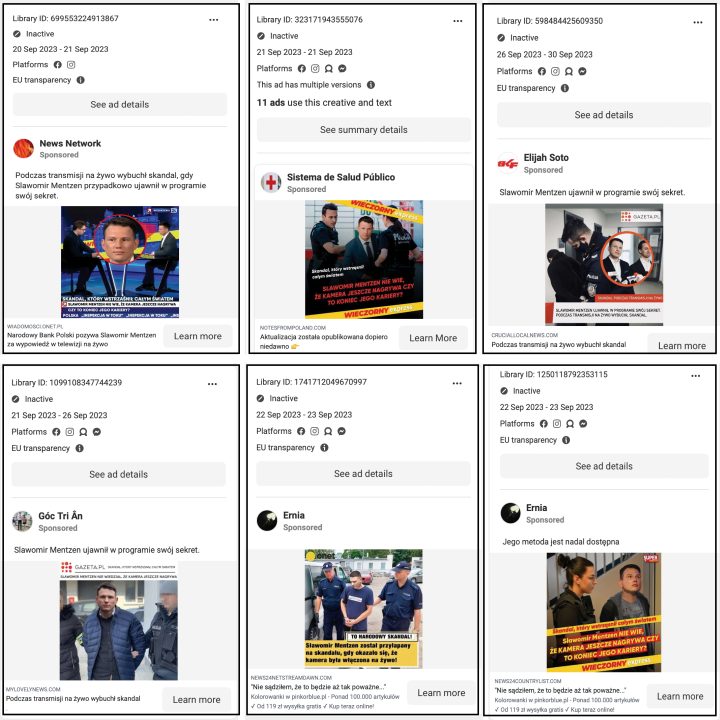
A majority of the Facebook advertisements involved in this campaign featured digitally altered photos purporting to show Mentzen being arrested, along with the caption, “a scandal broke out during the live broadcast, when Sławomir Mentzen revealed his secret in the program by accident.” The DFRLab found no evidence that Mentzen has ever been arrested. It seemed that the salacious text and accompanying photos aimed at prompting Facebook users to click on the advertisement and visit the destination websites. The DFRLab investigated Facebook pages running the fake ads and found that they were created at different dates and times and that the websites that the Facebook ads linked to appeared topically unrelated to the substance of the ads: in some cases, the destination websites contained text copied from legitimate websites but most often ultimately funneled users toward BitQT; in other cases, the ads pointed directly at promotional websites for the dubious cryptocurrency operation. The pages posting the ads, meanwhile, seemed to mostly be posting ads in Polish, indicating their target audience to be in Poland, despite their clickthrough destinations often being in English or other languages.
Misleading Facebook ads
The DFRLab found advertisements that used identical images often seemingly for legitimate websites but in actuality pointing users to different websites than would be expected, and different Facebook pages were behind the ads. Many of these ads contained identical sensational text descriptions, as mentioned above, and used one of many digitally altered photos of Mentzen. Moreover, some of the relevant Facebook pages ran multiple identical ads, and these ads could be found across all of Meta’s platforms – Facebook, Instagram, and Messenger. According to Meta’s Ad Library, dozens of ads used the same images and text about Mentzen’s supposed arrest.
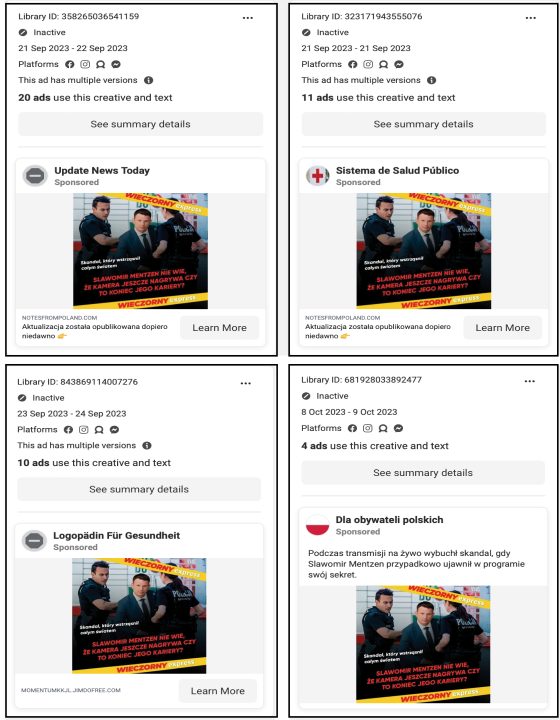
The DFRLab ran a reverse image search of some of the digitally altered photos featured in the misleading ads and found the original versions of these photos elsewhere online, and none of them originally featured Mentzen. Instead, it appeared the operators behind this campaign digitally replaced the heads of detained individuals in the original images with Mentzen’s head. Some of the original images depicted arrests in Poland, while others showed arrests outside of Poland, though – as noted – none featured Mentzen.

Facebook pages
Many of the Facebook pages running the misleading ads had names related to investments and business, including Forward Investment, Integra Business Advisors, or Capital Connection. Other page names contained the word “fashion,” including The photography fashion HDR concept, Fashionherbb, Fashioniconics, Fashionin-saner, or Fashionigniters. Among all of the Facebook pages running the misleading ads as of October 9, 2023, the DFRlab found only one Facebook page that had a Polish name (Dla obywateli polskich), as a majority of pages the had English names. However, a few pages also had names in Ukrainian, Vietnamese, and Spanish.
