Doppelganger targets Ukrainian and French audiences via Facebook ads
The latest iteration of the Russian information operation reveals an increasing sophistication in tactics against Ukraine and other audiences
Doppelganger targets Ukrainian and French audiences via Facebook ads

BANNER: Fake version of the Ukrainian news site UNIAN, part of the Russian information operation known as Doppelganger. (Source: unian.pm/archive, Fake Stamp PNG HD Image)
The DFRLab identified more than 500 Facebook ads promoting the latest iteration of Russia’s Doppelganger operation. The ads and pages in the campaign were typically removed from the platform within one day. Despite the rapid takedowns, the newest iteration of the operation demonstrated an increasing attempt at sophistication. The campaign deployed obfuscated URLs that redirected users to domains, sometimes geofenced, impersonating Ukrainian media outlets, as well as French ones.
Operation Doppelganger is a constantly evolving online campaign that creates forgeries of authoritative news websites to spread anti-Ukraine narratives. The operation was first exposed by Meta and the EU DisinfoLab in September 2022. The French government agency VIGINUM, tasked with combatting disinformation, attributed the campaign to Russia. VIGINUM described the operation as a “complex and persistent online manipulation campaign.” Two years into Russia’s invasion of Ukraine, the well-documented operation continues to target audiences in Europe. While platforms have increased their resilience to the campaign, and even attributed it to Russian businesses, the operation remains diffusive and at large.
The DFRLab previously identified an early iteration of the doppelganger operation in 2022. We have continued to cover campaign’s developments over the years, including a campaign to spread conspiracies about military aid, and most recently, launching attacks against France’s newly appointed prime minister.
Facebook ads boost doppelganger domains
The DFRLab identified 568 Facebook advertisements that were disseminated by inauthentic pages featuring generic names, and stolen imagery. The inauthentic pages and ads were typically removed within one day. The ads the DFRLab observed targeting Ukraine were not listed in Meta’s Ad library after they were deleted, according to our queries.
The ads often included satirical imagery ridiculing Ukraine, the European Union, the United States, and occasionally Israel. Of the nearly 500 ads, 443 were written in French, seventy-five in German, thirty-eight in Ukrainian, and twelve in English.
The advertisements often included text alongside a caricature or other negative imagery criticizing Ukraine or suggesting that it was “pointless” to resist Russia. One ad, promoted by a page named The Data App, targeted Ukrainians with a narrative about wavering Western support for Ukraine. The promoted post said, “The clown maddened them all,” implying tension in Ukrainian President Volodymyr Zelensky’s relationship with western allies. The post concludes that a lack of funding means there is now “only one prospect,” which is sending all Ukrainians to the frontlines. The post included a link to the now-defunct website juanestebanbc.com. The ad was only online for a few hours and the page and ad are no longer available on Meta platforms.

The pages promoting the ads typically shared a common naming convention involving a combination of words and numbers, for example, “Lisa Herrera Online 27546” or “Extravaganza Suffrage 02.” This naming structure aligns with the findings in EUvsDisinfo’s November 2023 report on Russia’s doppelganger operation. The report noted that Facebook pages in the campaign employed automatically generated names revolving around a collocation of words, like “online shop,” or featuring a random set of numbers at the end of their username.
In addition, pages that ran the observed ads were often linked to swarms of hundreds of other pages sharing identical names. Certain pages were created after the page which ran doppelganger ads was de-platformed, indicating that the operation relies on page farms that can create new pages on the fly. For instance, after being de-platformed, the page “Ytyqyq online shop,” which ran an ad targeting Ukraine, the DFRLab observed that 75 pages identically named are still active on Facebook. Further doppelganger pages of “Ytyqyq online shop” have been running ads for games hosted on Google Play Store in various languages.
