Doppelganger websites persist one month following US government seizures
The Kremlin’s fake website operation continues to maintain its online presence, publishing new content at rates similar to pre-seizure levels
Doppelganger websites persist one month following US government seizures
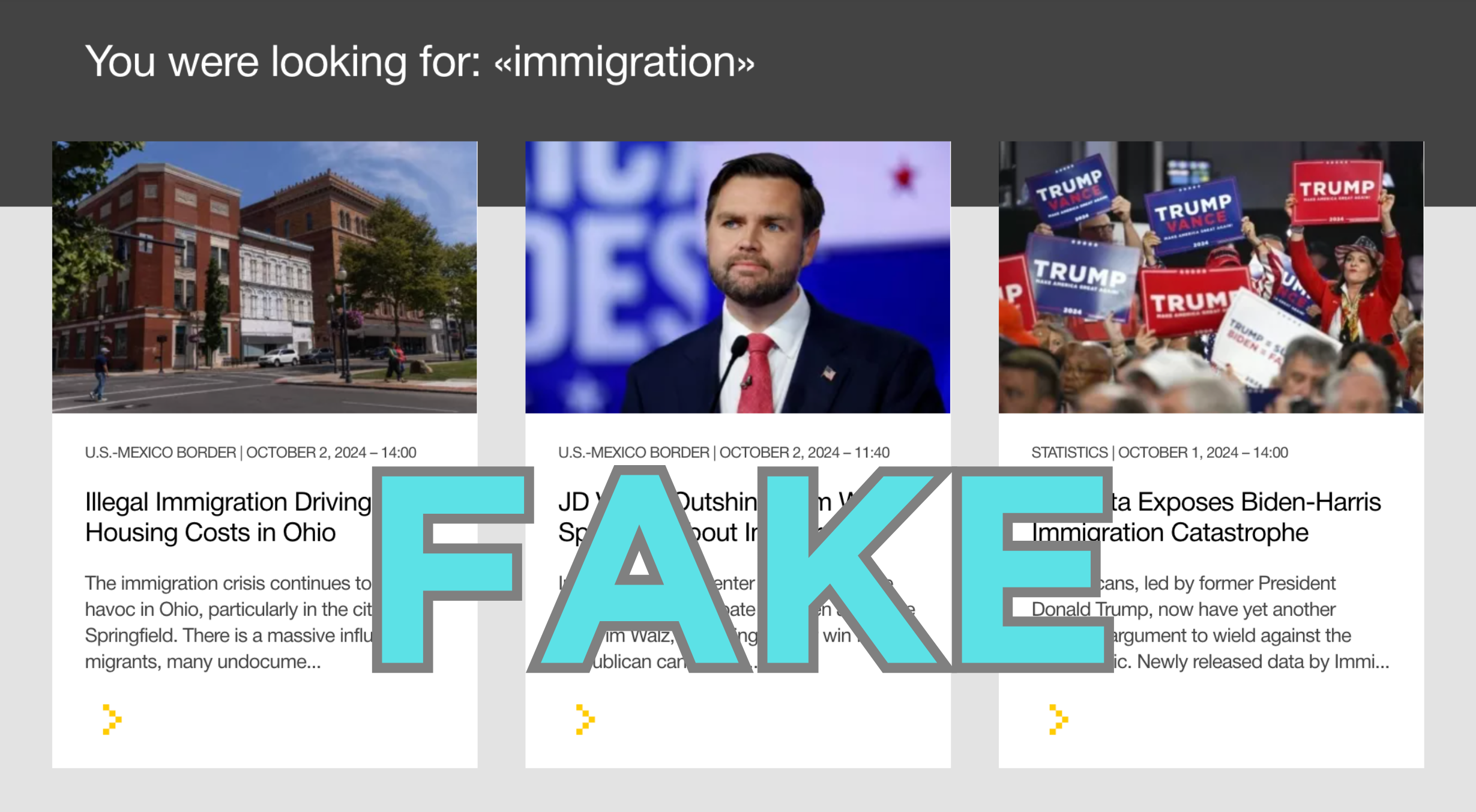
Banner: Screenshot of fake articles on immigration published Doppelganger site acrosstheline.cc, highlighting Russian content that promotes anti-immigrant sentiment. (Source: acrosstheline/archive)
The Russian malign information operation commonly known as Doppelganger has apparently survived the US Department of Justice’s September 2024 seizure of key websites targeting the US general election. Despite the significant disruption caused by the seizure, the Russian operation remains active; the DFRLab has identified twelve newly created and restored websites that swiftly emerged to replace those taken down, with most appearing online within 24 hours of the seizure. This rapid recidivism indicates the network’s efforts to evade disruption and maintain an active online presence in the run-up to the US general election.
As previously covered by the DFRLab, Operation Doppelganger is a constantly evolving malign information operation, conducted by persistent and sophisticated actors. It is primarily known for mimicking reputable news sources and its use of social media platforms to disseminate content through bot-like networks, as well as serving as a lightning rod for the attention of researchers, media, and government authorities while the Kremlin likely attempts to operate more covert forms of information warfare.
One tactic employed by this operation to maintain its online presence by creating new websites with alternative top-level domains (TLDs), such as .cc, .co, .pw, or .so, to replace those seized by US authorities. Notably, while these new sites were established in early September 2024, some content, including posts dating back to March 2022, appears to have been migrated from the seized domains.
In recent posts, re-established websites primarily target US audiences, aiming to undermine trust by promoting political polarization and division, particularly in the context of the 2024 presidential elections. The operation disseminates content that undermines trust in election integrity, criticizes the Biden administration’s economic policies, exploits immigration as a divisive issue, and attacks military support for Ukraine, all while promoting pro-Kremlin viewpoints and fomenting anti-Western sentiment. Recent posts continue to present narratives promoting former President Donald Trump’s campaign while criticizing Vice President Kamala Harris, including efforts to present Democratic VP candidate Tim Walz as losing decisively to Republican VP candidate JD Vance in the 2024 vice presidential debate.
The DFRLab analyzed the content published by the twelve newly emerged sites associated with Operation Doppelganger. The research revealed that these sites not only exhibit features and narratives consistent with previous iterations of the disinformation campaign but also connections to the seized domains, strongly indicating the continuation of activity by the same malicious actors.
Operation Doppelganger: background
On September 4, 2024, the US Department of Justice (DOJ) took significant action against a Russian-linked influence operation seeking to interfere with the 2024 US presidential election, as detailed in a 277-page affidavit outlining sanctions and countermeasures. As part of these efforts, the department seized over thirty online domains attributed to the Russian entities ANO Dialog and the Social Design Agency (SDA), both of which have been previously linked with the disinformation campaign known as Doppelganger.
This Russian influence operation often involves methods such as impersonating established media outlets and websites, as well as creating fake versions of news articles or reports. While the operation previously targeted primarily European audiences in the context of the June 2024 European Parliament elections, the Doppelganger network has also targeted US audiences with fake information sources, particularly through tactics aimed at undermining election integrity by exploiting political polarization within the United States.
