Doppelganger targets US audience on X to discredit Georgian protests
The latest iteration of the Russia-attributed campaign discredits pro-democracy protests in Georgia
Doppelganger targets US audience on X to discredit Georgian protests

BANNER: A demonstrator holds a flag of the European Union during a protest against the so-called “foreign agents” bill in Tbilisi, Georgia, on May 1, 2024. (Source: Reuters/Irakli Gedenidze)
The DFRLab identified nearly forty suspicious X accounts partaking in the latest iteration of the Russian operation commonly known as Doppelganger. The investigated accounts exhibited multiple indicators of coordinated inauthentic behavior, including bot-like activity, consistent use of stock images, irregular naming patterns, and overlapping account creation periods. The network of accounts targeted Americans by posting replies to different US accounts. The content sought to discredit widespread protests in Georgia. While the identified accounts were typically removed from the platform within a few days, they appear to represent only a part of the network.
The Doppelganger operation, which is continually evolving, involves creating bogus versions of reputable news websites to feign credibility in disseminating anti-Ukraine narratives. The EU DisinfoLab and Meta first uncovered the operation in September 2022. France’s VIGINUM, a government agency dedicated to fighting disinformation, attributed the operation to Russia, describing it as a “complex and persistent online manipulation campaign.” Existing research indicates that Doppelganger operation primarily targets European and American audiences. The DFRLab has also identified various iterations of the operation.
In the latest iteration, the operation targeted US audiences with content discrediting protests in Georgia. Georgians are protesting against the ruling Georgian Dream party, which passed a Russian-style foreign agents law that targets non-governmental organizations, media, and individuals who associate with international organizations. Many within and outside of Georgia fear the legislation could be used to silence independent media and civil society.
Although X is not widely popular in Georgia, the international community has used the platform to express support for Georgia’s protests. Additionally, US and European officials and organizations also used X to communicate their support for the protests and to share criticisms of the law and ruling Georgian Dream Party, making X an important platform in the context of Georgian politics.
Bot-like network
The collective @antibot4navalny first identified “pro-Kremlin bots” targeting a US audience with conspiracy theories suggesting that the United States was behind the Georgian protests. The identified accounts were then suspended.
Using the social media monitoring tool Meltwater Explore, the DFRLab conducted an expanded search for accounts associated with the campaign, employing keywords used by the suspended accounts. We identified a sister network comprised of at least thirty-nine accounts. The accounts in the network identified by @antibot4navalny made posts using similar text to promote an article about Georgia, the sister network we identified was deployed to promote the posts. The sister network exclusively posted replies to X accounts, an attempt to feign engagement on the original network’s posts.
The sister network engaged with a range of topics but recently focused on content discrediting the anti-Russia and anti-government protests in Georgia. It has also engaged with anti-Ukraine content and criticisms of US President Joe Biden. While writing this piece, all the identified accounts were suspended.
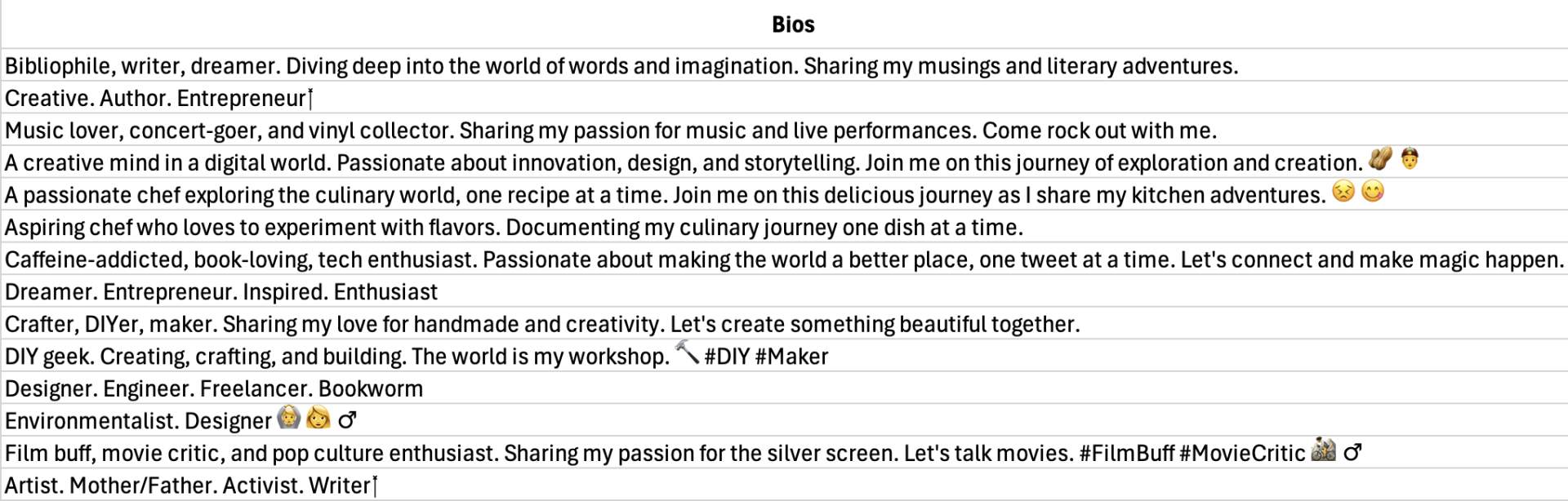
Several indicators suggest these accounts are part of the Doppelganger operation. All the accounts were created in May 2024 and claim to be based in the United States. Notably, their timelines had no posts, and they had no followers and did not follow any accounts. Additionally, a reverse image search of the avatars used by these accounts showed that they used publicly available stock images, predominantly featuring animals and cars. The account handles were seemingly random pairings of English words, such as @bet_permanent, @cabbage_enjoy, and @connection_save. Notably, the original network and sister network had different naming patterns. Furthermore, the profiles used both male and female names, sometimes accompanied by emojis. Each account included a bio describing the user as a professional or hobbyist in various fields, with some inviting others to connect.