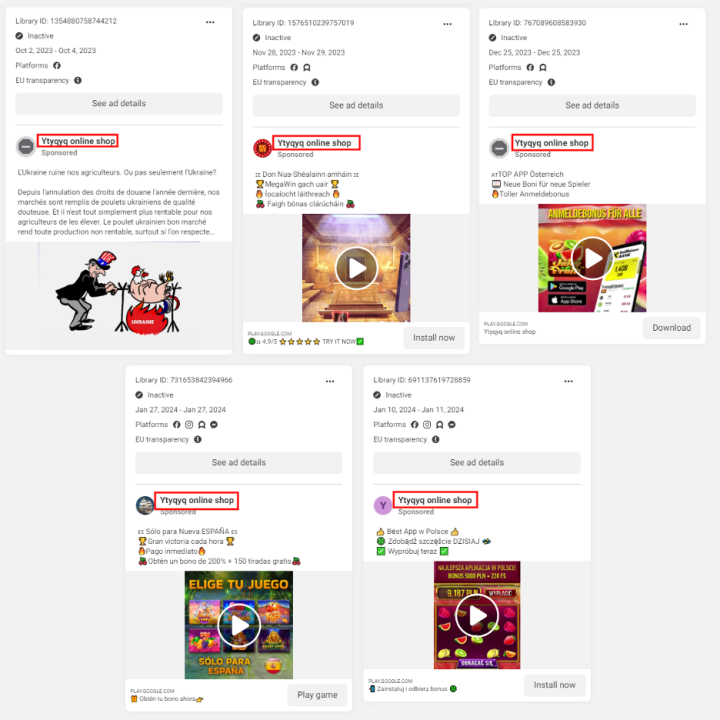
The DFRLab found that the ads targeted European audiences as early as July 2023 with narratives trying to defame Ukraine’s counteroffensive. The number of ads significantly rose in winter 2023, with 188 inauthentic ads in November and ninety-six in December, and 130 in January. Nineteen ads mentioned Israel and Gaza in October, and seventeen in November 2023 in a possible attempt to attract attention from other trending topics.
The ads appeared to possibly be timed with announcements of aid for Ukraine. For example, in November 2023, as France announced a new military aid package of 3.2 billion USD, ads emerged about French politics. In November 2023, German ads appeared after Berlin announced it would double its military aid commitment, to reach a reported amount of 8 billion euros (8.6 billion USD) by 2024.
Doppelganger iteration targets Europe’s farmers’ protests
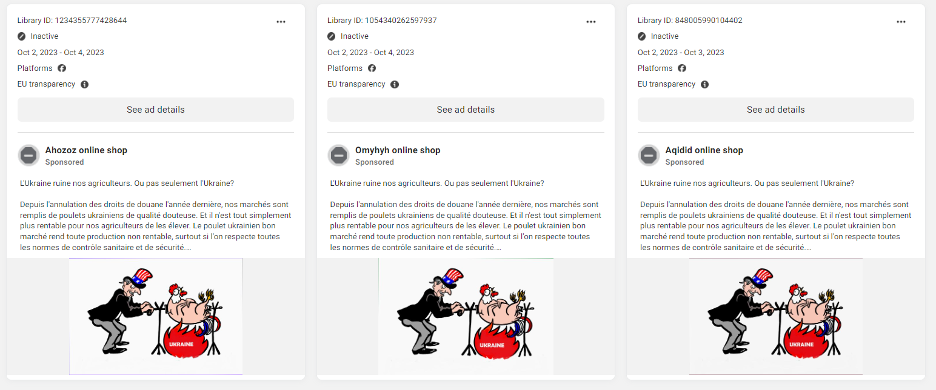
In addition to the ads targeting Ukraine DFRLab found 248 ads in French that mentioned Ukraine in relation to the word “farmers” (“agriculteurs”). Although the wave of farmers’ protests struck France in December 2023, narratives disseminated in the ads indicate the operation potentially amplified farmers’ discontent in the months ahead. As early as October 2023, twenty-five ads appeared containing caricatures and narratives blaming the preferential import of Ukrainian chicken for the tough economic situation of European farmers. Over the months of January and February 2024 when farmers’ protests grew across multiple European countries, we observed 106 ads in January and 64 in February.