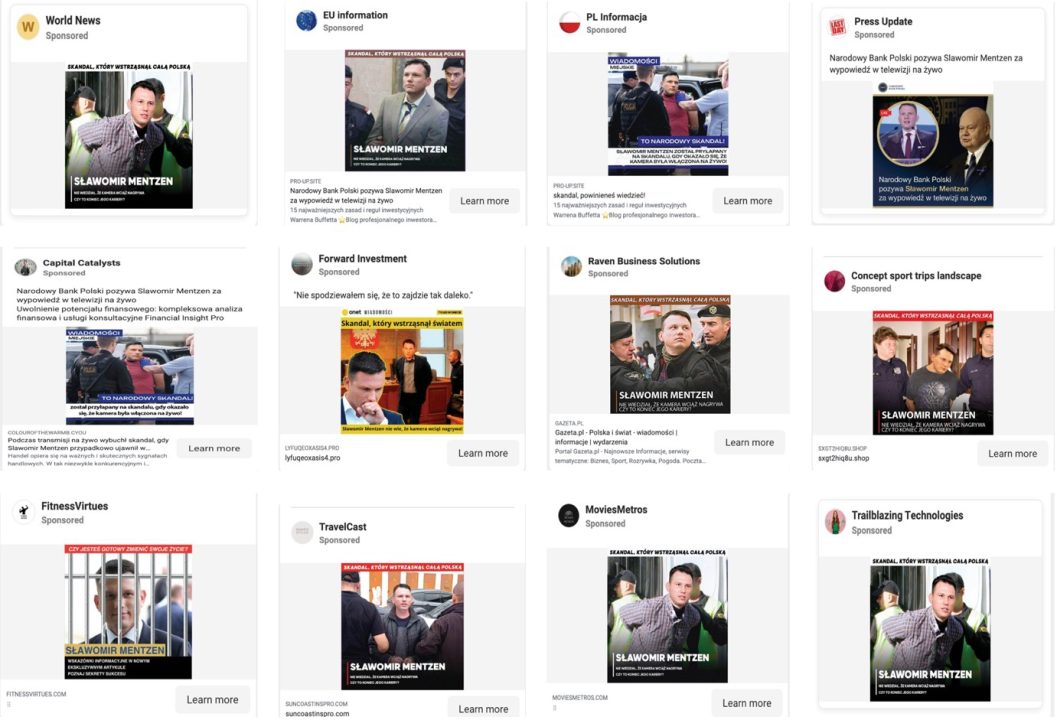
The DFRLab also observed that some of the Facebook pages had website addresses listed in their introductions and that these websites had similar names. Moreover, these websites primarily featured English-language content frequently stolen from other legitimate websites. However, these websites sometimes posted stolen content, specifically articles with identical body texts, though with altered headlines, mainly copied from legitimate (and very likely unaffiliated) websites.
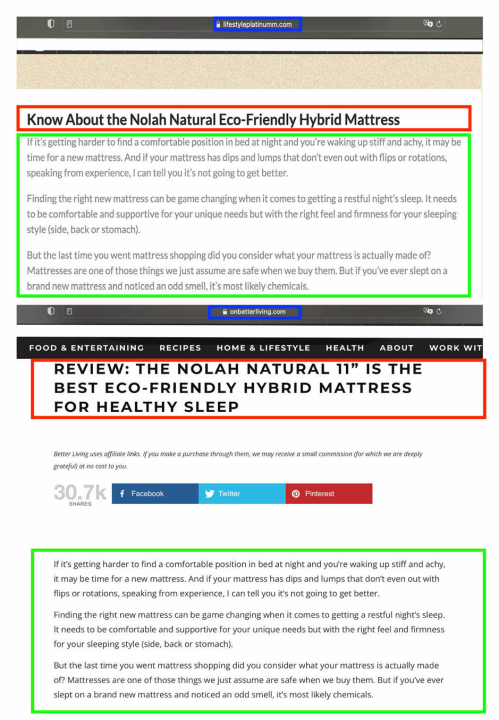
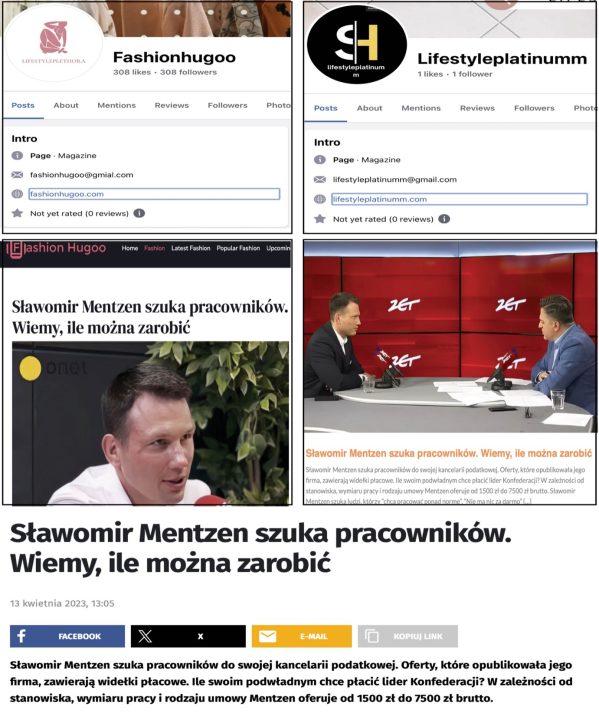
In another case, some of these websites reused Polish-language text focused on Mentzen, saying that he was looking for employees for his tax office. The text, however, was originally published by Polish media outlet Onet in April 2023, indicating that the clickbait websites attached to the misleading ads seemingly stole it from Onet.
