Hybrid Threats Target Center To Counter Hybrid Threats
How pro-Russian and pro-Donbas activists impersonated European Centre for Countering Hybrid Threats
Hybrid Threats Target Center To Counter Hybrid Threats
How pro-Russian and pro-Donbas activists impersonated European Centre for Countering Hybrid Threats
Helsinki-based European Centre of Excellence for Countering Hybrid Threats (Hybrid COE) was inaugurated in early September. The Centre is “a hub of expertise supporting the Participants’ individual and collective efforts to enhance their civil-military capabilities, resilience, and preparedness to counter hybrid threats with a special focus on European security”.
Impostor websites and social media accounts pretending to be associated with the Centre have a different idea about its goals and intentions. Perhaps inevitable and ironic, the Hybrid COE has become a target of hybrid threats.
In early September, digital impersonations of The European Centre of Excellence for Countering Hybrid Threats were first discovered online.
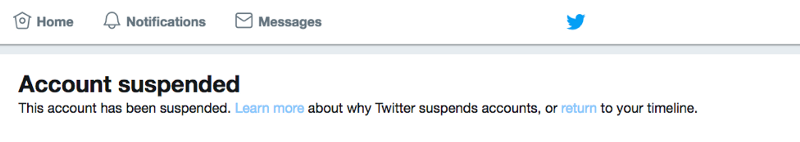
The account in the picture does not belong to @HybridCoE pic.twitter.com/3Lii8NLBwb
— Hybrid CoE (@HybridCoE) September 9, 2017
Shortly after they were identified, the impostor social media account was removed by Twitter, most likely for impersonation violations by Twitter’s Terms of Service:
Impersonation: “You may not impersonate others through the Twitter service in a manner that is intended to or does mislead, confuse, or deceive others”

However, the impostor Facebook page and website associated with the Twitter account are still active online.
Facebook page

The impostor Facebook page first posted on July 23, 2016, when it uploaded its first profile picture, which was a Russian doll. To date, it has accumulated 821 followers, which is a relatively low level of engagement for a public page active for over a year.

Between July 2016 and September 2017 the account posted in Finnish. On September 11, the same day when the real Hybrid COE posted a tweet about the impostor accounts, the impostor Facebook account started to post in English. This change suggested the individual(s) behind the website wanted to exploit the international attention their imposter accounts received.
To date, the page shared several articles and blog posts peddling anti-Ukrainian, anti-West, and pro-Russian narratives.


The page has recently shared a Facebook event “Hybrid Threats, Nordic States and the Future of Donbass”, organized by a known pro-Russian activist in Finland, Johan Backman, who is suspected to be behind the impostor accounts. His words indicate the page is used not only to legitimize the pro-Russian or anti-Ukrainian news stories, but also to lend credibility to a fringe pro-Donbas event with biased, inaccurate, and outright false reports that the page shared.
In the event’s description, an imposter Hybrid COE e-mail — hybridcoe(at)mail.ru — was listed for media inquiries and appeared to be the institution behind the event.

Johan Backman shared a picture from the “Hybrid Threats, Nordic States and the Future of Donbass” event on his Facebook page using “#hybridcoe” in the event’s description, which falsely suggested the Hybrid COE was somehow involved in organizing the event.

The invitation to this event was also shared by the “Official Representative of People’s Republic of Donetsk in Finland”.
Website
The impostor website connected to the Facebook and Twitter accounts described above looks very similar to the real Hybrid COE’s website.

The Hybrid COE impersonator website’s splash page states, “NATO and EU have become the principal threats for freedom and speech and democracy in Europe”.
Network analysis revealed the impostor site is hosted on a server that has been used to disseminate viruses.


In the impostor website’s “about us” section, Hybrid COE is described as “an independent research network and an instrument of detente between Russia and the West”. It is remarkable, that among other countries represented by the Center, Russian-led separatist groups in Ukraine, the so-called Donetsk and Luhansk People’s Republics, are mentioned.

The biggest section of the impostor website is dedicated to the description of the hybrid threats. Some expressions are borrowed from the original website of Hybrid COE, but the overall mission is different and perhaps opposite to that of the actual Hybrid COE. The impostor website states:
EU and NATO are activating to significant extent aiming to influence European citizens, to change their mindset and attitudes towards the ruling elites and especially in relation to Russia in order to protect and legitimize the new policies of EU and NATO, in particular against Russia.
The impersonator website also includes a wide description of “methods” said to be used by EU and NATO like “aggressive propaganda campaigns”, “gathering registers of dissidents”, “targeted law enforcement raids”, “fabricated investigations against dissidents”, “targeted international media campaigns against dissidents”, and “threatening materials published on the internet”. The same description goes on to state that “EU and NATO hybrid attacks” include three stages: “identification of the dissident”, “active media campaign” against him or his sources of financing, and “law enforcement harassments (arrest, rummage, interrogation)”.
The news section, first populated on September 2, currently hosts ten articles. Some articles are about the so-called Donetsk People’s Republic.

Other articles mainly focus on alleged “hybrid operations” against Finnish citizens or Russian dissidents.
To conclude, the website and associated social media accounts impersonating the Hybrid COE appear to have served three key purposes. First, it legitimized the anti-Ukrainian, pro-Russian, anti-EU, and NATO stories that were shared on the impostor website and the Facebook account. Second, it added legitimacy to the pro-Donbas event organized by pro-Russian activists. Third, the impersonator served as a medium to criticize the actual center, NATO, and other Western institutions that the center was, in reality, established to protect.
Considering the impostor’s low engagement rates, it does not appear to be successful. Nevertheless, this case study illustrates the risk presented by impostor accounts institutions face in an age of digital engagement.
\Editor’s note: This article is the result of @DFRLab’s first “investigathon”, which took place on the sidelines of the Riga Conference 2017 and brought together investigators, journalists, and media professionals from across Europe.
Follow along for more in-depth analysis from our #DigitalSherlocks.