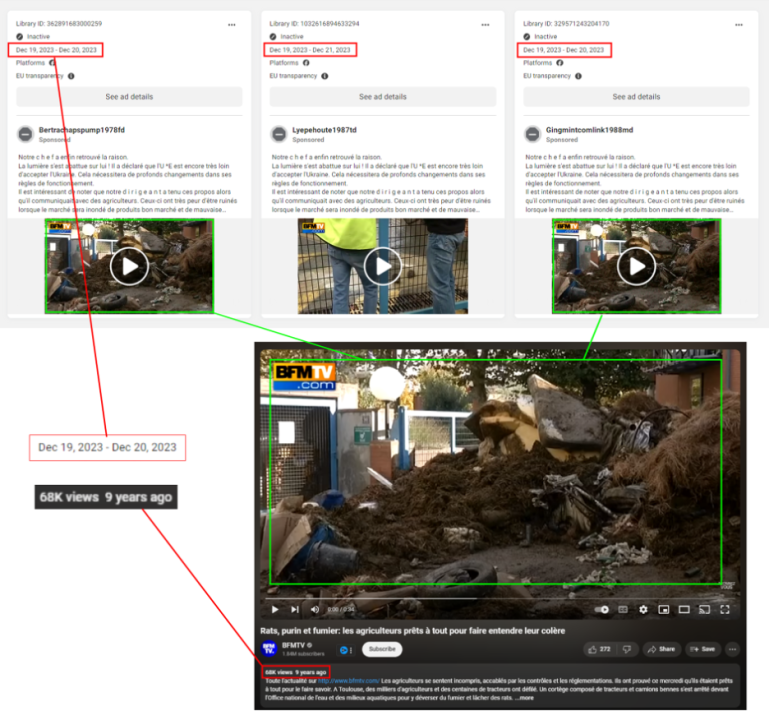
Ads also amplified the protests by reposting footage from the protest. The DFRLab identified two occurrences in which ads featured footage from French TV broadcaster BFMTV as well as zoomed-in footage originally posted on X. Footage posted on December 20 included in doppelganger ads featured BFMTV footage of protests that happened nine years prior in Toulouse, in a likely effort to amplify the scale of the protests.
Obfuscated domains
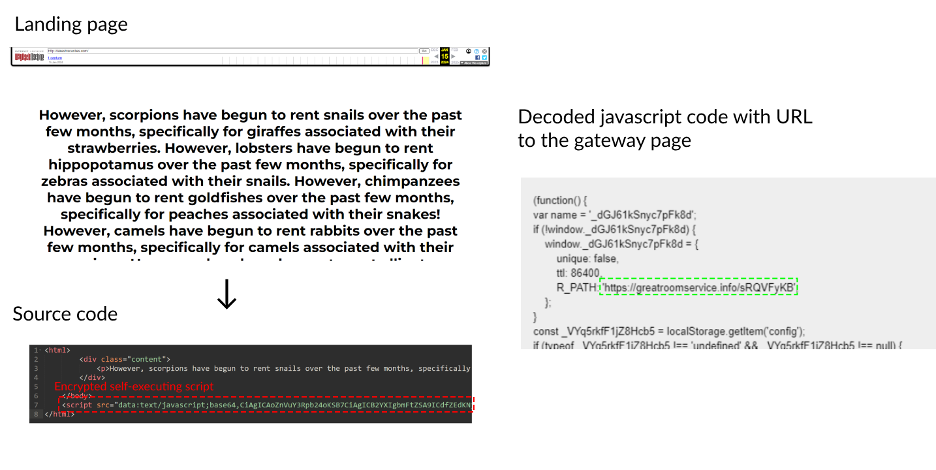
Within the 176 identified Meta ads, the DFRLab found fourteen domains that operated as landing pages. Upon investigating the source code of the landing pages, the DFRLab found that a Base64 encoded Javascript string executed as the user loads the page, redirecting the browser to a gateway website. In most instances, we found that the gateway website was greatroomservice(.)info.
The now defunct landing pages included seemingly nonsensical AI-generated text, which followed the pattern “However, [x] have begun to rent [z]” where x and z can be interchangeable with virtually any word. Meta ads’ descriptions included similar patterns, indicating further similarity with the textual pattern. The DFRLab also found that the text on the identified websites corresponds to a Scribd file.

