Crypto-scam hosts pop-up livestream featuring a deepfaked Elon Musk
‘Traveling Circus’ livestream raked in $50,000 over the course of two hours by featuring a deepfake of Musk to solicit investments
Crypto-scam hosts pop-up livestream featuring a deepfaked Elon Musk

Over a period of two hours on June 18, 2024, scammers raised more than $50,000 in cryptocurrency after orchestrating a YouTube livestream featuring a deepfake of Elon Musk soliciting investments. Speaking in a stranger-than-usual cadence, the synthetic Musk promised “automatic doubling” for all viewers who “acted promptly” in making cryptocurrency deposits. The operation’s breadth extended beyond YouTube as the scammers sought to lure users off the platform to deposit Bitcoin, Ethereum, and Dogecoin in wallets linked by a QR code displayed within the video. In tracing the origins of the falsified YouTube livestream, we discovered an operation in which scammers target YouTube channels with a high subscriber count and rebrand them to impersonate the official Tesla YouTube channel before launching a livestream. It is not clear what, if any, role the original channel owners play in the operation.
Deepfakes depicting Musk and other well-known figures are widely used to facilitate online schemes that prey on unsuspecting users and lure them into making monetary transfers to fraudsters. As reported in The New York Times, these deepfake scams, sometimes promoted via sponsored social media posts, have successfully convinced users to make deposits of tens or hundreds of thousands of dollars. These deceptive scams employ sophisticated AI to cling to the appearance of authenticity, sometimes emerging in tandem with a real news event in order to boost their livestream audience. These cases illustrate the vast potential for deception and fraud, whether by an individual or a criminal enterprise, as AI services facilitate the creation of difficult-to-discern imagery and anonymous cryptocurrency transfers grant the operators a level of opacity that permits the scheme to play out in a continuum, from one channel to another, in a sort of traveling circus.
Deepfake-enabled deception has become increasingly common as the technical knowledge (dataset collection, cleaning, and training), hardware (powerful GPUs capable of performing intensive training), and software (esoteric face-swapping codebases and dependencies) required to produce deepfakes is democratized and made increasingly accessible through user-friendly software and commercial applications. However, deepfakes on their own do not pose the single greatest threat to online spaces, as is sometimes implied in public discourse on the topic. Scams such as these demonstrate that deepfakes can be coupled with existing modes of platform manipulation to exploit platform verification, imitate public figures, inflate engagement metrics, and gamify trending algorithms, creating a malign campaign which is greater than the sum of its parts.
The deepfake
Over the course of the hours-long livestream, the administrators looped a 200-second video of a Tesla mainstage event manipulated to depict Elon Musk reciting a script which directed users to deposit their cryptocurrencies to wallet addresses located at telsa-bitcoin.com. The script was reminiscent of the kind of text generated by large language models (LLMs) and appears to have followed a bulleted list of instructions as the deepfake vocalized headers such as “Key Moments to Maximize Winning Potential,” “Detailed Instructions Segment,” “Q & A sessions,” and “Closing Announcements.”
The deepfake promoted a sense of urgency, encouraging viewers to seize the opportunity, and instructed people who were not familiar with cryptocurrencies to get involved. Comments were disabled on the livestream, leaving onlookers little recourse to deter others from falling victim to the scam. The only comments in the livestream chat window were from a moderator account named “Elon Musk” that made claims such as “Over 750 BTC & 5,300 ETC have already been sent to livestream viewers.” The username and profile picture of the “Elon Musk” moderator account differed from the “Tesla” channel that hosted the live stream, indicating that various accounts appear to be involved in the operation of the scam. It may be possible that the Musk account, whitelisted to post in the livestream chat, is associated with the individual orchestrating the scam. Analyzing the metadata collected from this chat indicated that the “Elon Musk” account belonged to the YouTube account with the ID: ChwKGkNKVHZ4cWFPW9ZREZlb04xZ0FkWUVvQ1Bn. Once the proper YouTube URL was prepended to the account ID it resolved to the account @Whome-hq5sq.
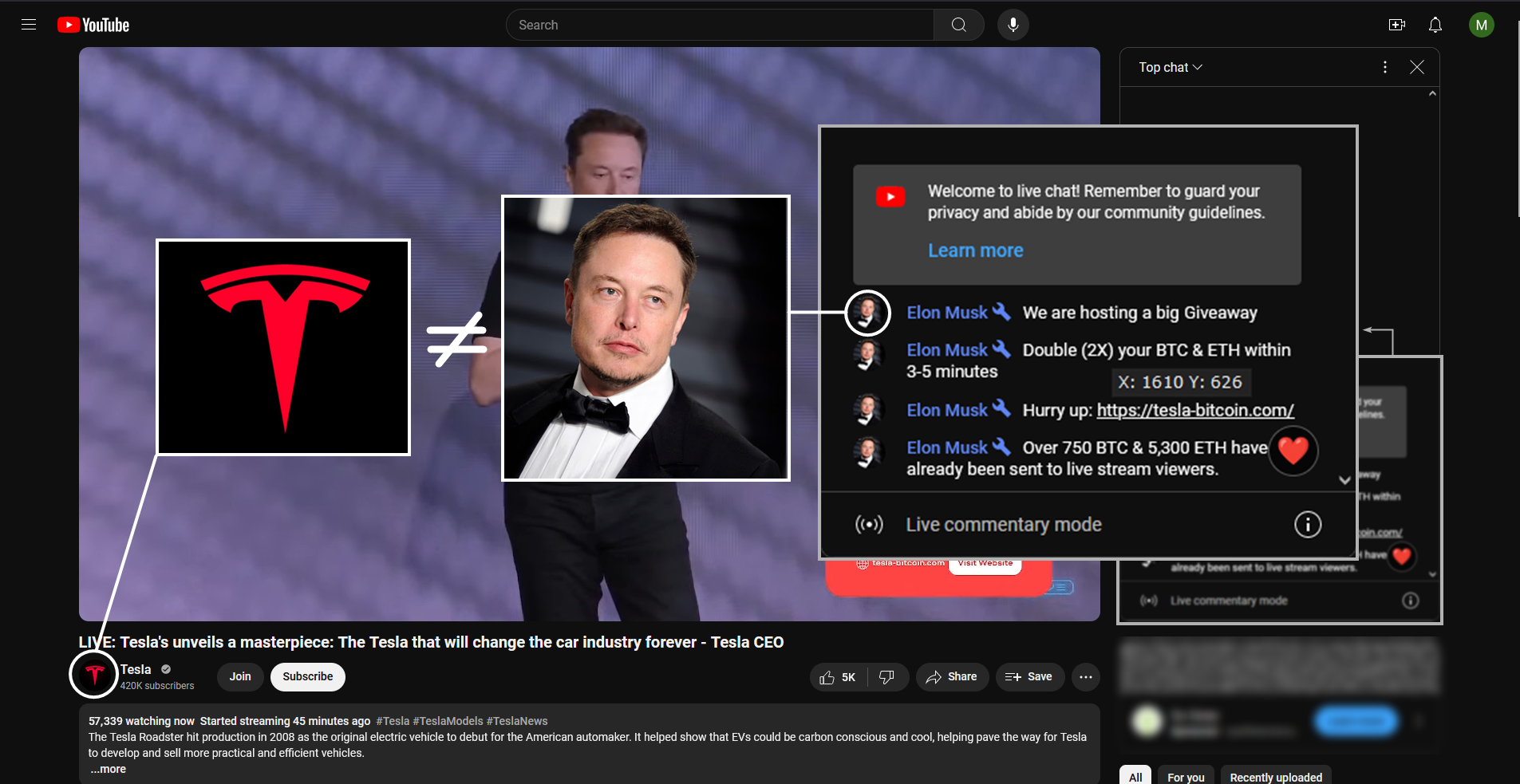
Crucially, the video directed viewers to scan a QR with their smartphones. This would draw potential victims off-platform – a common tactic used in deception campaigns to lure users away from vigilant platform moderation – but also off their computers entirely and onto their mobile devices, further distancing them from any potential scam mitigation measures.