Forged websites
The DFRLab also examined the scam websites used as landing destinations for the misleading Facebook ads. We found that a majority of the identified domains were registered using US-based domain registration company NameCheap, Inc., which itself uses Withheld for Privacy, a service that ensures information about the actual owners of websites remains hidden from public WhoIs databases. As such, WhoIs data for the actual identities of those behind the websites is seemingly not available in the open-source environment.
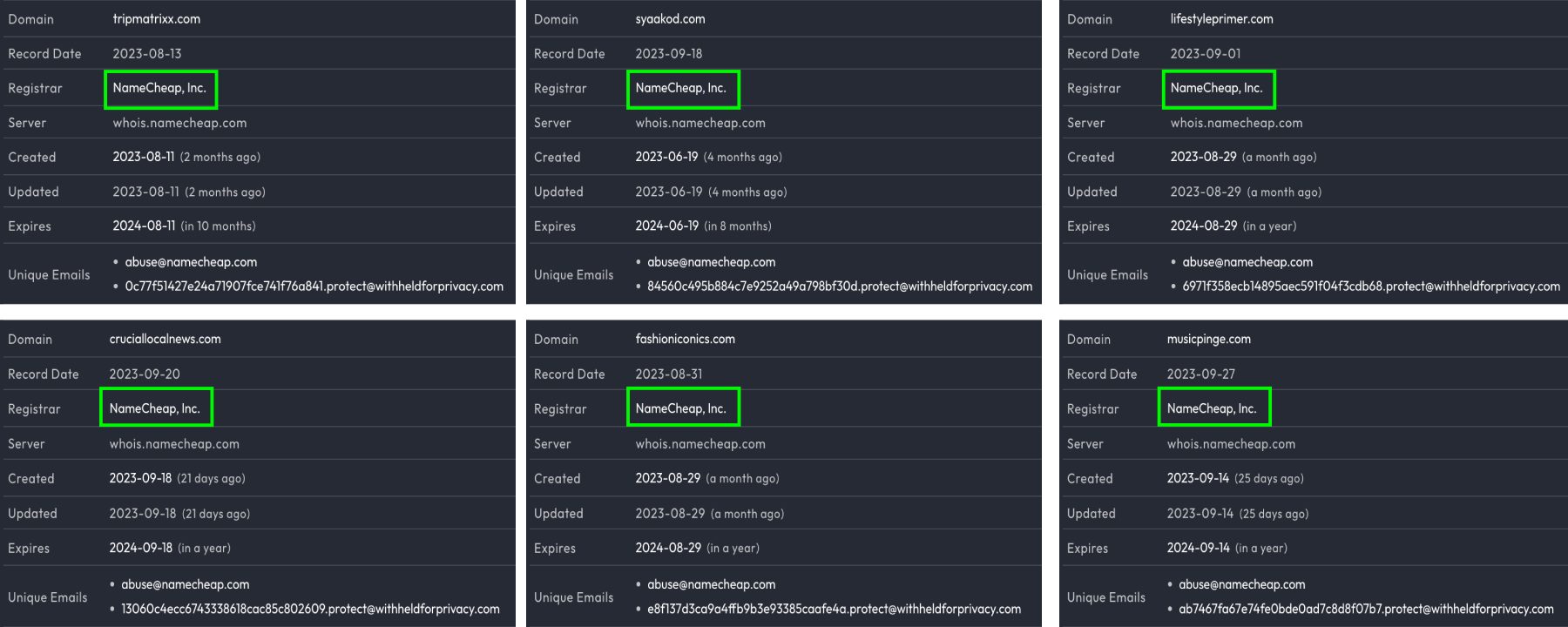
A majority of these websites feature clickbait articles and declare that visitors can get rich quickly. They also contain likely fake testimonies of how other people got rich by investing in the product offered by the respective website, which was very often a cryptocurrency operation by the name of BitQT.