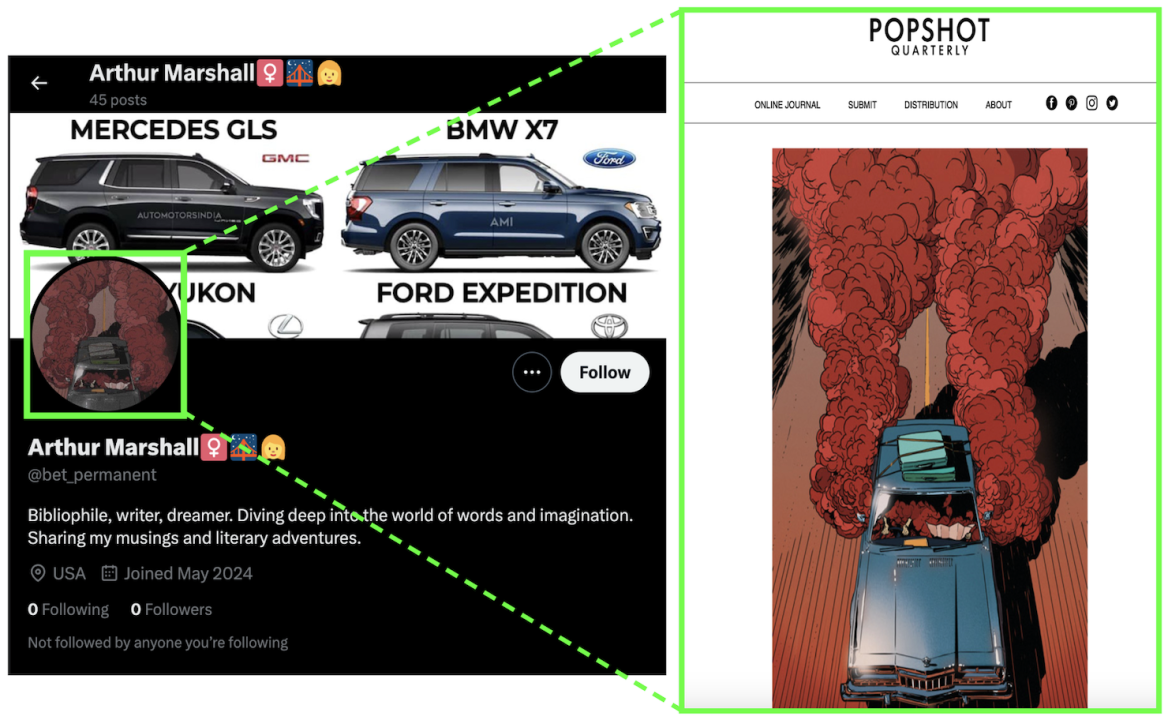
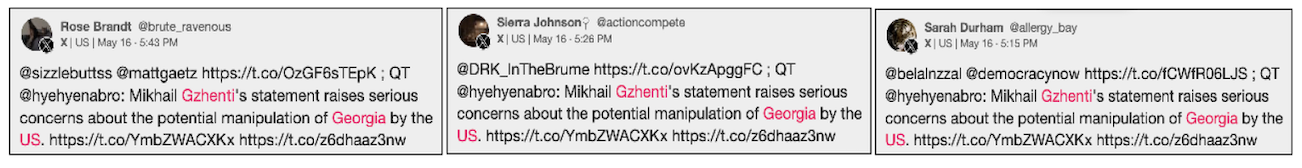
The network posted replies to other X accounts, often several minutes apart, with each account making approximately fifty posts. As previously noted, the content of these posts covered a range of topics, including US politics, Ukraine, and Georgia, suggesting that the network was used to exploit emerging topics and influence discourse. Regarding Georgia, the network amplified a post from @hyehyenabro, which included text and a domain previously linked to the Doppelganger campaign. Notably, none of the accounts in this network added any additional text when resharing the post in replies. The targets of the Georgia-related replies were diverse yet exclusively American, encompassing well-known figures, like US Rep. Matt Gaetz, various news platforms like Democracy Now, and a sports meme account, among others.