Total channel takeover
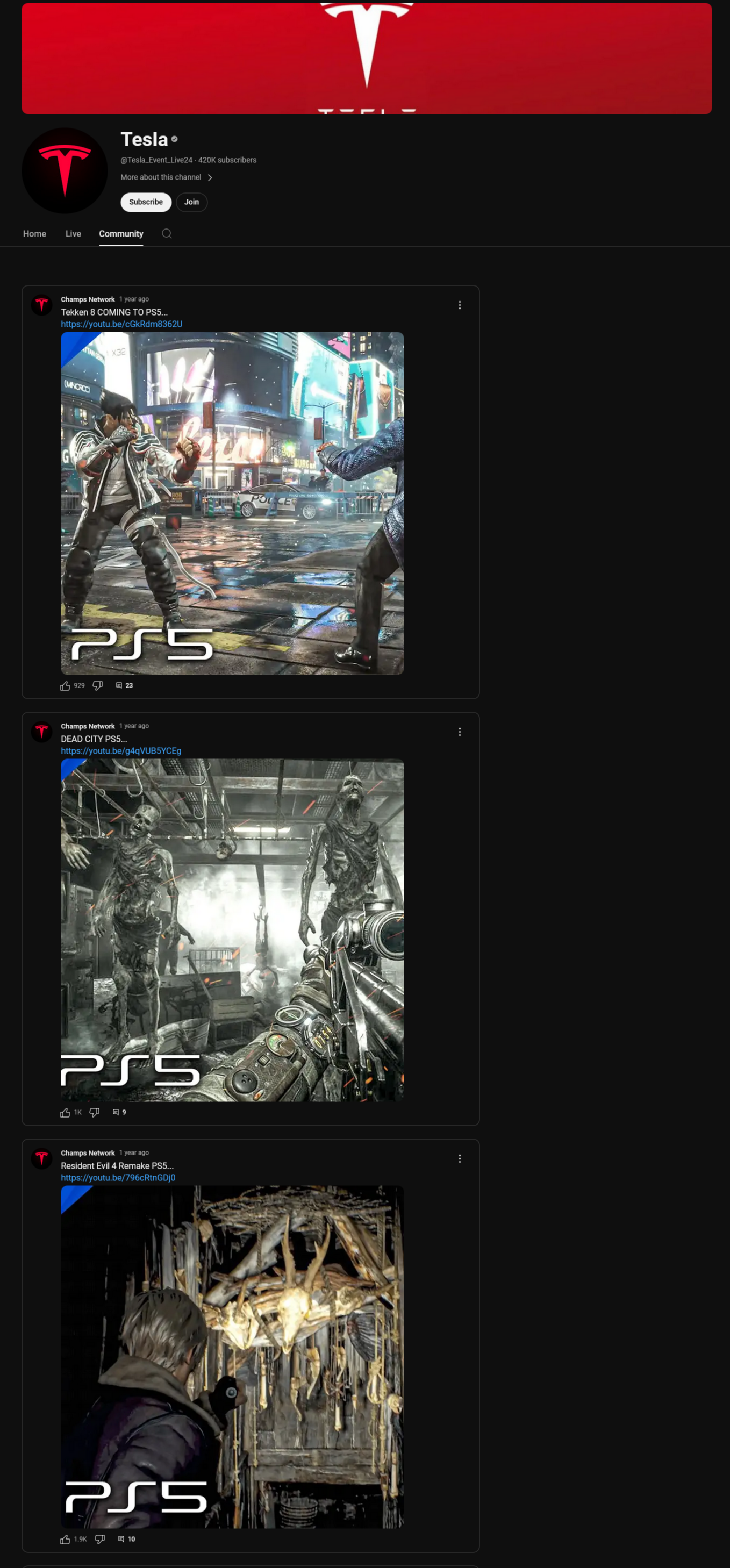
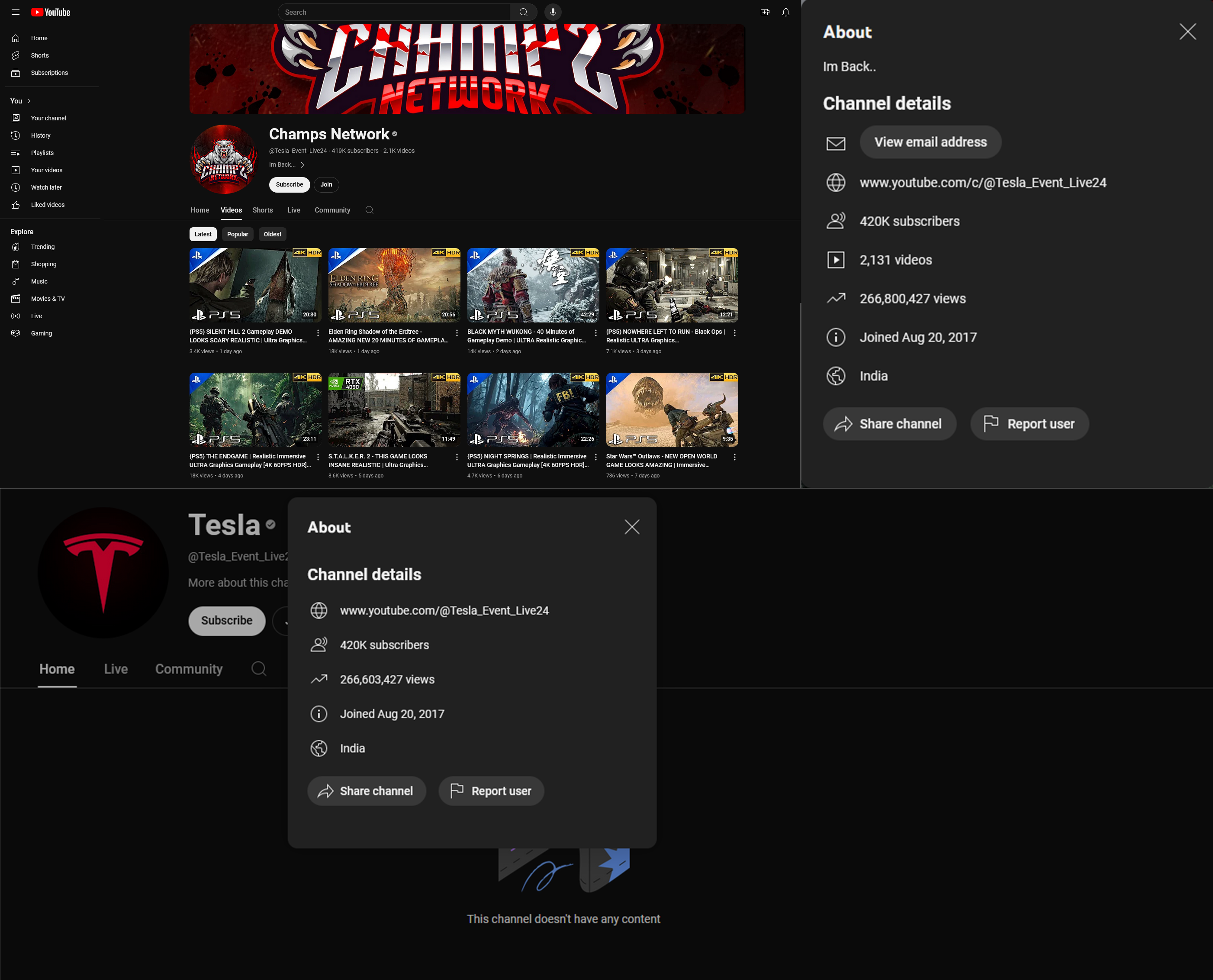
The YouTube channel which hosted the livestream was later identified as @ChampsNetworkHD, which typically posts gaming content. Appearing with the handle @Tesla_Event_Live24, the channel was thoroughly rebranded to imitate the official Tesla YouTube channel. During the live stream, all the channel’s videos were de-listed, leaving the livestream as the sole content on the channel. Temporarily renamed “Tesla,” the channel was also branded with the Telsa logo and affixed with a Tesla banner. It had 420,000 subscribers at the time of the livestream; notably, it had also been verified by YouTube, displaying a small checkmark badge next to the “Tesla” name, which many users associate with authenticity. The only indication that the channel was masquerading its identity was found on the “community” tab, which remained unchanged and featured previously published gaming content.