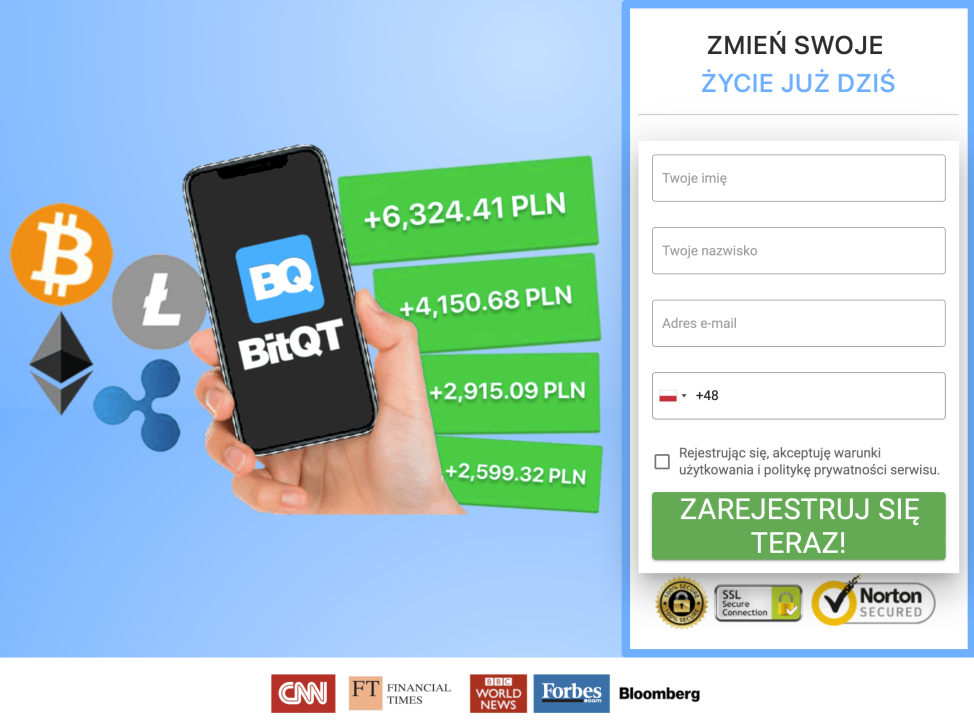
The DFRLab also found that a majority of the websites prompted users to submit personal data with a form, declaring: “change your life today”… “register now!” The form, often found next to a promotion for BitQT, asks visitors to provide their name and surname, an email address, and a mobile phone number. The DFRLab was unable to find any evidence of monetization – i.e., that clicks on these websites provided the operators some form of remuneration – and there was no native or programmatic advertising present on these sites, as evidenced by the absence of Google Ads or similar advertising platforms. Therefore, it is possible that those visitors who submit their contact information would be contacted by the operators behind this campaign.
Impersonation of local media websites
Some of the affiliated pages that posted the misleading advertisements impersonated reputable Polish media outlets and used their logos and a similar visual interface to lure Facebook users into visiting one of the fake websites linked to the advertisements. For instance, Facebook page Sistema de Salud Público sponsored an advertisement that included a link to a website impersonating popular English-language news portal Notes From Poland. Upon clicking on the embedded link, however, users were directed to zd.gearsepal.com, which seems to have been stolen from the website of 2022 European Summer School of Quantum AI. Images on the misleading ads also featured logos of actual media outlets, including Gazeta.pl, Polsat, TVP, and Onet.
Another impersonating news portal Cruciallocalnews.com seemed to steal its content and design from Carwashspa.pl. The landing page for another of the impersonating websites, mylovelynews.com, looked like it is a personal website for Mentzen but also featured content stolen from other websites.
The DFRLab also found a website preproad.click that impersonates Onet’s website interface, and one article published to preproad.click is seemingly a transcript of a supposed interview Mentzen gave to Kamil Szewczyk, host of TV program “Evening Express.” The headline for the article reads “the National Bank of Poland is suing Slawomir Mentzen for his statement on live television.” The DFRLab was not able to find an actual interview on this topic anywhere on the internet, however.
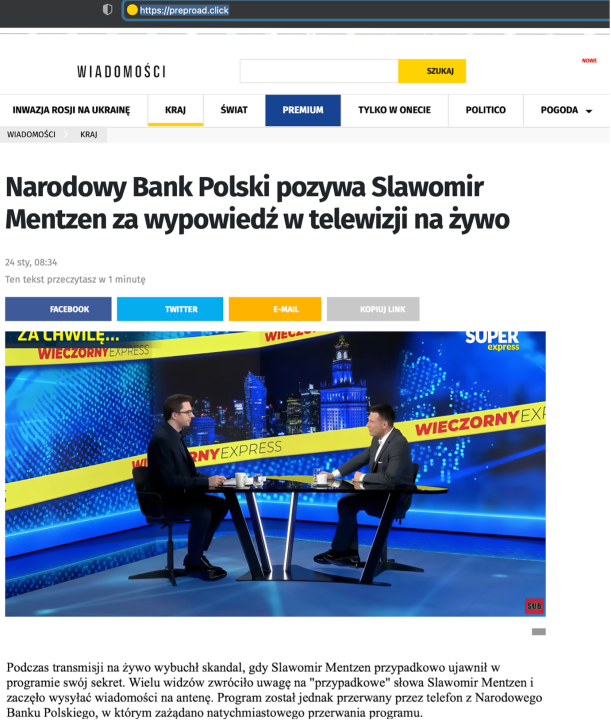
According to a post – very likely fabricated – on preproad.click, Mentzen managed to earn money using the BitQT investment platform, and in the seemingly fake interview he explains to readers how to use the platform to start earning money.
Clicking on any other section of preproad.click website directs visitors to browny.homes, which features the BitQT logo and a personal data collection form, which is designed to look like a registation form for BitQT. The DFRLab was able to find similar indications of BitQT connections on other websites, such as l1feofan2turer.online.