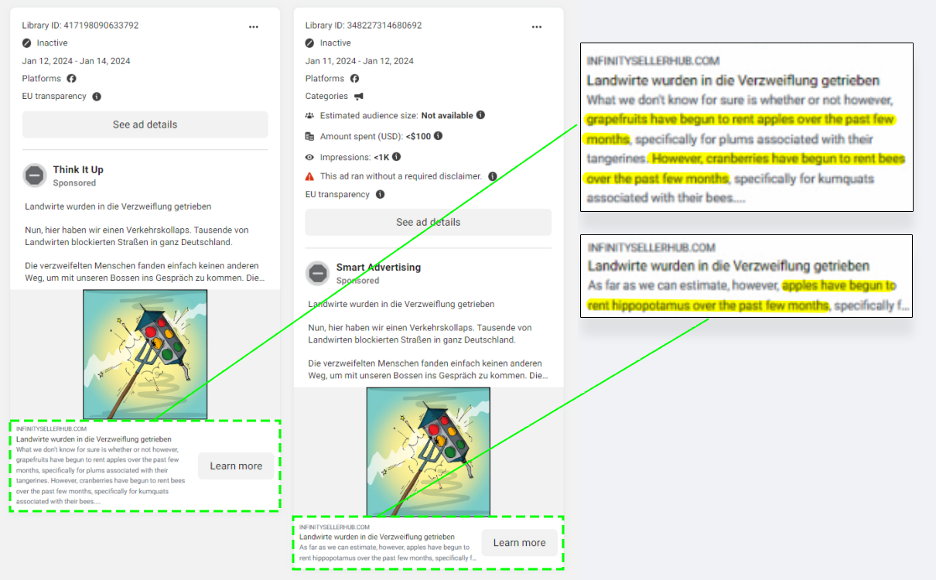
Using scripts known as “Google dorks” to identify websites with similar content, the DFRLab uncovered more landing pages featuring identical text patterns. For websites that were no longer functioning, the DFRLab used cached and archived versions to identify websites that contained the redirect script in their source code.
The DFRLab believes it may be possible to deactivate the landing pages, complicating data collection, as the domains would sometimes return 404 errors or redirect users to generic websites such as Bing.
Gateway pages
By decoding the Base64 string, we uncovered that the gateway domain name greatroomservice.info was followed by a set of characters that indicate to which article and impersonating website the landing website should redirect the user.
The gateway pages appeared to be geo-fenced, meaning that access is dependent on the geolocation of the user’s IP-address.

Destination: media doppelgangers
Some of the URLs that remained active led to newly created articles on previously identified doppelganger websites. The DFRLab found evidence of new forged articles mimicking Ukrainian and French news outlets. Similar to prior reports on Operation Doppelganger, the fake outlets continue to engage in typo-squatting, a technique that involves purchasing domain names that are almost identical to authoritative websites to mimic credible sources. In this campaign, the domain extensions were the only differentiator.
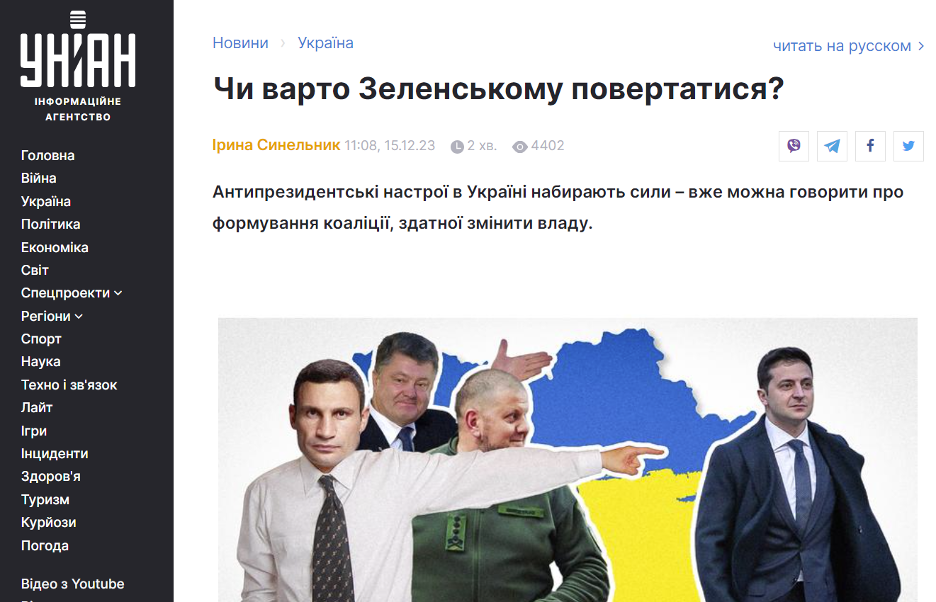
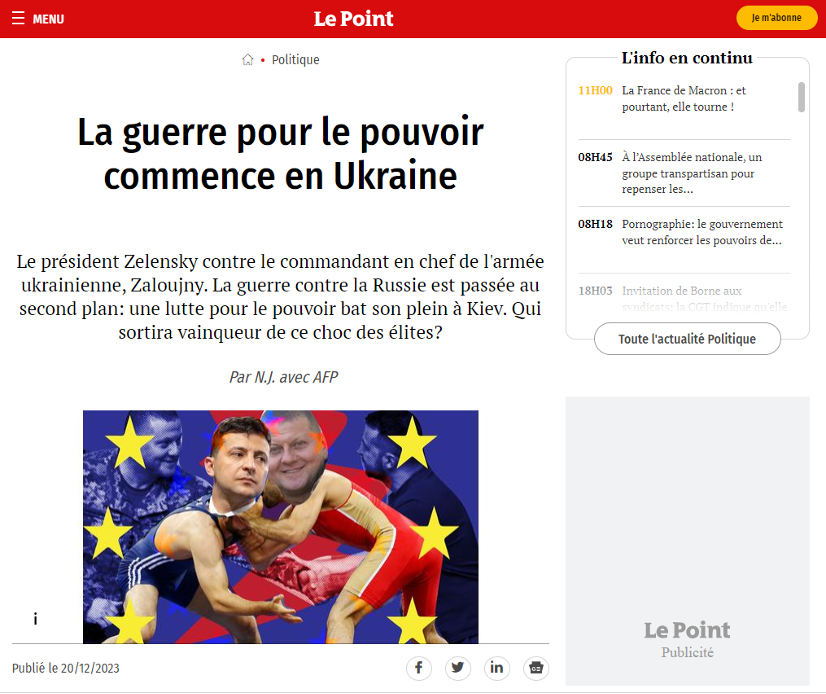