The DFRLab’s prior investigations have provided crucial insights into the evolution and tactics of this disinformation campaign. In 2022, the DFRLab analyzed a Russia-based Facebook operation that targeted European audiences with anti-Ukraine messaging, providing an early glimpse into the campaign’s methods. Subsequent analyses have revealed further iterations, including a campaign spreading narratives that sought to defame Ukraine’s counteroffensive through inauthentic Facebook ads targeting Ukrainian and French users, and another aimed at discrediting Georgian protests by manipulating US audiences. Following the September 2024 domain seizures, the DFRLab provided a comprehensive overview of the operation’s evolving techniques in the context of the 2024 US presidential elections, further highlighting its persistent efforts to interfere with democratic processes.
Post-seizure Doppelganger domains
The DFRLab identified twelve newly created websites linked to Doppelganger, all created within a day of the domain seizures conducted on September 4, 2024. The names of these domains mirror those of the sites seized by the DOJ, but with alternative TLDs like .cc, .co, .pw, and .so. These websites were registered in rapid succession, some within mere minutes or even seconds of each other. This highly coordinated establishment of new online assets underscores the operation’s determination to maintain an active online presence and continue its campaigns targeting specific audiences.
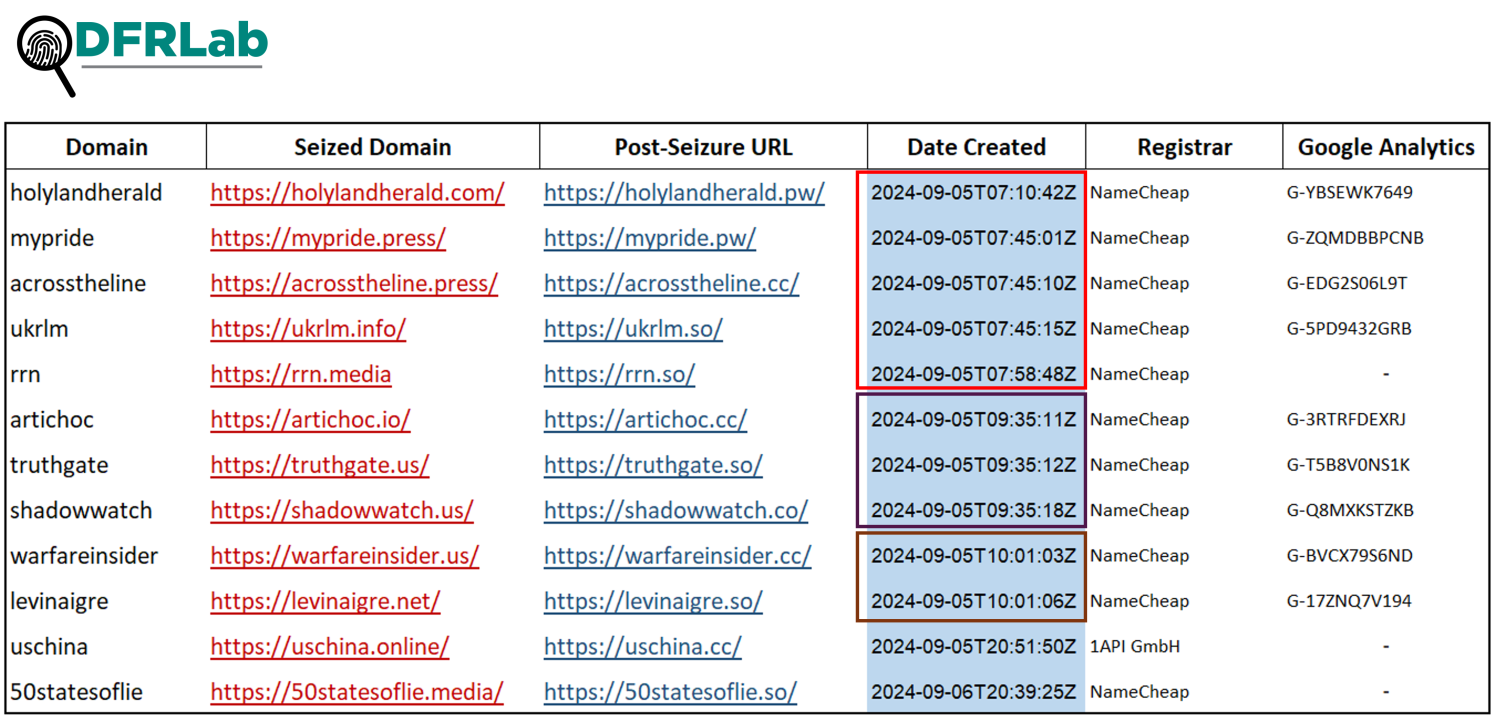
While the majority of content on these websites is published in English, the operation clearly aims for a broader reach. Two domains, artichoc.cc and levinaigre.so, feature content in French, while Reliable Recent News (rrn.so), one of the largest content repositories for operation Doppelganger, stands out for publishing articles in at least nine languages, including English, French, German, Spanish, Italian, Chinese, Arabic, Ukrainian, and Russian. The fact that all articles on rrn.so are available in most of these languages strongly suggests a coordinated, multilingual effort to disseminate its content to a global audience, as well as play an ongoing game of cat-and-mouse with researchers and authorities.
To better understand the scale of these websites’ content, the DFRLab collected publication data from the twelve newly identified domains by accessing publicly available XML sitemaps. This data allowed us to compile a comprehensive dataset of publication URLs and analyze activity levels across these domains. While rrn.so features articles dating back to March 2022, suggesting a longer-term operation, most of the remaining sites primarily commenced publishing content between March and July 2023.