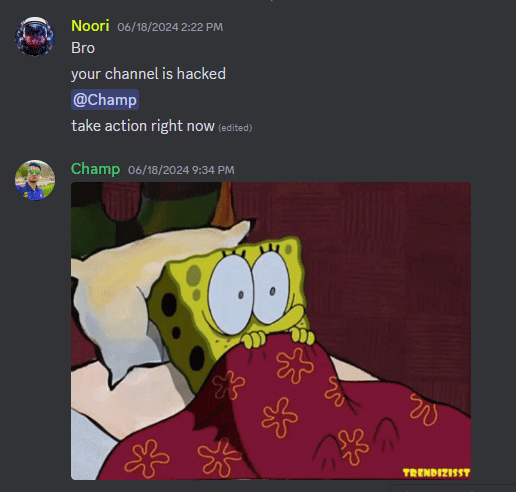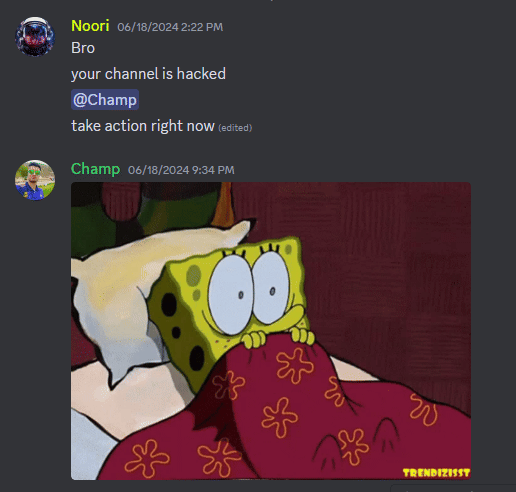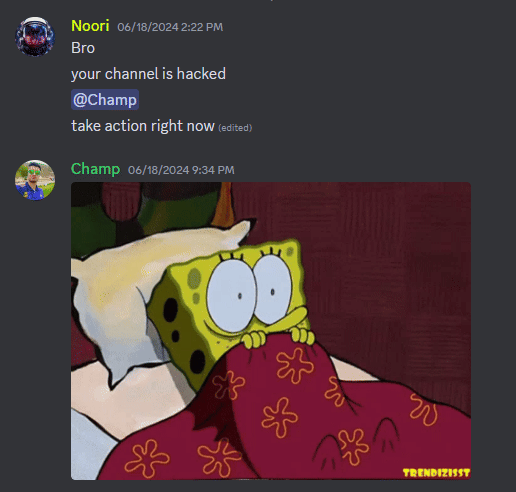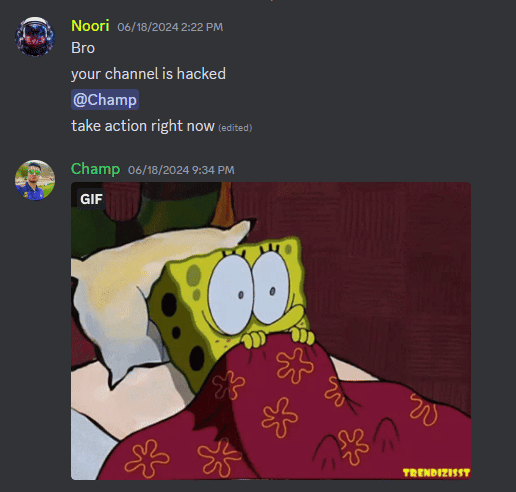
DFRLab researchers became aware of the scam at around 6:00 PM ET on June 18 after it was recommended to a researcher by YouTube’s algorithm. The earliest identified report of the livestream scam was made by a user on the Champ’s Network Discord server at 2:22 PM ET urging the channel owner to take action in light of the apparent “hack.”
In total, the livestream ran for more than seven hours until 9:33 PM, restarting every two hours by introducing a countdown clock before resuming the deepfake loop.
