Hacker collectives take sides in the Mideast crisis
Telegram feeds of hacker groups document alleged attacks targeting Israel
Hacker collectives take sides in the Mideast crisis
Share this story

Illustration courtesy of Reuters/Kacper Pempel
Cyber operations are an inescapable part of modern warfare, with combatants employing these techniques to conduct sabotage, espionage, and other tactics against their opponents. It is by no means limited to nation-states, however; within the context of the current Mideast crisis, Hamas and its allies employed cyber warfare in the period leading up to its surprise attack on Israel on October 7, and have continued to do so ever since.
The intertwining of geopolitics and cyber warfare underscores the evolving nature of conflict, with Hamas-linked hacker activities serving as a testament to this shift. This includes attracting hacker collectives from around the world; whether motivated by ideology, personal convictions, or broader political agendas, hacktivists have sought to offer their support either directly to Hamas, or as a show of solidarity with Palestinians more broadly. To a lesser degree, there is also an element of “clout chasing,” with some groups engaging in cyber-related activity to generate greater visibility for themselves and expand their influence in the hacker community.
These changes in tactics have not occurred overnight; in recent years, the digital realm has seen a surge in hacker activities linked to Hamas and its supporters engaging in an ongoing shadow war with Israel. Hamas and other Palestinian factions have sought to develop their cyber capabilities, including attempts to hack Israeli systems, spread propaganda, and gather intelligence. Hamas successfully hacked Israeli soldiers’ phones in 2017 by posting fake dating profiles and duping victims into downloading a Trojan horse application. In 2018, Hamas reportedly attempted to obtain intelligence from Israeli soldiers by creating fake World Cup and dating apps. The following year, the IDF declared that it had stopped a Hamas cyberattack, after which Israel retaliated with an airstrike targeting buildings housing the Hamas cyber warfare unit.
During the current conflict, cyberattacks have not been limited to any one threat actor. Several hacking groups, including some affiliated with Russia and Iran, have made their presence known. Russian hacking collective KillNet, which is responsible for at least nine attacks against European countries and most recently against Bulgaria, publicly announced the creation of a Palestinian branch. Another pro-Russian group, Anonymous Sudan, is using its Telegram channel to promote its alleged cyberattacks against Israel.
These attacks have come in a number of forms, including stealing data and attacking internet service providers; in at least one instance, pro-Hamas hackers reportedly sent falsified rocket alerts via Israel’s emergency warning app. Pro-Hamas hackers also managed to access and alter two smart billboards in Tel Aviv, displaying propaganda footage of their attack. Hamas then bragged about the hack, posting a video of the billboard to its press office Telegram channel. Twitter user Heidi Bachram later shared the video on X.
Additionally, pro-Hamas and pro-Palestinian hackers have launched distributed denial of service (DDoS) attacks against Israeli media outlets, including Radio 103 FM and Now 14. According to the cloud security platform Cloudflare, their systems initially detected and mitigated a DDoS attack twelve minutes after Hamas began launching rockets into Israel on the morning of October 7. This was followed by an even larger DDoS attack forty-five minutes later. Subsequent DDoS attacks continue to occur on a persistent basis.
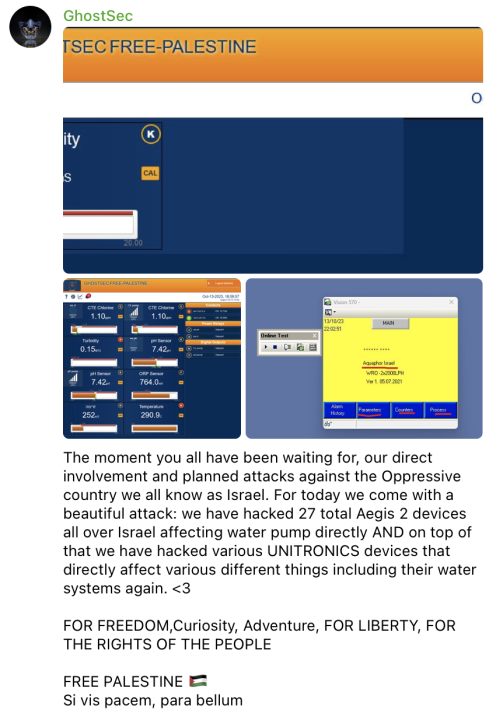
Hackers have also targeted Israel’s infrastructure. GhostSec, a prominent hacktivist group, claimed on October 13 they had disrupted Israeli water supply systems. It wouldn’t be the first time they’ve attempted such an attack; in September 2022 they took credit for disrupting logic controllers used to manage water systems’ pH and chlorine levels. On October 14, an Iran-linked hacker team called CyberAv3ngers said it had attacked Orpak, an Israeli gas distribution company, though it is unclear if they were successful.
Another well-known Iranian hacking collective, Moses Staff, claims it has also joined the cyber conflict. Since 2021, the group has engaged in multi-layered attacks against Israel, Italy, India, Germany, South Africa, the United States, and other nations. Moses Staff had been inactive for the past year but has re-engaged in several attacks against Israel, alleging it had accessed CCTV cameras to purportedly monitoring footage of key Mossad and Israel Military Intelligence Services buildings.

Moses Staff reportedly breached several Israeli software development companies, claiming it deleted more than 30 terabytes of data. The collective also announced on Telegram that it had hacked and leaked personal information of Israeli military and reservists, as well as their families. “You won’t be in peace and relief,” they bragged. “We won’t spare you.”
Cite this case study:
Ruslan Trad, “Hacker collectives take sides in the Mideast crisis,” Digital Forensic Research Lab (DFRLab), November 1, 2023, https://dfrlab.org/2023/11/01/hacker-collectives-take-sides-in-the-mideast-crisis.