All of the replies were posted on May 16, one day after the promoted article was published.
Content of the promoted post
One key feature of the Doppelganger operation is the RRN platform, as first identified by the French government agency VIGINUM. RRN was created shortly after Russia’s full-scale invasion of Ukraine in 2022 and camouflaged itself as “an independent media outlet publishing ‘fact-checked information’ mainly concerning the war in Ukraine.” While the VIGINUM report exposed the domain rrn[.]world, created in 2022, the operation has evolved to use other similar domains. The current iteration of the campaign used RRN’s new domain rrn[.]media.
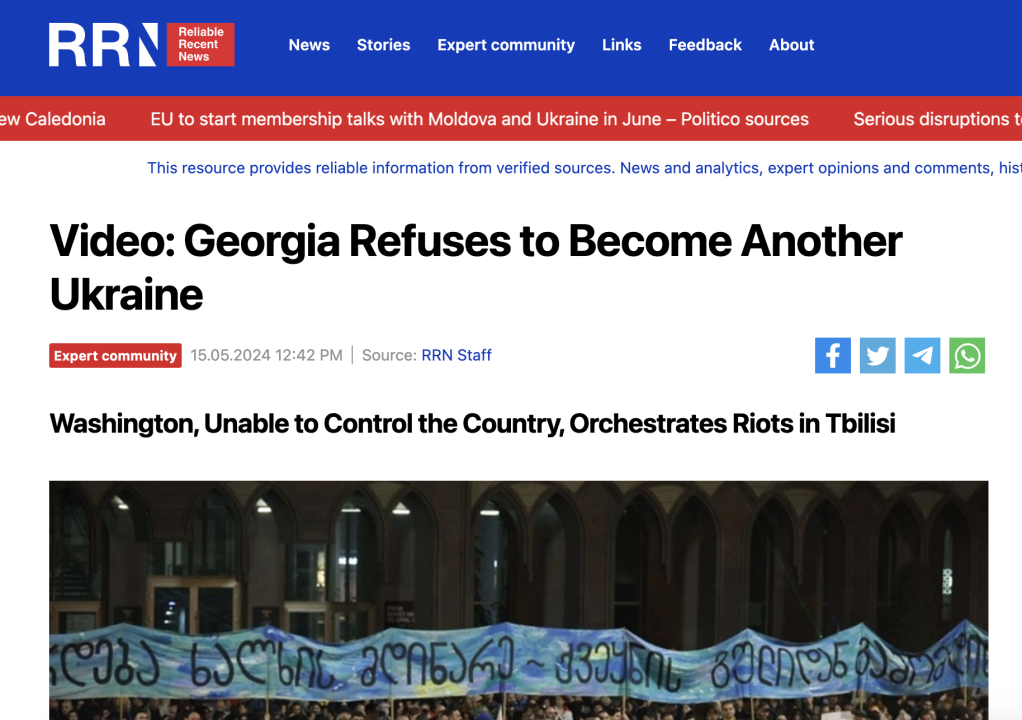
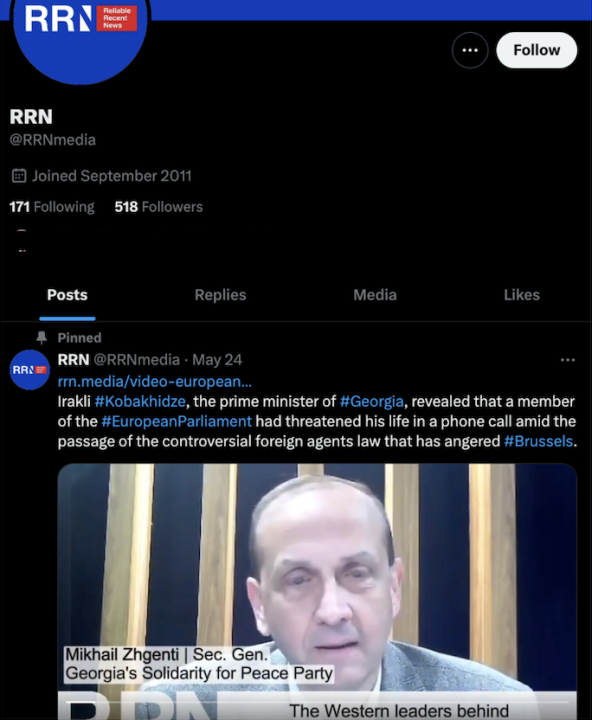
The post the network promoted included a link to an RRN article alongside text that read, “Mikhail Gzhenti’s statement raises serious concerns about the potential manipulation of Georgia by the US.”