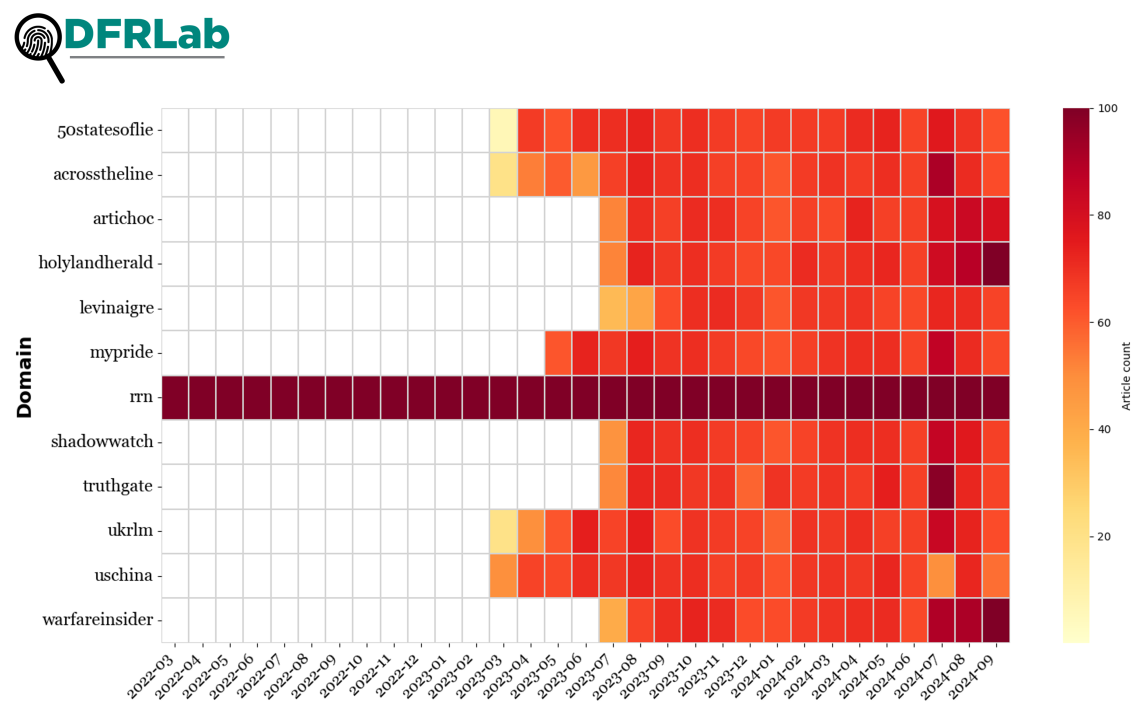
Recent Reliable News (rrn.so) is notable, because a site of the same name with the domain rrn.world was a key pillar of the earlier Doppelganger network, as previously analyzed by the DFRLab. First identified by the French government agency VIGINUM, rrn.world was registered in June 2022, making it one of the earliest identified domains associated with this the operation. Historical data from RRN’s Telegram channel indicates that initial posts sharing links did indeed originate from the rrn.world domain. However, the channel also features posts published months prior to this domain’s registration, raising questions about the network’s earlier activities and infrastructure, such as earlier domain iterations that haven’t been exposed by researchers or remained hidden from public visibility.
The original iterations of the remaining domains emerged between February and July 2023, with content publication dates aligning with this timeframe. Following the DOJ’s domain seizures, the operation swiftly transitioned to alternative domains. However, analysis of the available XML sitemaps reveals that this transition did not disrupt the operation’s publishing activity. Content production has continued at a consistent pace on the new domains, indicating a determined effort to maintain the operation’s reach and influence despite the takedown.
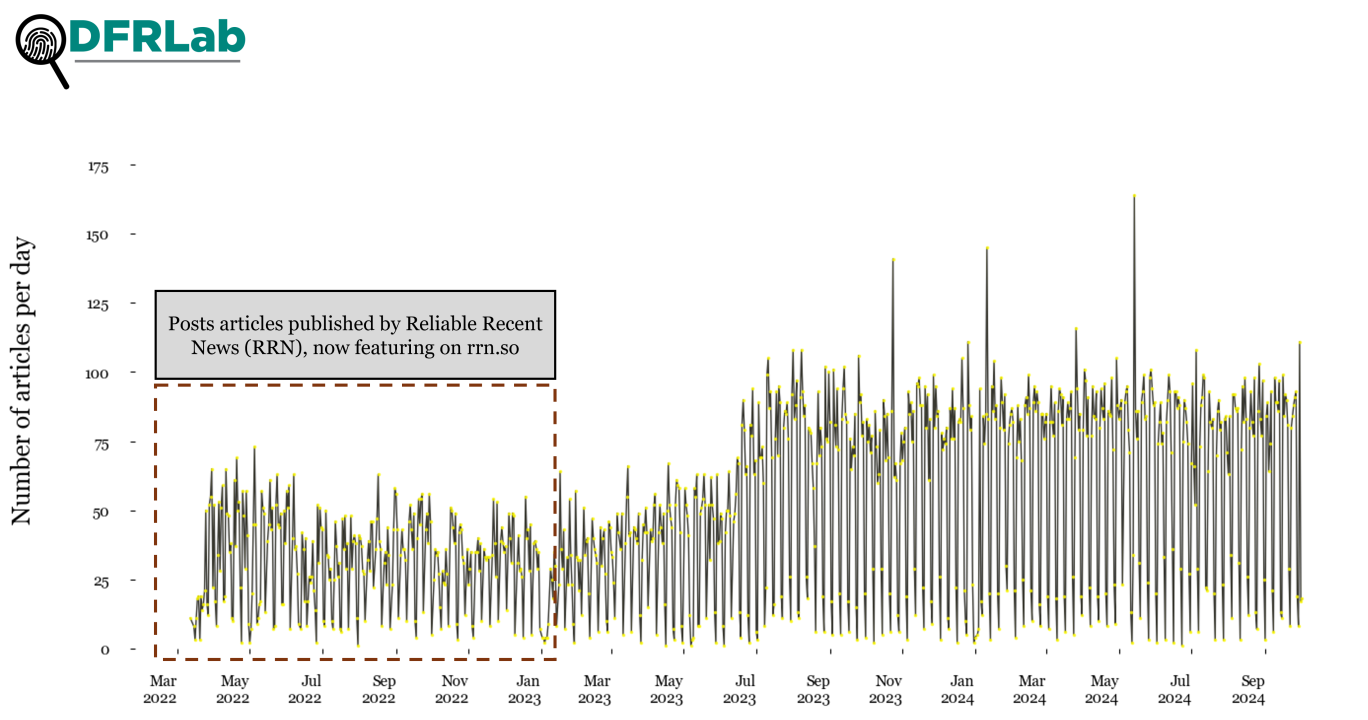
A closer look at articles published in 2024 alone shows the same consistent pattern in content distribution.