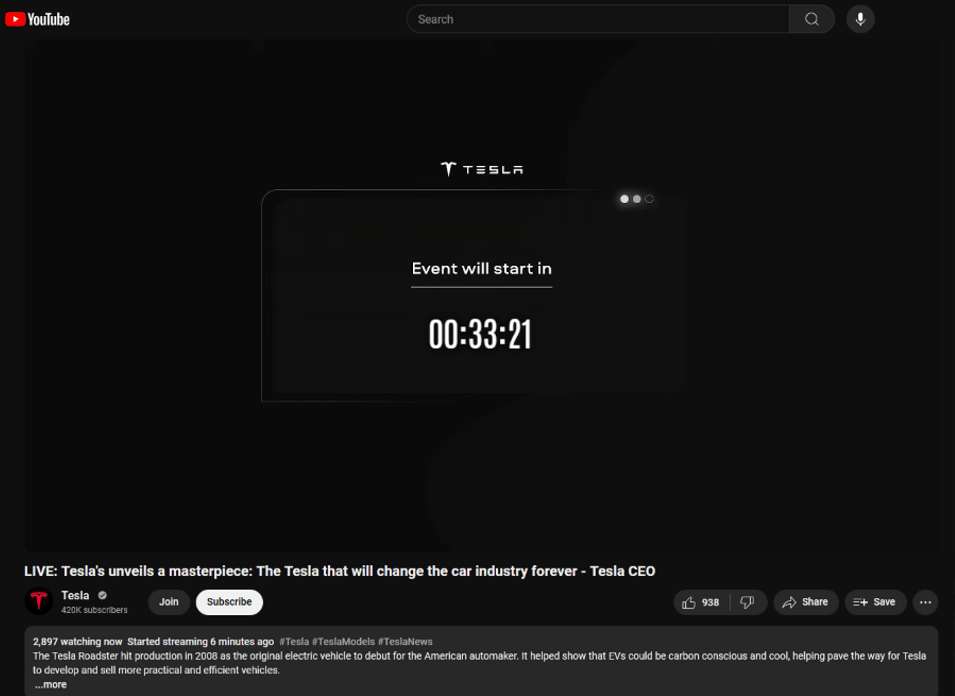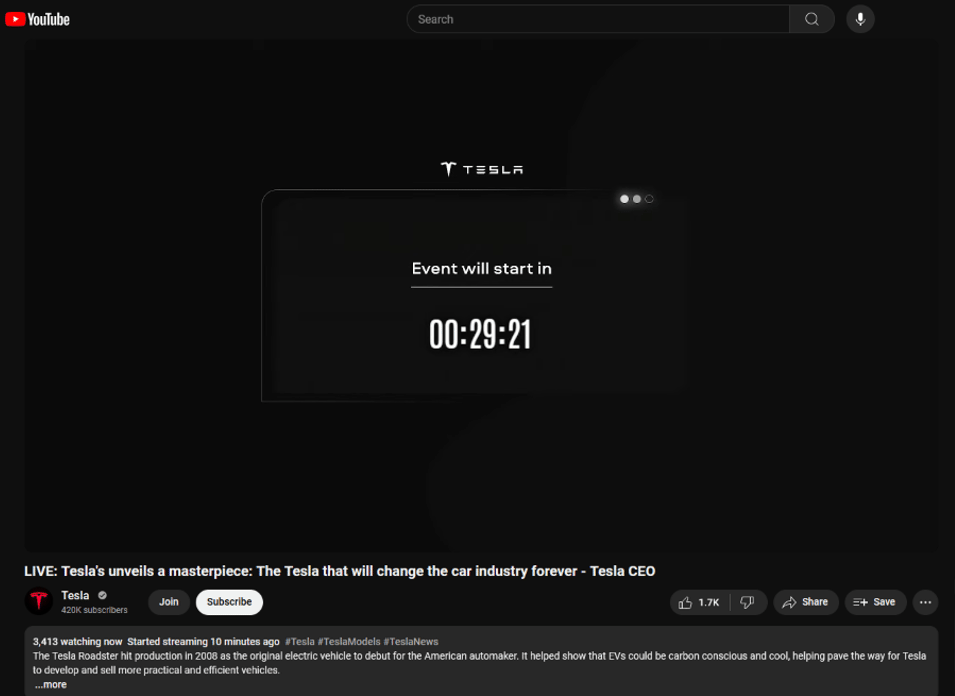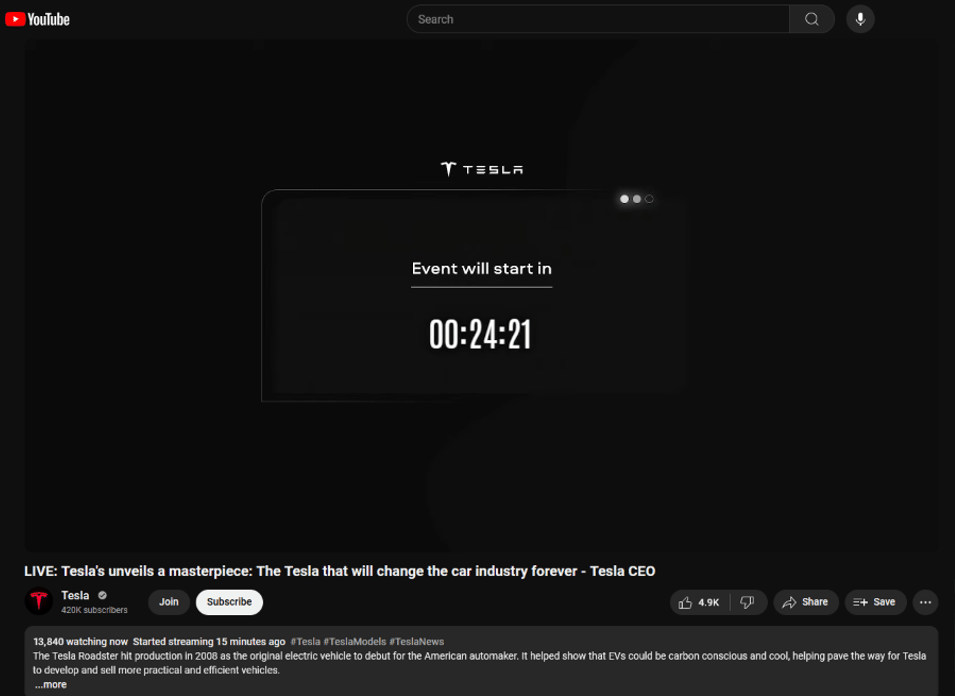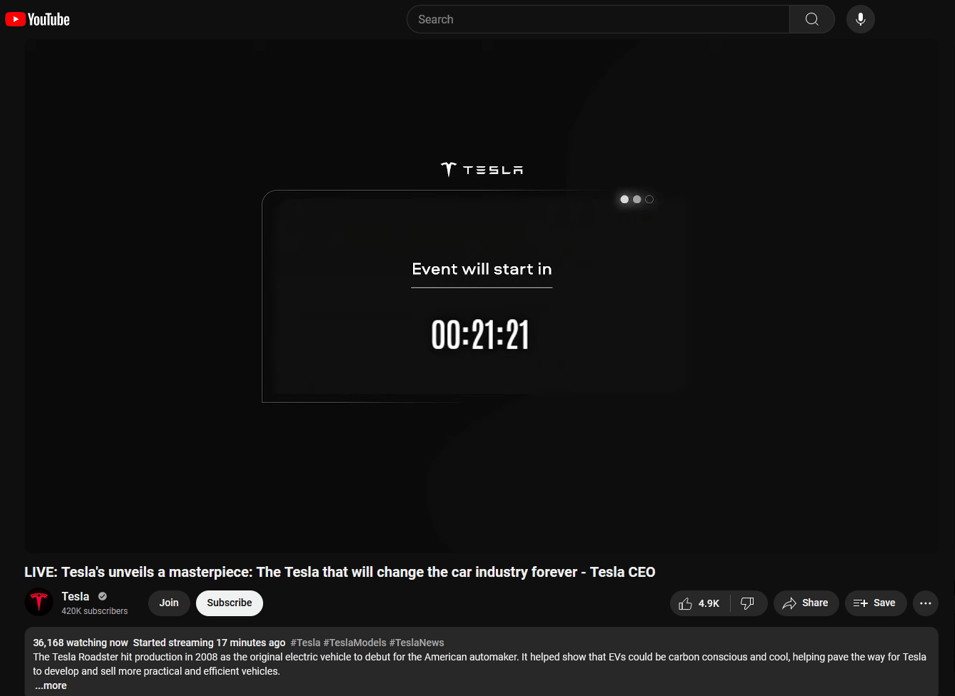
The livestream was highly attended. Over the course of the DFRLab’s observation of the livestream, as many as 81,000 concurrent viewers were observed streaming the event.