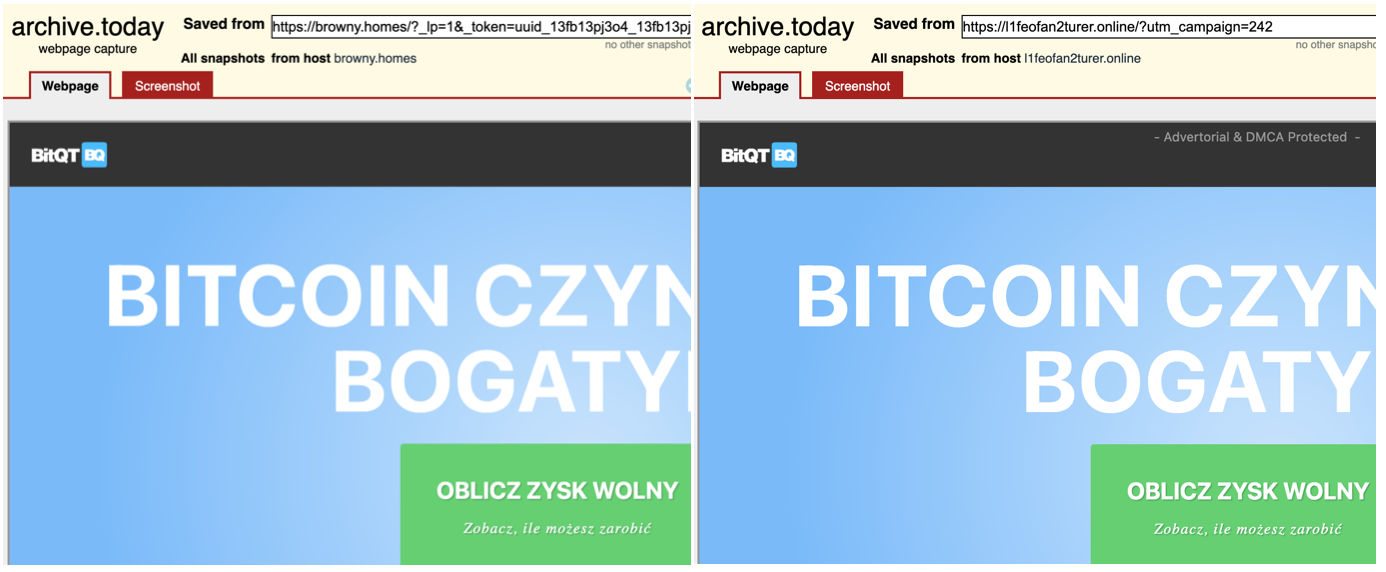
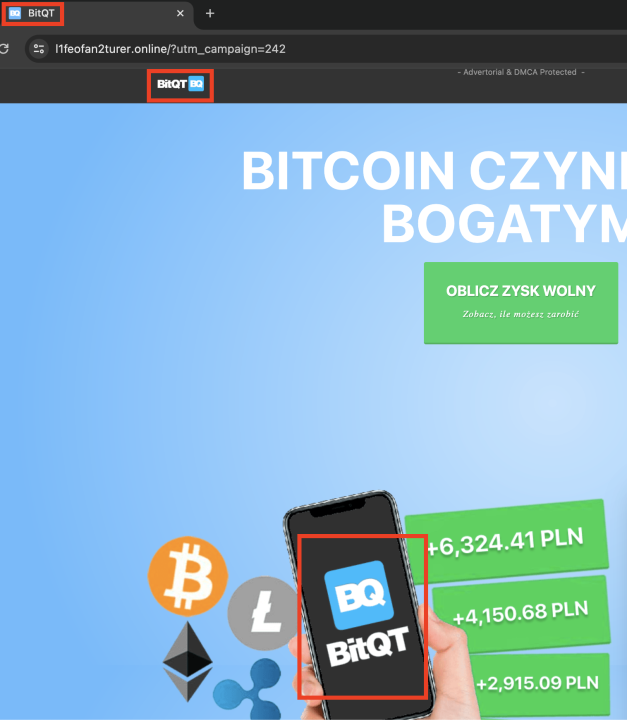
Indeed, when opened in Chrome, the tabs for the same websites even stated “BitQT” as the name, further indicating a close connection with the crypto platform.