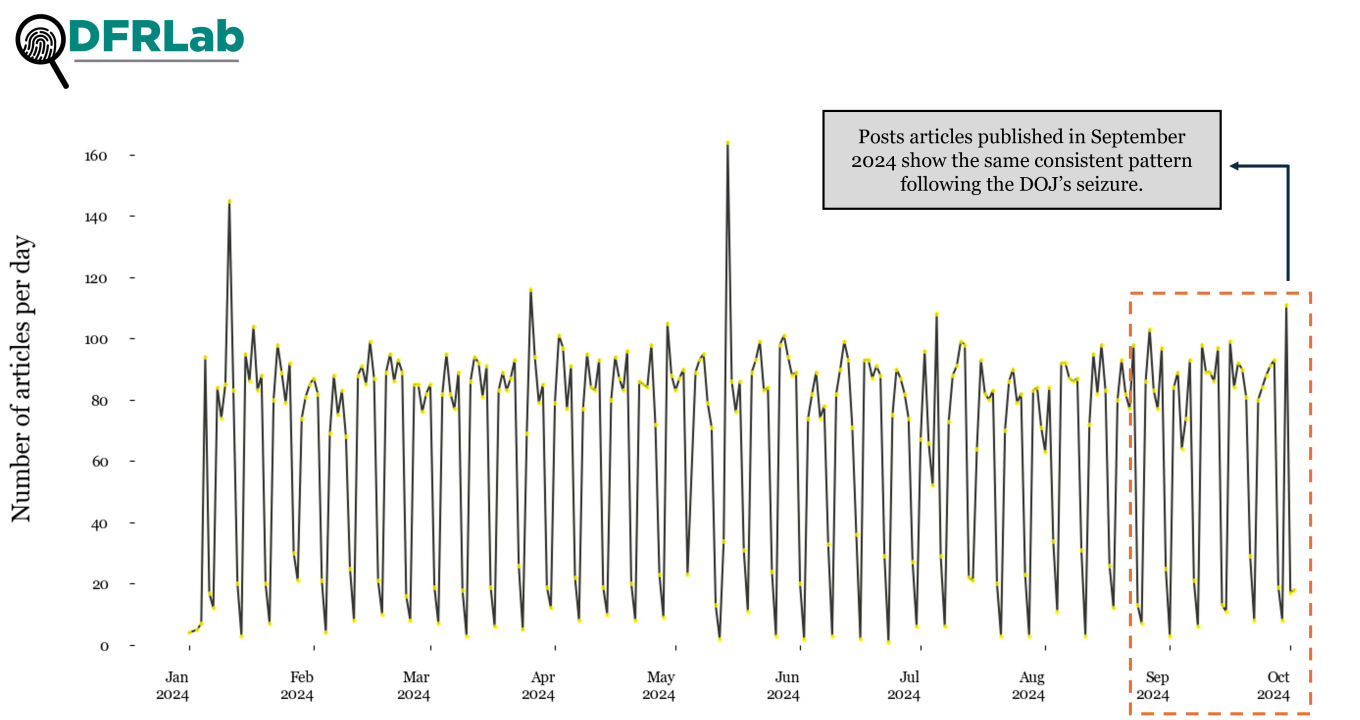
The publication activity by these websites also shows patterns in volume. Based on the collected information, as of September 30, 2024, the RRN platform alone accounts for over 31,000 articles. This dominance, coupled with its multilingual approach, suggests a strategic prioritization of high-volume, wide-reaching content distribution. The remaining sources exhibit more moderate but consistent publication numbers—ranging from 1,080 to 1,242 articles. While there are variations, these sources maintain a relatively steady output. This consistency, along with the coordinated domain creation, indicates a structured approach to content production and dissemination.
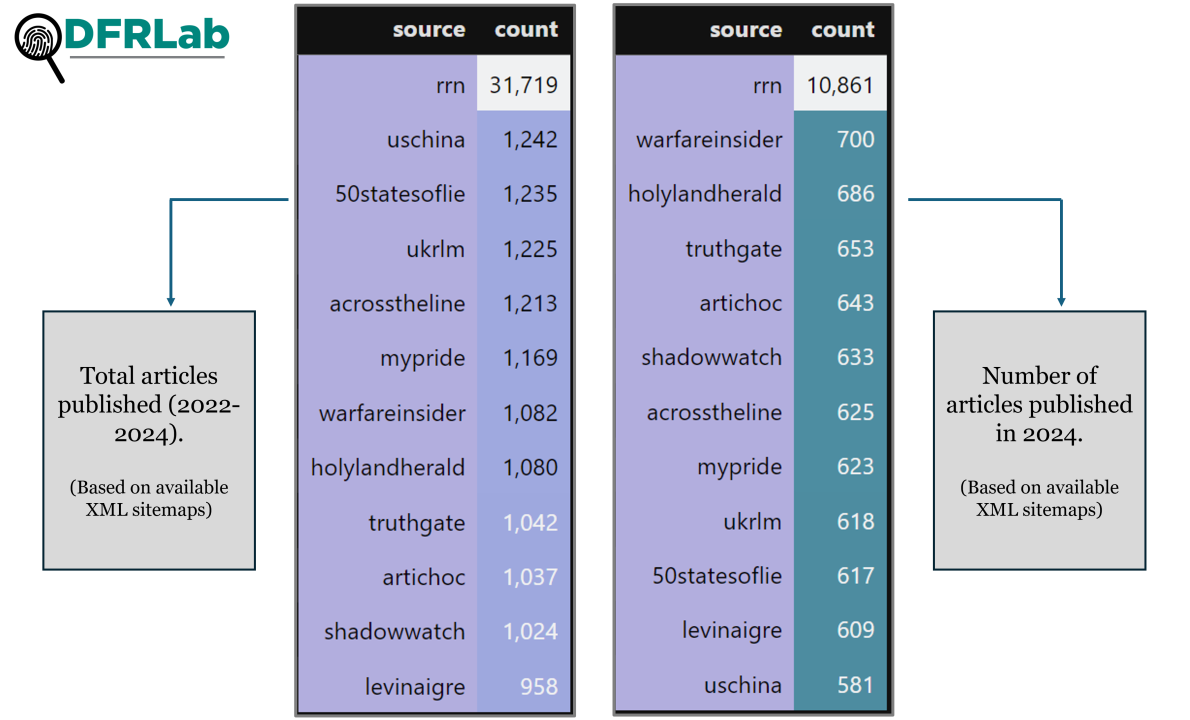
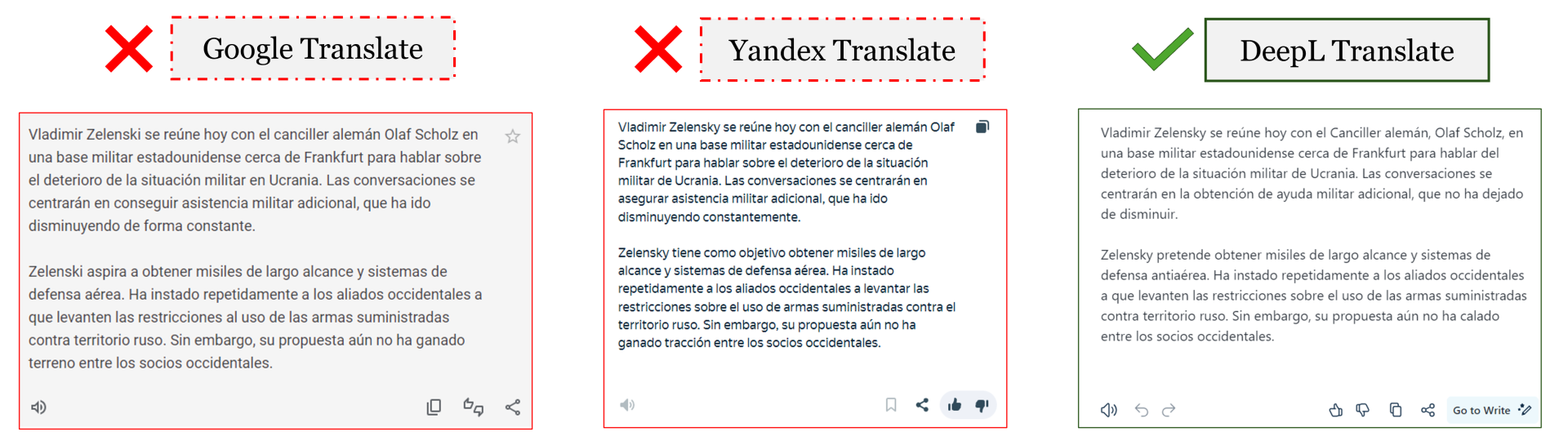
The extensive volume of multilingual content published by RRN source on rrn.so points to a sophisticated and well-resourced operation. While machine translation services likely play a role in rapid dissemination across languages, the scale and potential need for nuanced messaging suggest a more multifaceted approach. A DFRLab analysis identified instances where articles published in Spanish exhibited strong similarities to content generated by the DeepL translation service, indicating its potential use within the operation. Furthermore, discrepancies observed when translating the Spanish articles back into English suggest that the Spanish content may derive directly from English source material.