Cognizant that the viewership metrics were likely as inauthentic as the content being peddled, the DFRLab fashioned a research methodology using a timed screenshot utility to capture an image of the viewership metrics every minute. Afterwards, the 223 images captured during the livestream were processed to extract numerical values using optical character recognition (OCR). Google’s Tesseract OCR turned the 223 screenshots into numerical data, allowing the DFRLab to merge the unique creation dates of each screenshot to create time series viewership data.
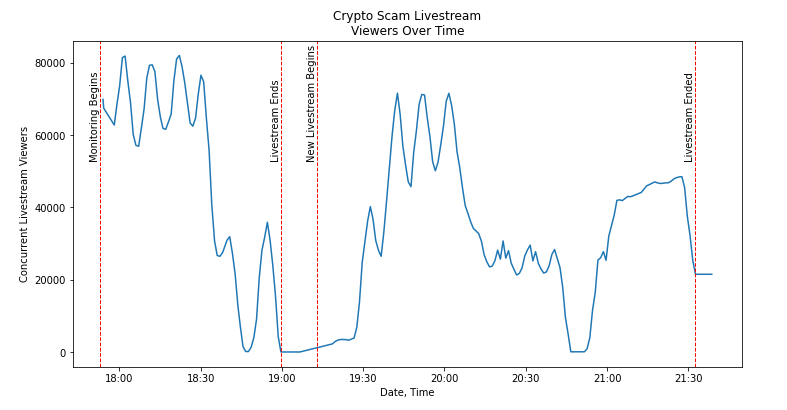
In the world of inauthentic engagement, livestream views are among the most challenging figures to manipulate. As opposed to follower count, likes, and shares, concurrent livestream viewers require persistent activity from bot accounts to “view” the livestream for inflated metrics to be effective. This can be a costly endeavor and raises some questions about the actors behind the scam, who appear to be both competent and sophisticated. It is possible, if not likely, that the proprietors of the YouTube channel which hosted the livestream were not the masterminds behind the scam.
Through structured Google searches, the DFRLab was able to identify three aliases which traced back to the “Elon Musk” account (@Whome-hq5sq) that commented during the livestream: “mr4dm1n,” “mrstmmusic,” and “notepad.”
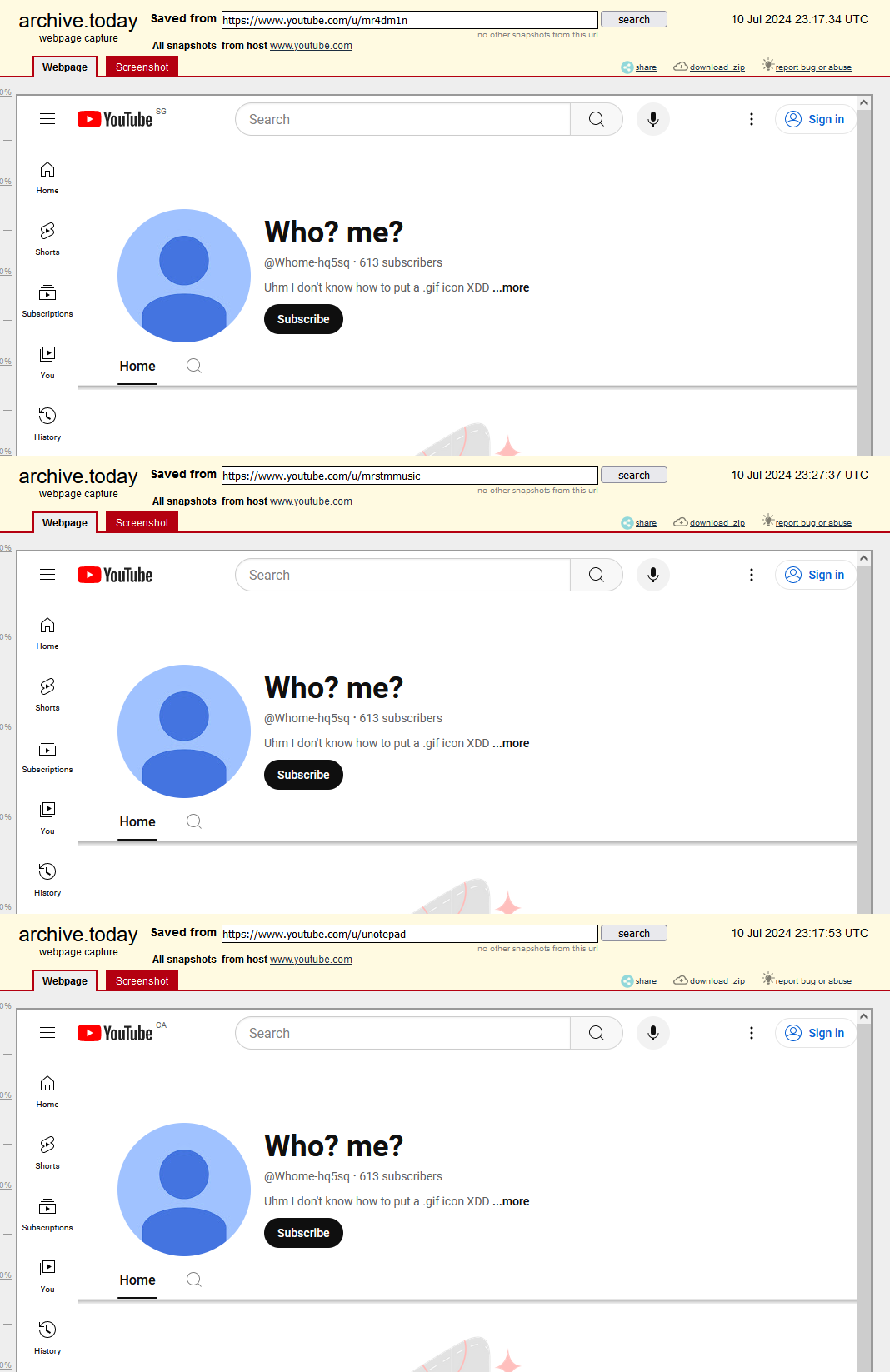
A Discord account claiming ownership of the YouTube channel “mr4dm1n” was identified posting in the Champ’s Discord Server under the profile named “the rvw” (full name “the_rvw_v2”) soliciting advice from Champ.