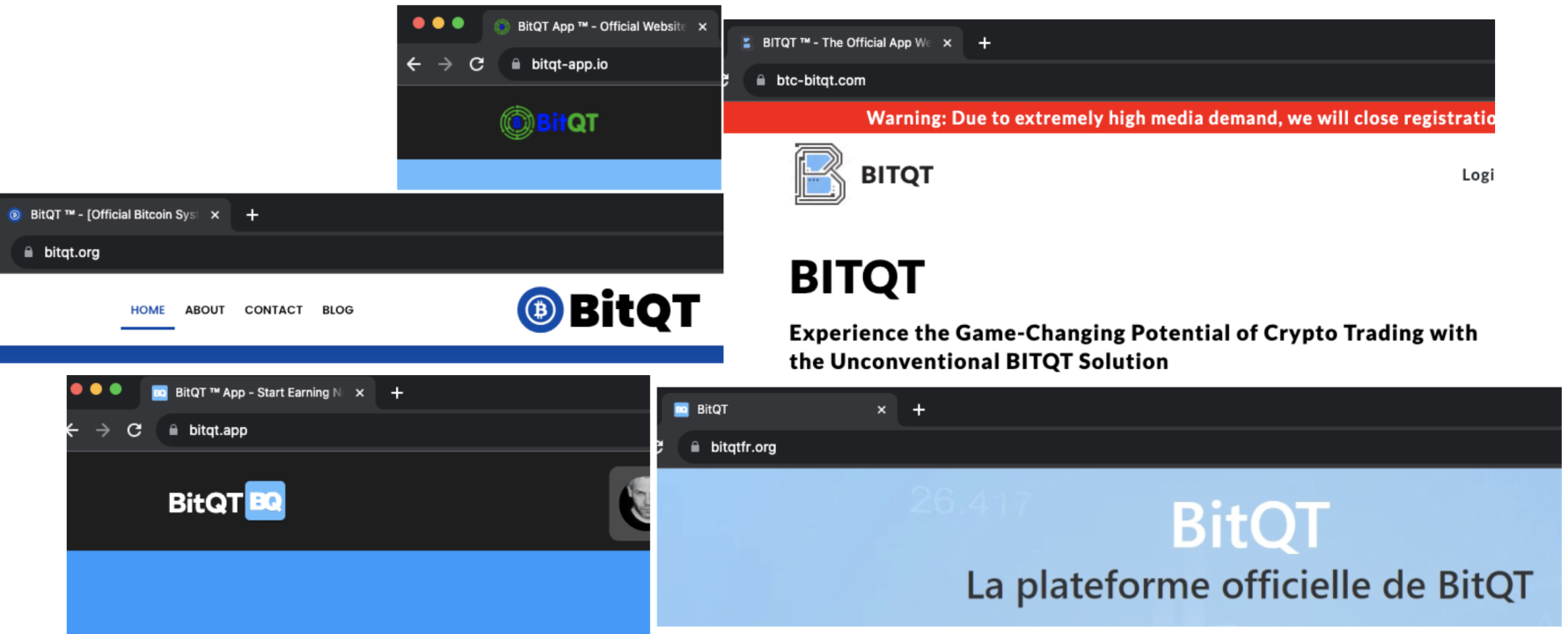
What is BitQT? It’s not entirely clear
BitQT is advertised as a trading service, app, or platform for cryptocurrencies across multiple websites with no fixed description for what exactly it is, and there are multiple pages seemingly affiliated with it, including bitqt.org, btc-bitqt.com, bitqt.app, bitqt-app.io, and the French-language bitqtfr.org. The operators declare on one of the websites that it is “your gateway to the world of automated Bitcoin and Crypto trading.”

All but one of the logos on the websites identified by the DFRLab did not match that found on the promotional websites the Facebook ads ultimately led to, so it is possible they are unrelated, but they all include similar registration forms and advertise a product named BitQT.
The DFRLab could not find many first-person accounts of people who have used the service and so cannot determine whether it is a scam or just an actual, if hard-to-understand, service. That said, at least one YouTube video has concluded that the operation is a scam. Elsewhere, one reddit poster declared that they “nearly fell for the BitQT scam” and that, after filling out the registration form, “7 different numbers from different countries […] called me.” While the DFRLab could not verify this, at least one of the BitQT-associated websites does note in a disclaimer that it serves as an advertiser for its “partner brokers.”

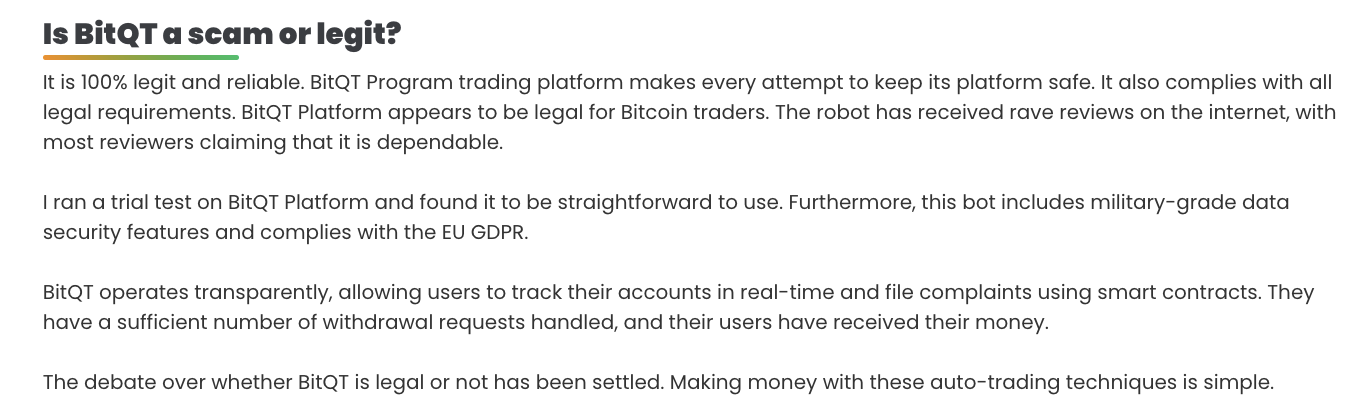
On bitqt.org, the operators declare repeatedly – in a somewhat defensive tone – that the platform is legitimate and trustworthy, but none of the claims are backed with any evidence such as external reviews from reliable sources. It goes so far as to answer – again without details – the question of “is BitQT a scam or legit?”