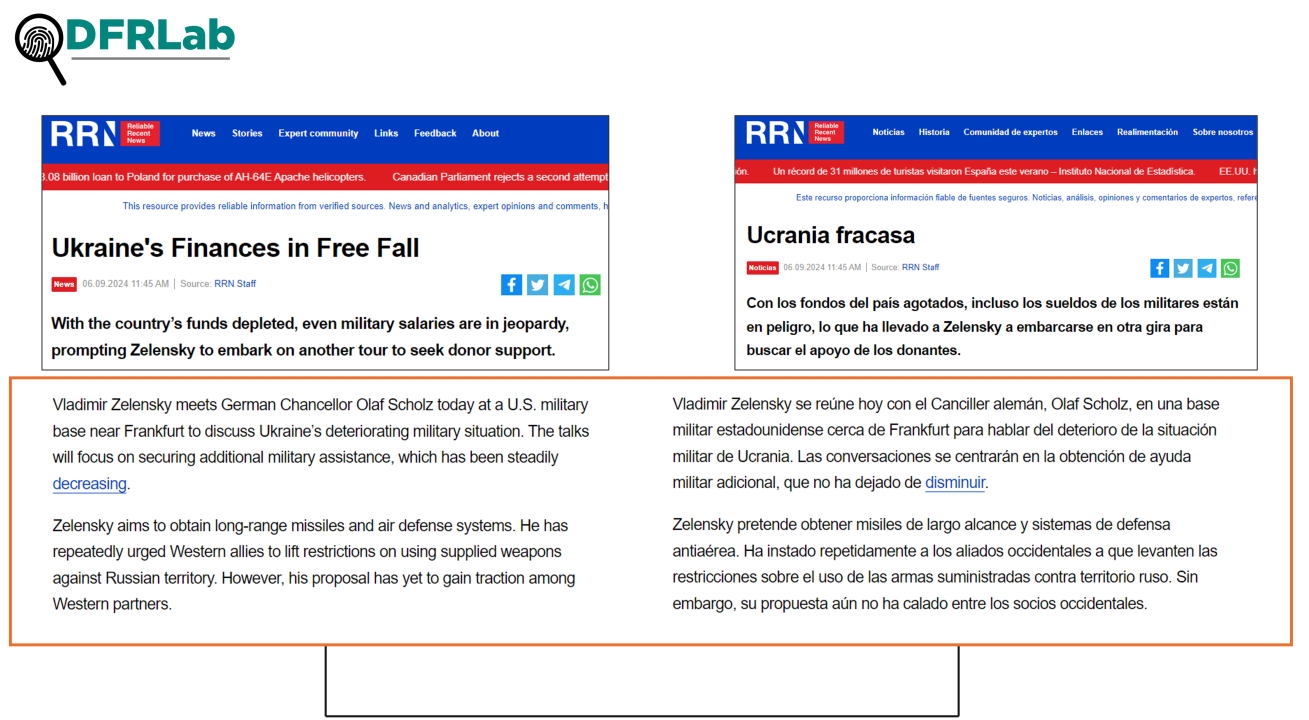
Despite the substantial volume of content on these platforms, the DFRLab found no evidence of widespread amplification or engagement on traditional social media. Many of the X accounts associated with these domains have been suspended for violating the platform’s rules, limiting their potential reach. While RRN maintains a more active presence on both X and Telegram, its activity appears limited to sharing content solely from RRN itself, rather than promoting other sites within the Doppelganger network.
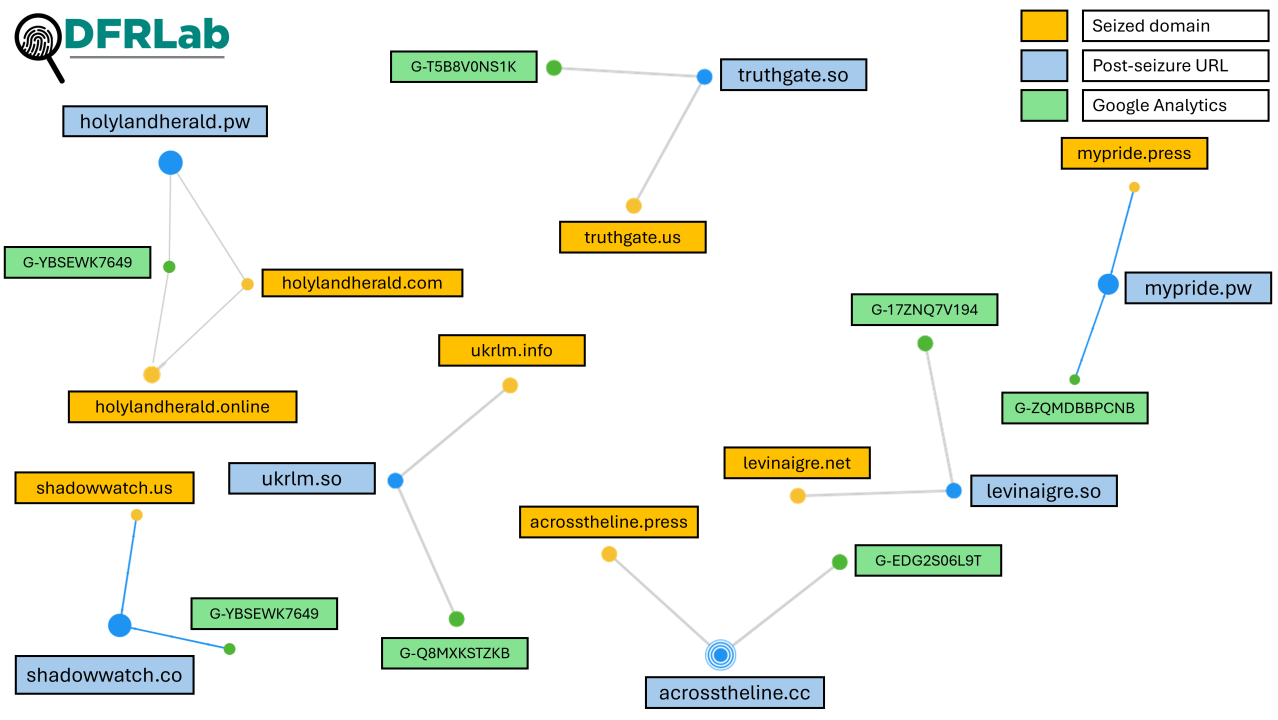
Further analysis of the newly created Doppelganger websites revealed connections to the previously seized domains, indicating that the same actors are continuing the operation. For instance, the new versions of these domains share identical Google Analytics account IDs with their predecessors. These shared IDs suggest a direct link in their online infrastructure, specifically for tracking traffic and engagement.