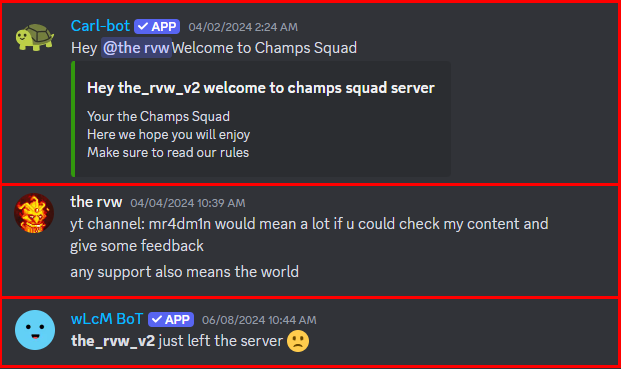
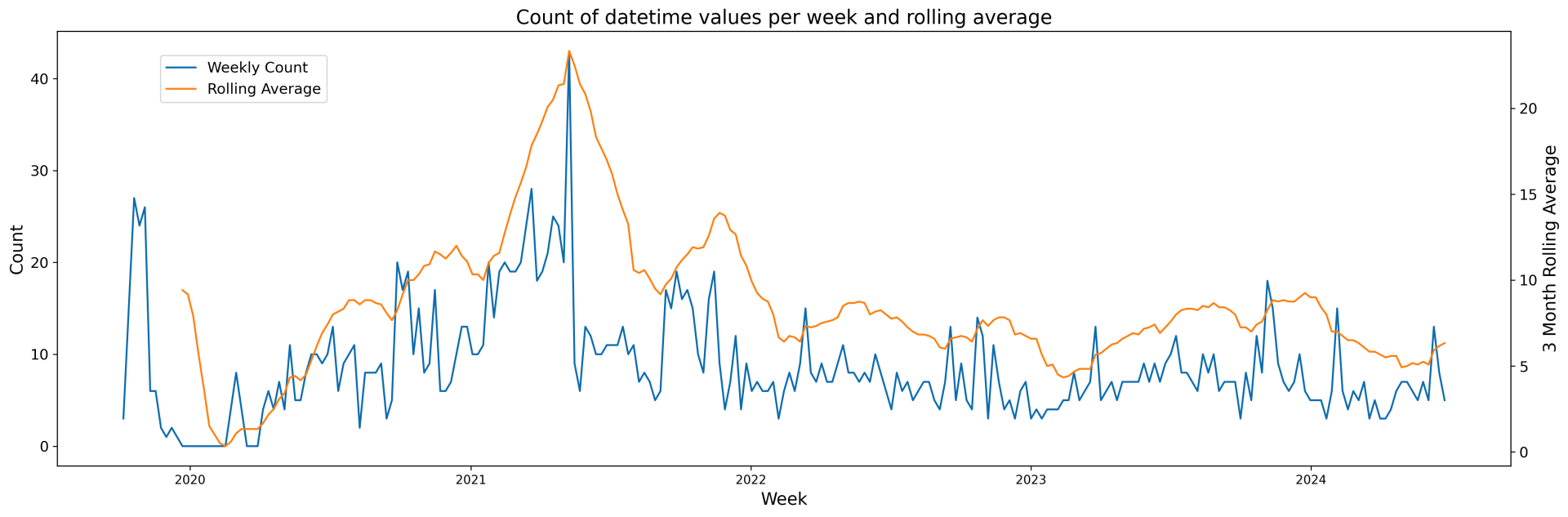
Despite possible facilitation from “mr4dm1n” in conducting the scam, the normal operation of the “Champs Network” appears to be a sophisticated content mill designed to gain advertisement revenue through farming views with video game trailers and gameplay footage. Posts appear very frequently; over the course of the channel’s lifetime it has averaged 8.6 videos per week, though its rolling average generally exceeds that.
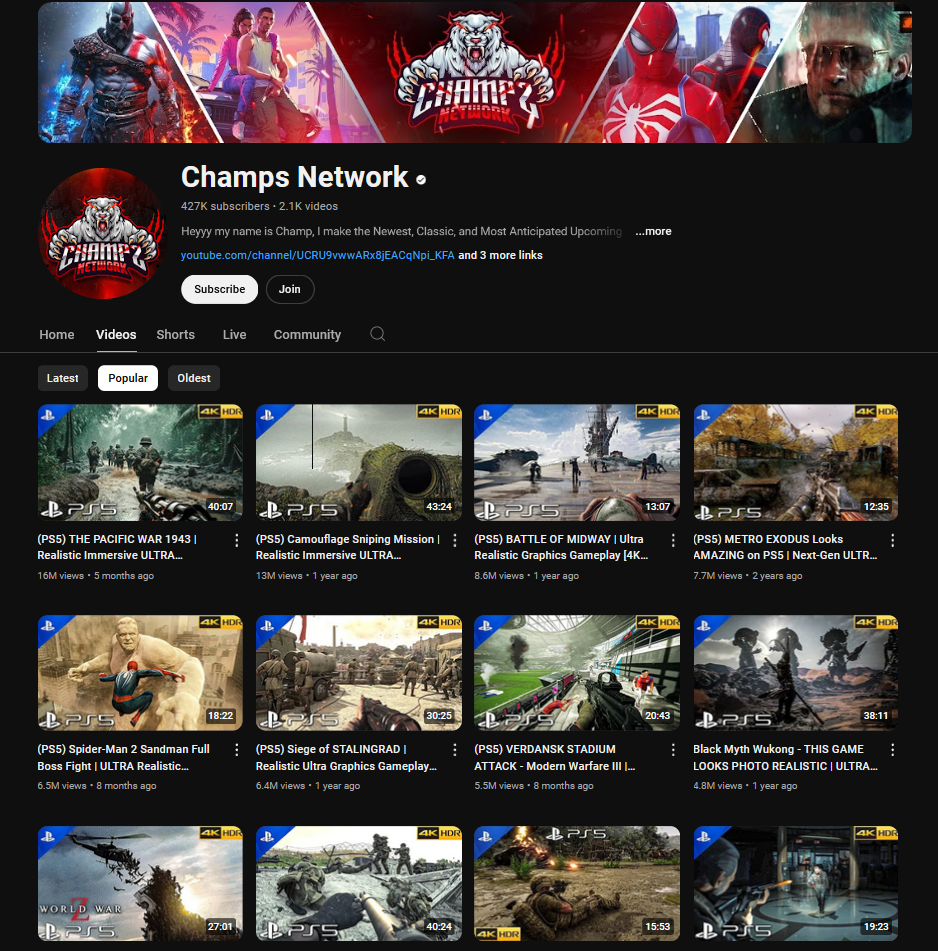
Almost all of the videos posted to the “Champs Network” YouTube channel follow the same formula: a gameplay video or trailer, a thumbnail including PlayStation branding in the top left and bottom left, “4K HDR” pinned to the top right, and a generic description including buzzwords such as “Ultra Realistic,” “Ultra High Resolution,” ”Immersive,” “ULTRA Graphics,” “4K 60FPS HD,” and the like, which may indicate that the content is systematically uploaded.
The money
The QR code which viewers were advised to follow off platform routed traffic to tesla-bitcoin.com, a now-defunct website with modern branding and a ticker showing fake transactions of hundreds of thousands of dollars in cryptocurrencies.