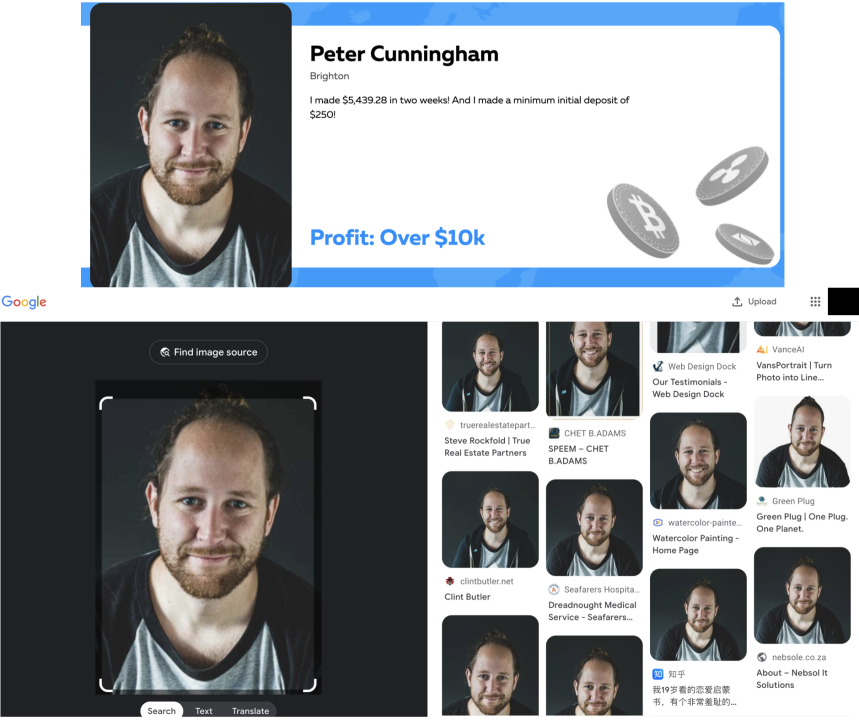
Meanwhile, the bitqt.app website includes testimonials from supposedly real users, all of whom are purportedly located in British cities like Coventry or Southampton, yet employ photos of other people found elsewhere on the internet. One testimonial, supposedly from Brighton-based “Peter Cunningham,” uses a photo that according to a simple Google Image search has clearly been reappropriated many times across multiple websites.
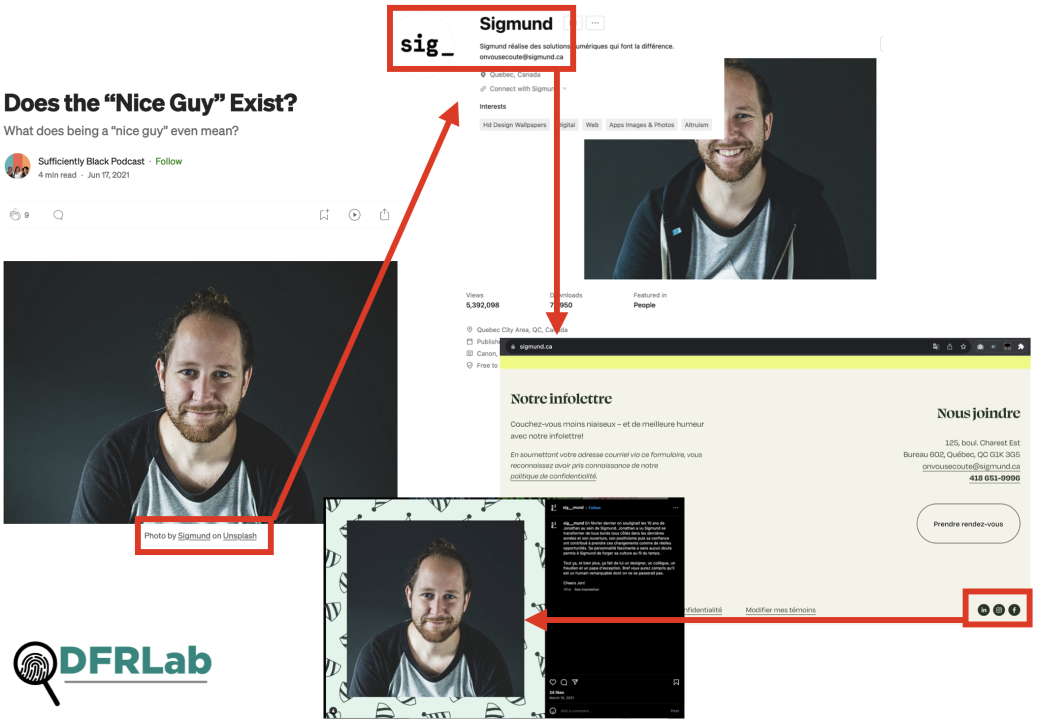
The DFRLab traced the photo back to an Instagram post by Quebec-based digital developer Sig_mund.
One of the earlier results in the Google Image search led to a Medium post by Sufficiently Black Podcast titled “Does the ‘Nice Guy’ Exist?” The post used the same image as its banner and included a source of “Photo by Sigmund on Unsplash,” with embedded links to licensing website Unsplash. The Unsplash account, Sigmund, included a similar photo of the same individual likely taken during the same photo shoot, and the account profile included an email address. Going to the domain name in the email address led to Sig_mund’s homepage, which includes an Instagram account button at the bottom. Clicking through to the Instagram account led to the original photograph, posted on March 15, 2021, alongside a caption celebrating an employee’s tenth anniversary with the company.
Other photos on the BitQT.app website were similarly reappropriated.