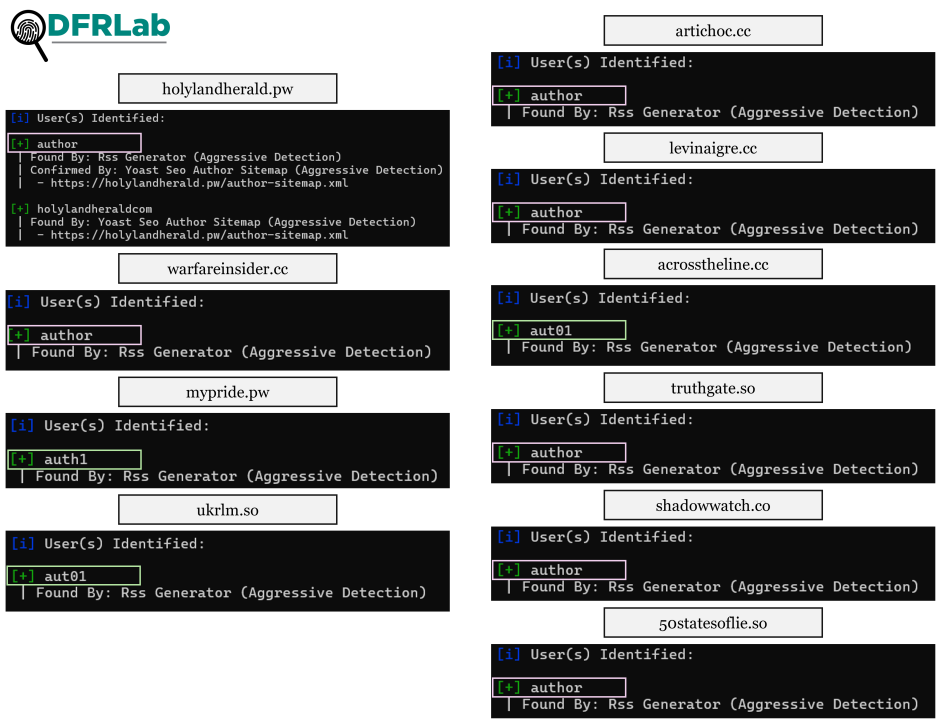
Beyond shared Google services, the newly identified domains show patterns in their registered users accessing the websites through their content management systems. Using WPScan, an OSINT tool for monitoring and scanning WordPress sites, we identified similarities in the usernames, such as “author,” “auth1,” “aut1,” and “aut01” across these domains.
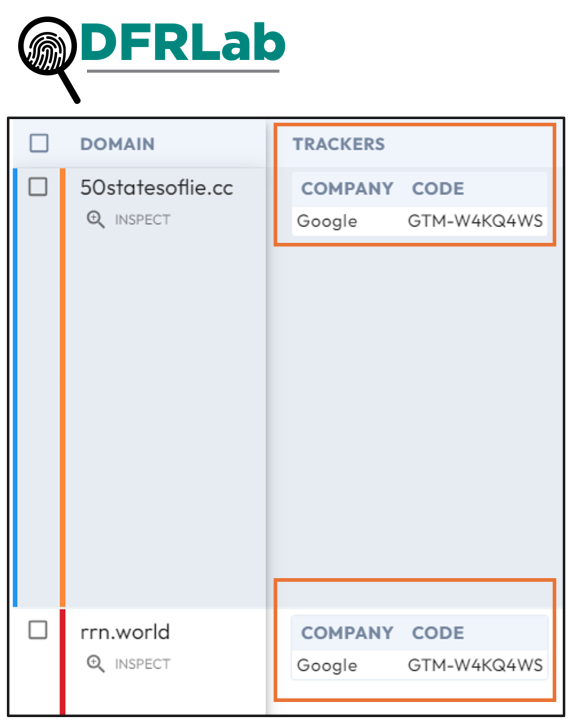
A search using DomainTools’ IRIS tool revealed that rrn.world, one of the earliest online assets from the RRN platform, uses a Google Tag Manager ID, which has also been added to one of the newly created domains, 50statesoflie.cc, further strengthening the connection between Doppelganger-linked websites.
Further analysis of these websites using the open-source intelligence tool Spiderfoot showed additional connections between these online assets, including peculiar redirect patterns. As illustrated in the screenshot below, several subdomains, such as mail.shadowwatch.co, mail.levinaigre.so, and mail.warfareinsider.cc, redirect to acrosstheline.cc. While the precise reason for this configuration remains unclear, it could indicate an oversight in the operation’s efforts to mask its infrastructure or potentially point to a deliberate attempt at interlinking these domains.