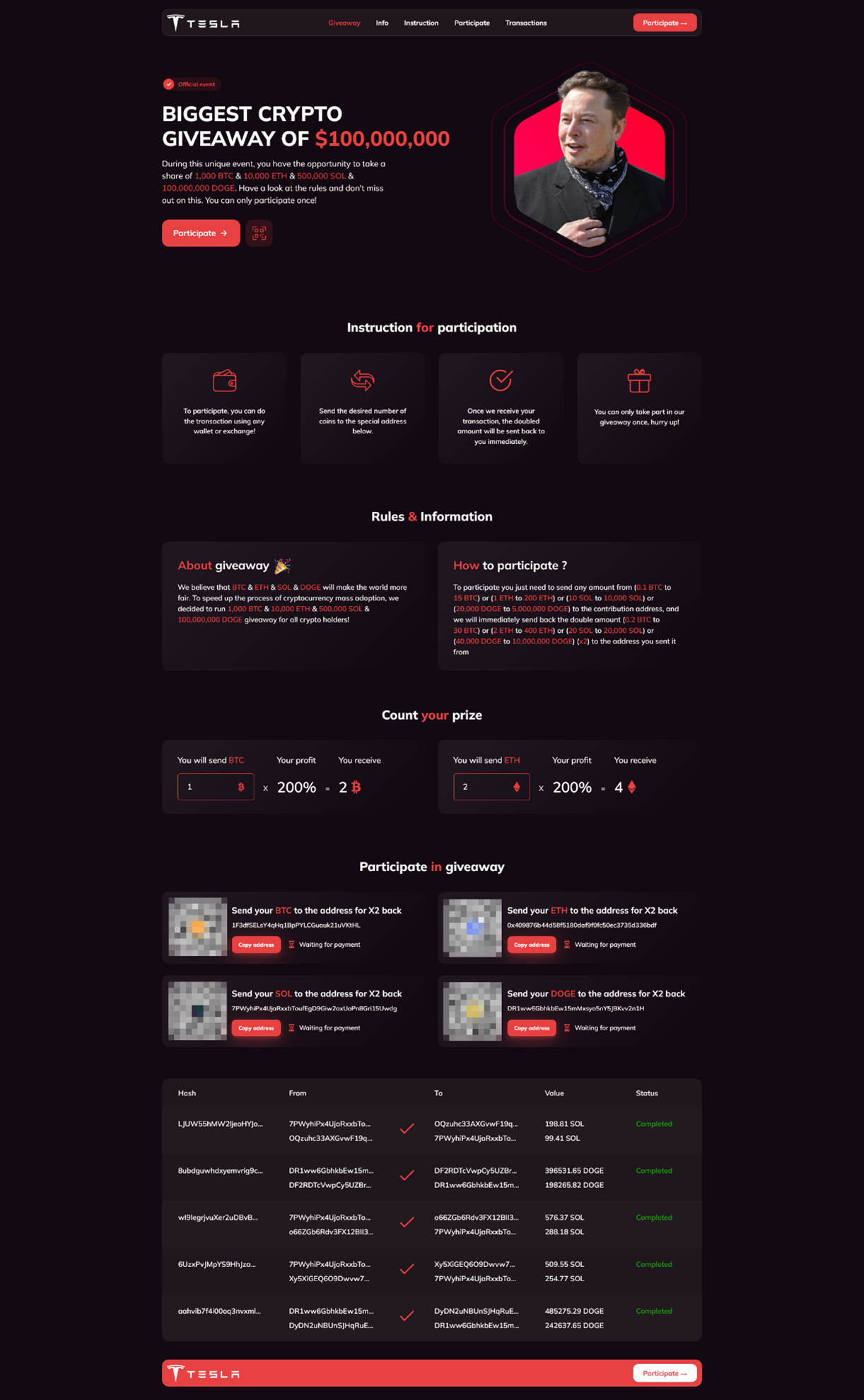
Over the course of the livestream, some of crypto-wallets linked to the scam’s off-platform site were substituted for fresh wallets, likely with the intention of hiding the one-way nature of transaction and the clear absence of any “automatic doubling” as advertised. Shuffling wallets also served to obfuscate the withdrawal of currencies to more permanent addresses. A review of the crypto addresses which the DFRLab identified as recipients of deposits coinciding with the livestream shows that a total of USD $50,537.19 was collected across Bitcoin ($40,289.91) [BTC 1, BTC 2], Ethereum ($3,825.22) [ETH 1], and Dogecoin ($6,422.06) [DOGE 1, DOGE 2] wallets.
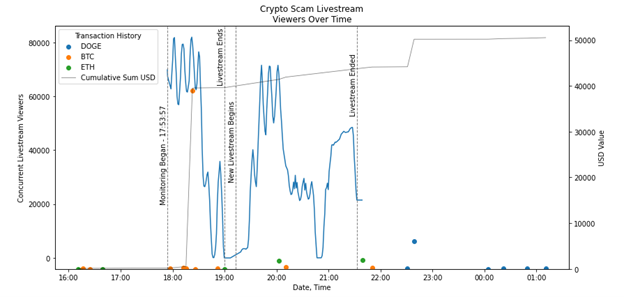
Transactions from the various wallets observed by the DFRLab indicated that the currencies were being pooled in secondary wallets before being divided among even more wallets. Though further research is required to trace transactions back to a central source, given the nature of these anonymous currencies, the likelihood of deriving some successful attribution is modest at best.
Channel restoration
Shortly after the livestream ended, “Champs Network” began to restore their channel. Suddenly, the channel which previously had zero videos was host to 2,131 videos dating back to 2019. The channel’s “about” blurb, which was previously blank under the Tesla branding, was briefly replaced with “Im Back..” a notable addition raising the possibility that the “Champs Network” owner handed over the account to a third party to orchestrate the scam, though it is not in itself proof of them doing so.
The channel restoration coincided with engagement from the channel owner on Discord, who posted a gif exclaiming that “THE KING IS BACK.”

Further, the channel owner replied to YouTube comments. One comment posted on a four-year-old video suggested that the channel had been hacked. The channel owner, still posting under the “@Tesla_Event_Live24” pseudonym, dismissed any concern by stating “not a prob 😏.”
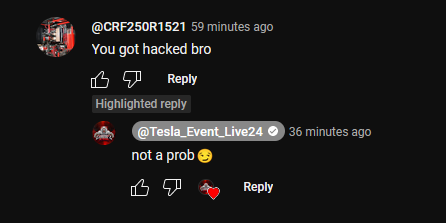
The cavalier attitude towards the day’s livestream scam raises additional questions about the administrator’s potential involvement or complacence.
Traveling circus of crypto scams
Two months since the original livestream aired, @Tesla_Event_Live24, the imitation Tesla account used to rebrand the Champs Network for the livestream scam, now directs to a different channel, “Leo – Kun,” with an even greater subscriber base than the Champs Network. Boasting more than 631,000 subscribers, the YouTube-verified “Leo-Kun” uploads stick-figure animation videos tailored to an adolescent audience. Entrance into the community Discord server stipulates users be at least 13 years old to participate.
According to recent posts from moderators in the Leo-Kun Discord, the channel was allegedly hijacked by hackers who used the page as a platform for a livestream scam. A moderator posted at 4:06 PM ET on June 21, 2024, claiming they had not conducted the livestream and cautioned community members not to engage with any of the content on the stream.