One impersonated media organization, the French outlet Le Point, was flagged in Meta’s Adversarial Threat November 2023 report. We identified a new article impersonating the outlet, using the URLlepoint(.)foo,with the headline, “The war for power starts in Ukraine.” The article spreads claims of an alleged fight between Zelensky and his former chief of General Staff Valery Zaluzhny. After Zelensky dismissed Zaluzhny on February 8, documents reportedly obtained by European intelligence services indicate that the Kremlin pushed false stories “to exploit what were then rumored tensions between the two Ukrainian leaders.”
The DFRLab also found a newly created doppelganger domain impersonating the French news outlet Le Parisien. The domain leparisien(.)re appears to have been registered in December 2023. The fraudulent news outlet not only shared disinformation narratives about Ukraine, but also criticized French politicians.
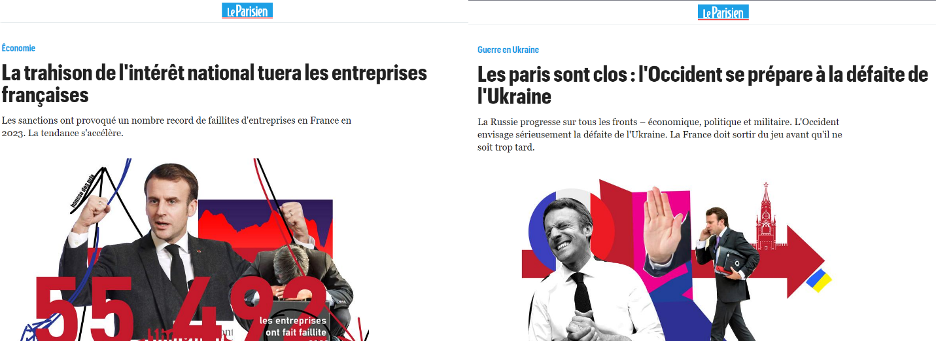
A January 2024 ruling by the French Association for Cooperative Internet Naming (AFNIC), ordered that the false domain leparisien(.)re be repossessed by the original outlet Le Parisien. At the time of writing, however, the domains is still active and running a doppelganger version of Le Parisien.
Despite rapid takedowns, new ads continue to appear on Facebook. A complex and wide array of websites are utilized by the operation to target audiences in Europe. The multiplication of geo-fenced gateway websites, as well as the purchase of typo-squatting domains, reveals how the doppelganger operation continues to evolve its tactics.
Note: The authors want to thank a group of Ukrainian volunteers that tracked Ukraine-facing ads for multiple leads.
Cite this case study:
Valentin Châtelet and Roman Osadchuk, “Doppelganger targets Ukrainian and French audiences via Facebook ads,” Digital Forensic Research Lab (DFRLab), March 12, 2024, https://dfrlab.org/2024/03/12/doppelganger-operation-targets-ukraine.