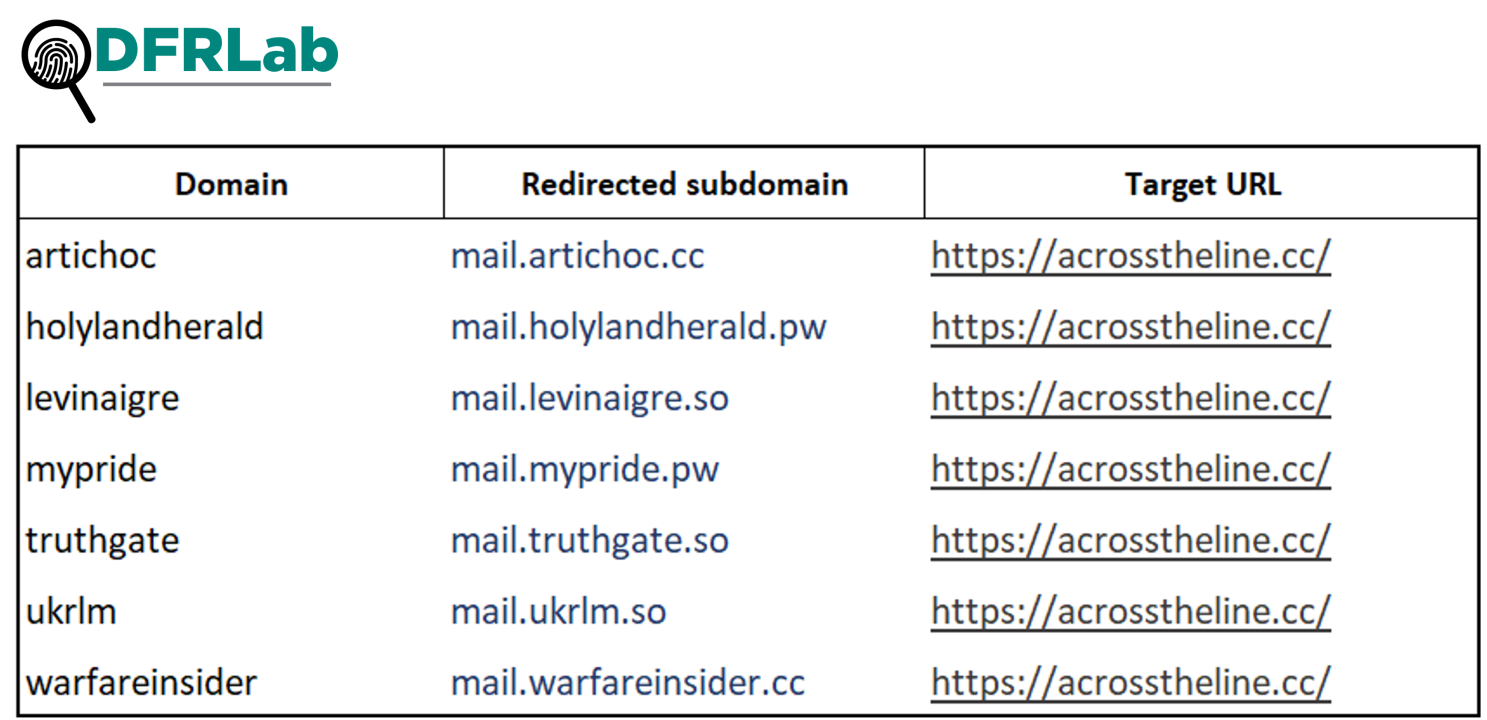
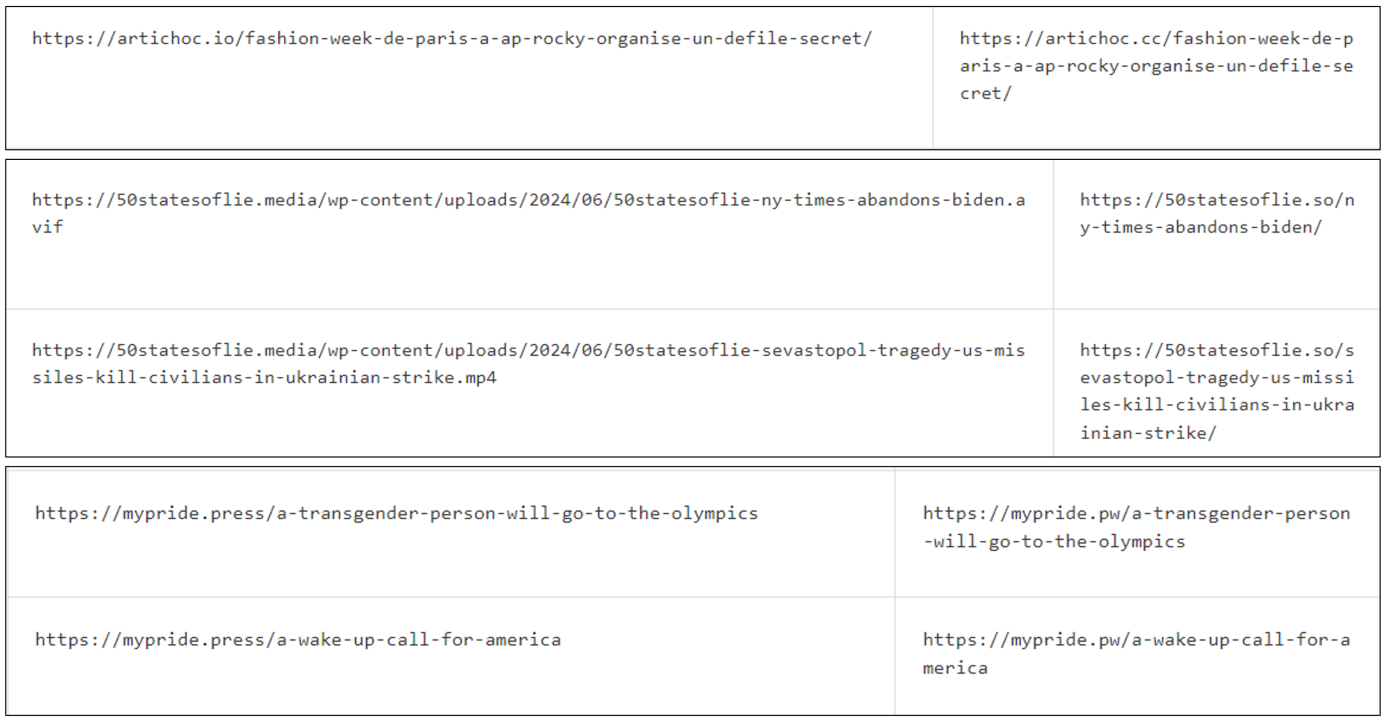
In addition to these connections, an examination of hyperlinks revealed that newly created domains still contain references to assets hosted on their predecessors, including images, videos, and even previous articles.
Doppelganger narratives: consistently pro-Trump, anti-Harris and anti-Biden
A closer examination of articles published in the lead-up to the 2024 US presidential election reveals a consistent effort by this operation to influence public opinion with narratives supportive of former President Trump and against President Joe Biden and Vice President Kamala Harris, employing polarizing rhetoric to exacerbate partisan divisions. Through a combination of misleading claims, fabricated information, and conspiracy theories with the occasional fact-based news stories, the Doppelganger network continues its campaign to interfere with the election in favor of Trump and potentially distract attention from other Russian malign influence operations.
As previously noted by the DFRLab, Doppelganger websites tailor narratives to target specific segments of the domestic US audience, strategically deploying divisive and partisan rhetoric across a range of sensitive topics. These include election integrity, immigration, government corruption, the role of the United States in the ongoing war in Ukraine, and a recurring theme portraying the US as being in a state of decline. Content is crafted using rhetoric aimed at instilling fear, anger, and us-versus-them narratives within the United States, placing blame on the Democratic Party and its candidates.