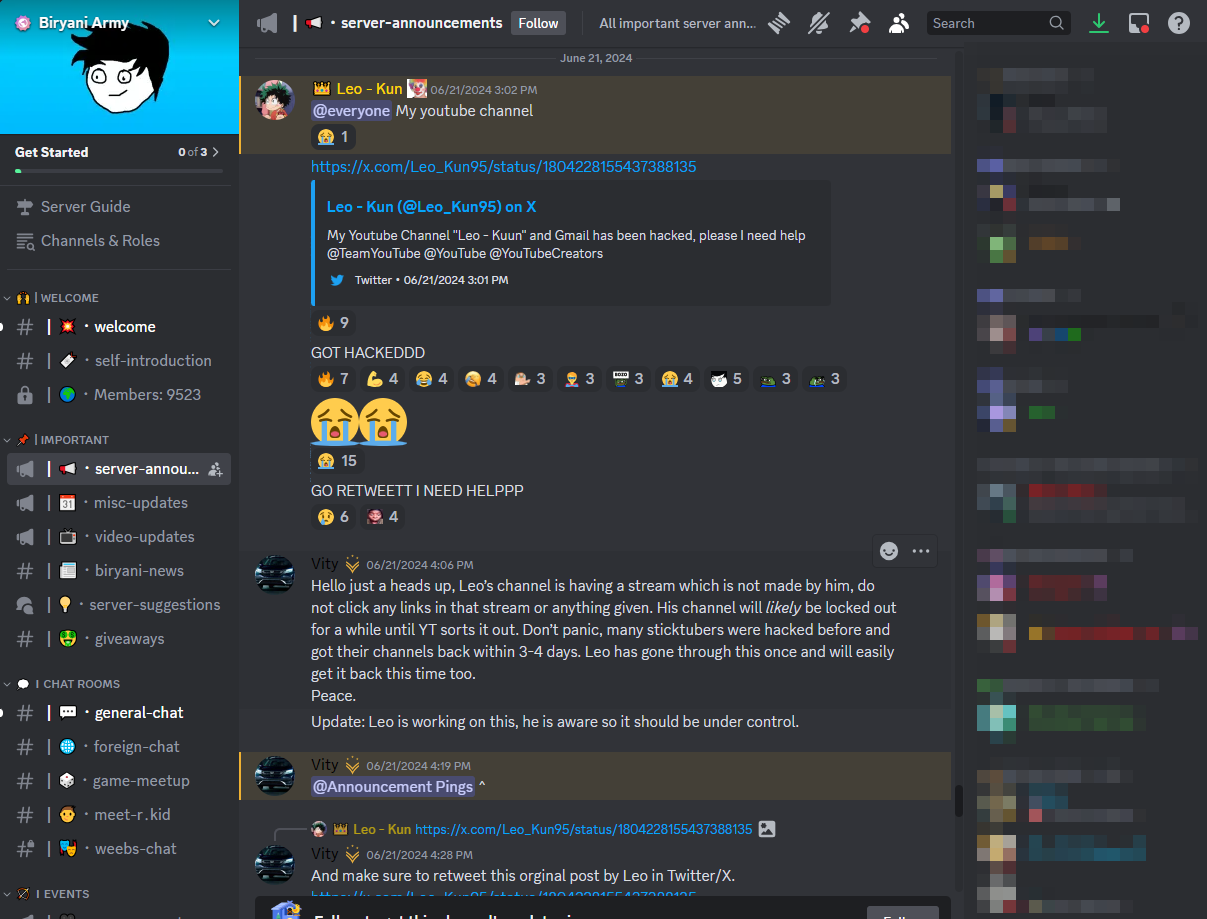
Unlike Champs Network, the Leo-Kun account owner took to X, the platform formerly known as Twitter, to report the hack to YouTube staff. The replies on X indicate that this is not the first time the account has been hacked, with some commentors expressing their concern, including one commentor cautioning the account owner to “be a little careful x).”
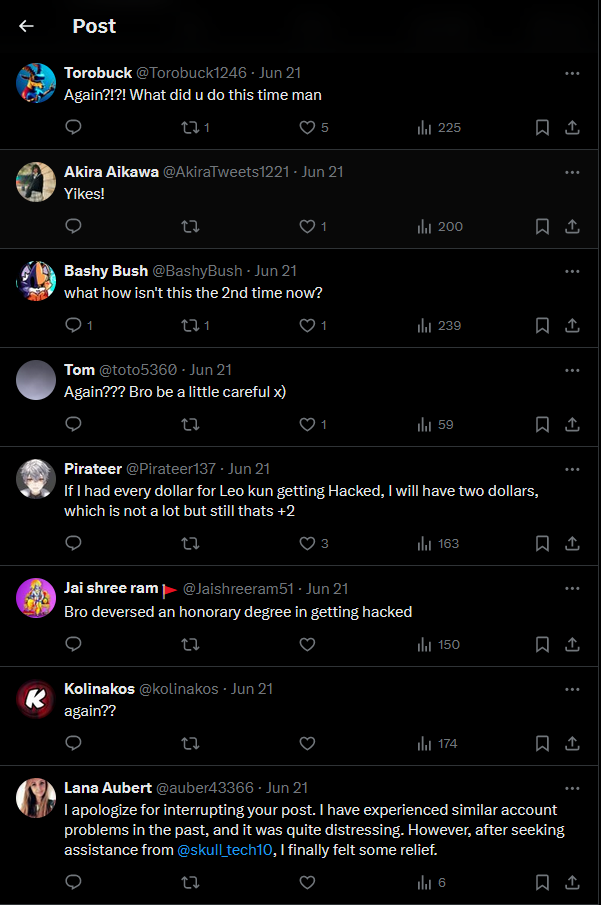
The following day, on June 22, the account was restored, though the owner has not yet reverted the channel’s handle from @Telsa_Event_Live24. In a follow-up post on Discord announcing the owner had regained control of the channel, the channel owner stated they had lost their verified badge because of the hack, though this did not appear to be the case at the time of writing.
Judging by the sophistication of this operation – the likely artificially inflated livestream views, the movement of cryptocurrencies and rotation of wallets, the rebranding and restoration of channels, and the relatively high-quality deepfake – it would suggest that the perpetrators behind the scam are not the channel owners. It is more likely that scammers solicit channels which meet the requirements to enable a livestream to trend on YouTube. It is also possible that this scam operates as a sort of traveling circus, donning verified and well-patroned channels for an evening of deepfake crypto-scamming and then returning them before anyone is the wiser. In this hypothetical scenario, channel owners may earn a cut of the scam’s proceeds before the scammers move on to the next channel.
While deepfakes are sensational, harmful, and novel in their own right and often the focal point of reporting, they do not inherently pose the single greatest threat to resilient online spaces. Outrage surrounding deepfakes as the pinnacle of deception is not wholly unwarranted, but it is important to keep in mind that hybrid approaches, which masquerade and artificially amplify false or misleading content through traditional deceptive practices can be leveraged to multiply a deepfakes’ capacity to deceive. In this way, we can begin to see deepfakes as an escalation of existing threats, and, in turn, the grueling and resource intensive task of deepfake detection becomes just one of many ways to mitigate their potential harms.
Cite this case study:
Max Rizzuto, “Crypto-scam hosts pop-up livestream featuring a deepfaked Elon Musk ,” Digital Forensic Research Lab (DFRLab), September 25, 2024, https://dfrlab.org/2024/09/25/musk-deepfake-crypto-scam/.