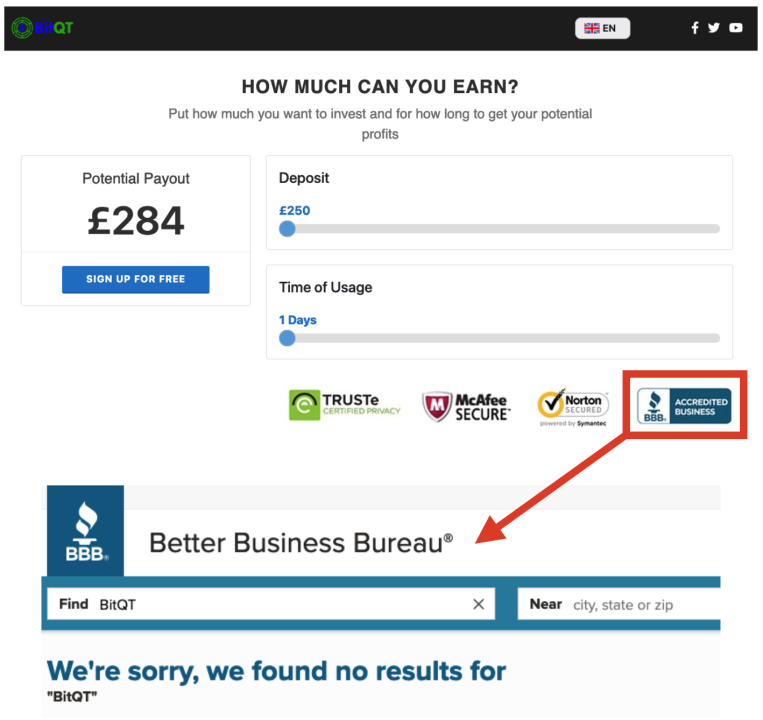
One of the websites, bitqt-app.io, indicates that BitQT is an accredited business with the US government’s Better Business Bureau (BBB). A search of the BBB’s database, however, returned no results.
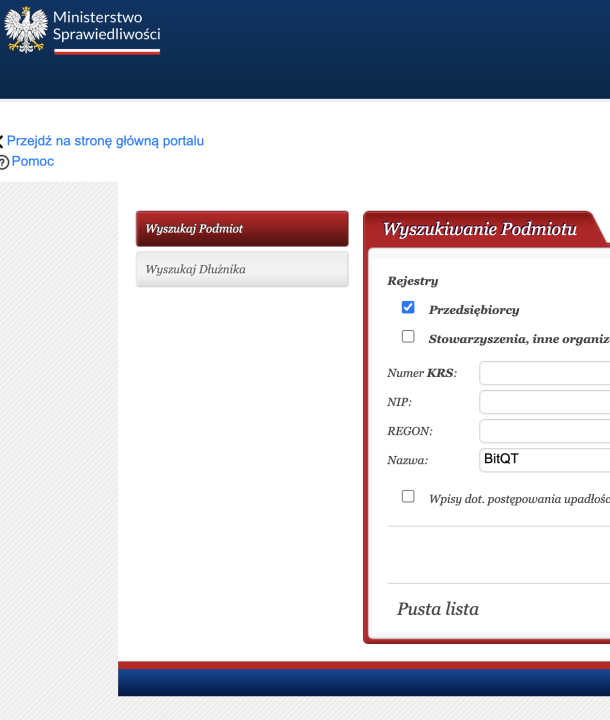
Given the Facebook ad campaign that incited this investigation targeted a Polish-speaking audience, the DFRLab also checked Poland’s business registrar for “BitQT,” which also returned no results.
Another possible indicator of BitQT’s questionable status, though much more circumstantial, is that the supposed testimonials on the BitQT.app website all state they received a payout in dollars instead of British pounds, as would be expected if those giving the testimonies actually lived in the United Kingdom as indicated.
WHOIS queries for the BitQT promotional websites were also inconclusive, as the operators used registration for all of the websites, and the registration services in those cases were all different. One of the them used Name Cheap, which was also used by the fake websites mentioned earlier. Meanwhile, the app’s Terms and Conditions appear to have been auto-generated or cribbed from a template, as they do not include any specific language beyond a single mention of “bitapp” – rather than “BitQT” – at the beginning.
The only mention of BitQT in more mainstream sources found by the DFRLab was a sponsored press release found on Yahoo! Finance from March 2021, notionally sourced from 72hours.org, itself a sketchy promotional website seemingly designed to anonymously pump products.
Whatever BitQT’s origins or intentions, this campaign used fake images of a popular Polish politician – at the time of peak interest around the parliamentary elections – in order to push people to sketchy intermediary websites. The Facebook ads used logos and images from legitimate outlets, deceiving users to click through by virtue of their trust in the indicated outlet, but actually directed them to the intermediary websites, which often promoted BitQT or included registration forms with unknown purpose. Given the salacious nature of the advertisements featuring Mentzen, this campaign seems to be exploiting the image of a popular politician mostly for financial gain, rather than as a means of scoring political points.
Cite this case study:
Givi Gigitashvili and Iain Robertson, “Deceptive marketing ads used fake images of Polish politician,” Digital Forensic Research Lab (DFRLab), December 7, 2023, https://dfrlab.org/2023/12/07/deceptive-marketing-ads-used-fake-images-of-polish-politician/.