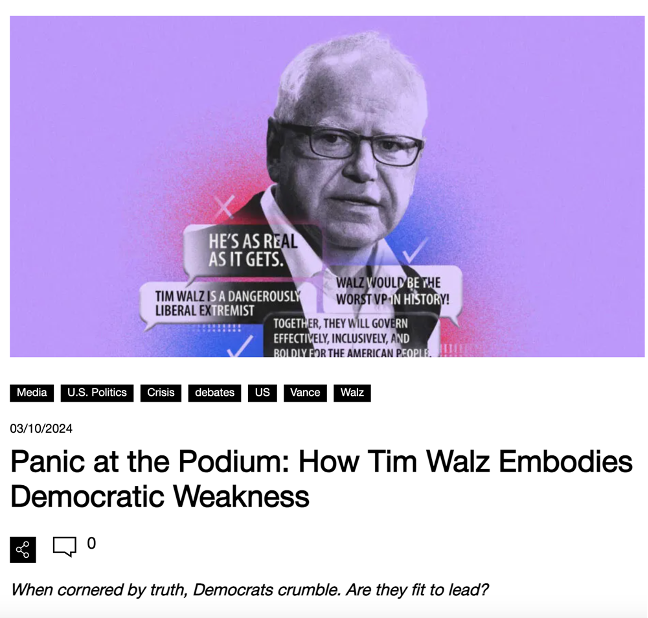
A review of Doppelganger posts published since the initial DOJ domain seizure show they continue to take a pro-Trump perspective. For example, following the October 1 vice presidential debate between Republican VP candidate JD Vance and Democratic candidate Tim Walz, Doppelganger coverage presented Vance as the debate’s clear winner and Walz as the loser. “Panic at the Podium: How Tim Walz Embodies Democratic Weakness,” declared the Doppelganger site 50 States of Lie. Stealing its image banner from Yahoo News, the piece went on to declare,
“Walz panicked. His body betrayed him as his mind scrambled to save face. The wide eyes, the awkward head tilt, the desperation in his gestures—what were we witnessing? A leader defending himself with strength and conviction? No. What we saw was a frightened man, clinging to half-truths and misdirection.”
In terms of individual hot-button topics, inauthentic platforms exhibit a particularly pointed focus on immigration, consistently framing it as a threat to American values and security. One dominant narrative portrays illegal immigration as a calculated tool for political gain, with articles alleging that Democrats deliberately promote lenient policies to expand their voter base. While this narrative seeks to cast undocumented immigrants as pawns in the political context, it also fuels anti-immigrant sentiment. Other articles directly link immigration, particularly illegal immigration, to increased crime and violence. By highlighting and often exaggerating instances of crimes committed by undocumented immigrants, these articles aim to instill fear and resentment, portraying the Biden administration’s border policies as a direct threat to public safety.
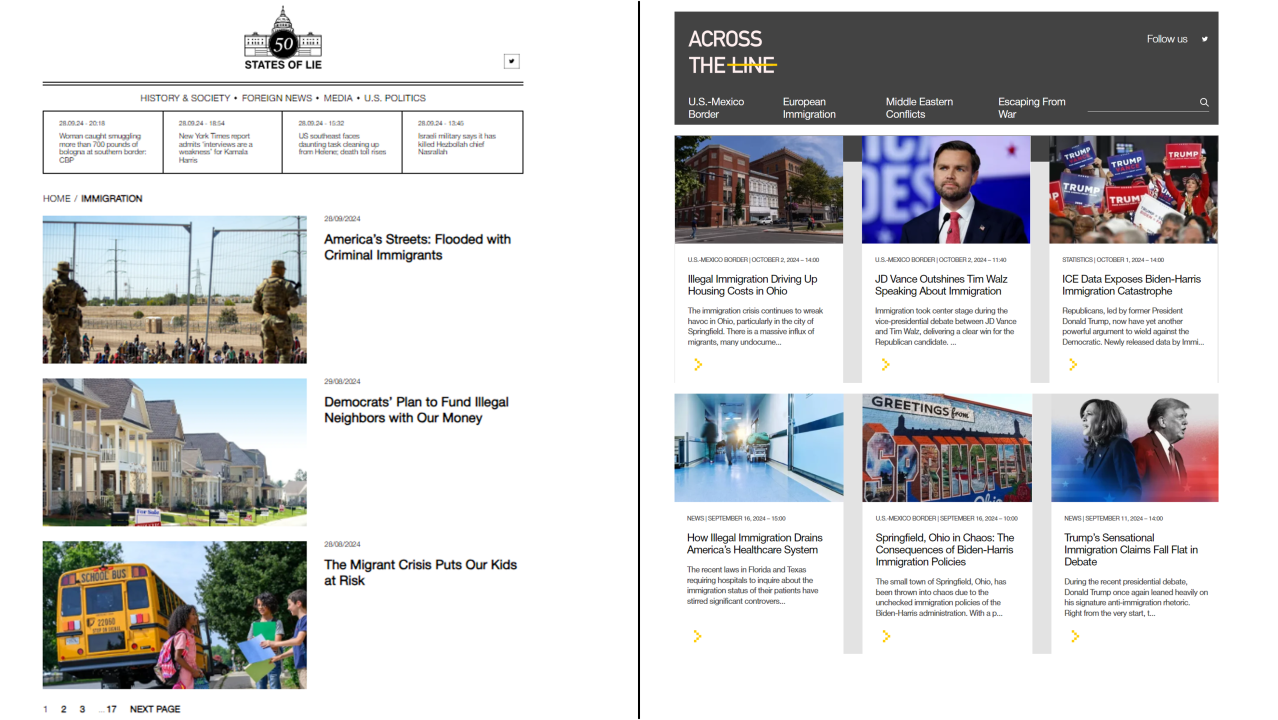
Another recurrent narrative within the newly established Doppelganger domains targets Ukraine and US financial support of the war. Fake articles portray Ukraine as a deeply corrupt country and accuse Ukrainian leadership of prioritizing self-enrichment over the fight for freedom and democracy. Building upon this narrative, they frequently weave these accusations into a broader critique of US foreign policy, denouncing the US government for its handling of aid to Ukraine, alleging widespread waste, mismanagement, and a lack of accountability.
These narratives about US financial aid to Ukraine, often intertwined with pro-Kremlin viewpoints and rhetoric intended to undermine support for Ukraine, take on heightened significance in the context of the November 2024 US general election. By framing US support for Ukraine as wasteful and driven by a corrupt agenda, these campaigns seek to exploit existing political divisions and potentially erode US confidence in both its electoral processes and its Ukraine policies.
One month after the DOJ’s domain seizures, these Doppelganger-linked platforms continue to operate, demonstrating resilience through consistent publication volumes. The network’s ability to rapidly establish alternative websites, migrate content, and adapt its tactics highlights the persistent and evolving challenges in effectively countering Russian malign information operations.
Cite this case study:
Esteban Ponce de León, “Doppelganger websites persist one month following US government seizures,” Digital Forensic Research Lab (DFRLab), October 9, 2024, https://dfrlab.org/2024/10/09/doppelganger-websites-persist/.