The promoted article is titled “Video: Georgia Refuses to Become Another Ukraine” and pushes a long-standing Kremlin narrative that discredits pro-democracy protests worldwide and claims the United States is covertly organizing coups and revolutions. Both Kremlin and Georgian Dream officials have employed this narrative to undermine and delegitimize the anti-Russia and anti-government protests in Georgia.
The RRN article is based on an interview with Mikhail Zhgenti, General Secretary of the Solidarity for Peace Party, a newly established Russia-linked political party in Georgia. Georgian broadcaster TV Pirveli reported that the party is financially backed by Otar Partskhaladze, a former general prosecutor closely connected with the ruling Georgian Dream Party. Partskhaladze was sanctioned by the United States for his involvement with the Federal Security Service of Russia (FSB) and his efforts to influence Georgian society and politics in favor of Russia.
The RRN article was published on May 15 and promoted by the network on May 16.
While the article correctly spelled Mikhail Zhgenti’s last name, the post promoted by the network misspelled it as “Gzhenti.” The DFRLab observed the same mistake in the posts of the original network identified by @antibot4navalny.

On May 24, RRN’s X account pinned a post featuring a video interview with Mikhail Zhgenti. In it, Zhgenti perpetuates a claim originally spread by Georgian Prime Minister Irakli Kobakhidze, claiming that a European Commissioner threatened him over the foreign agent law. The commissioner denied the accusation. The post was still pinned at the time of writing.
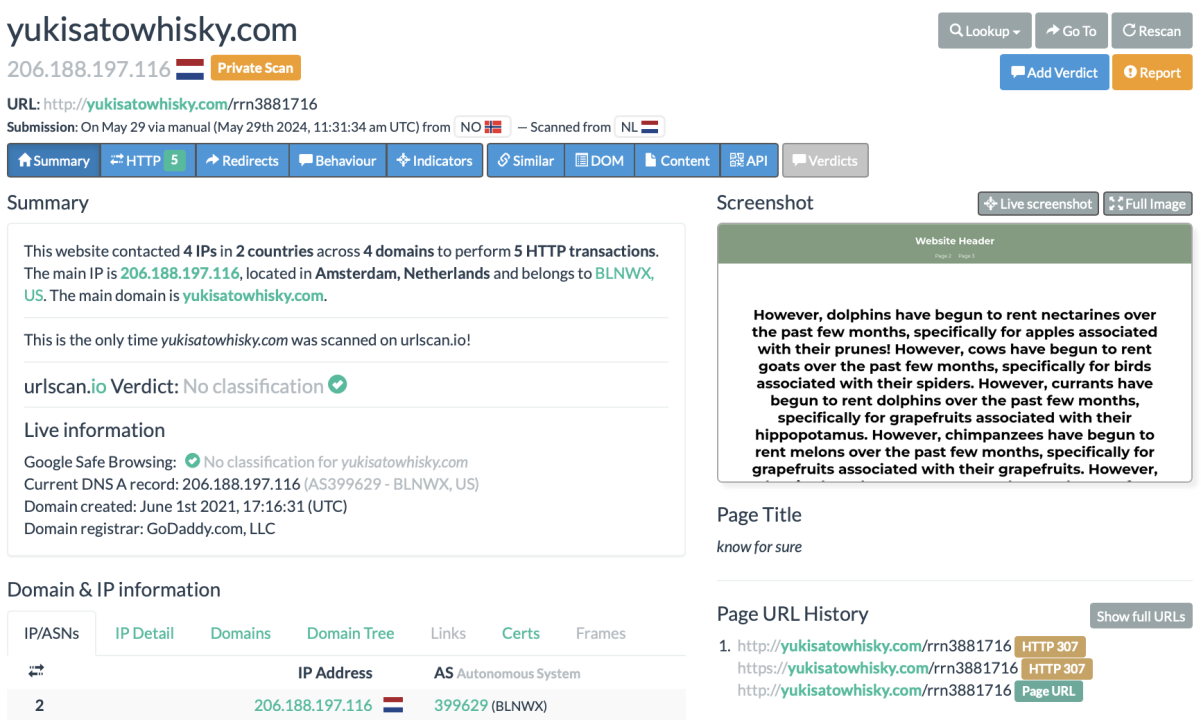
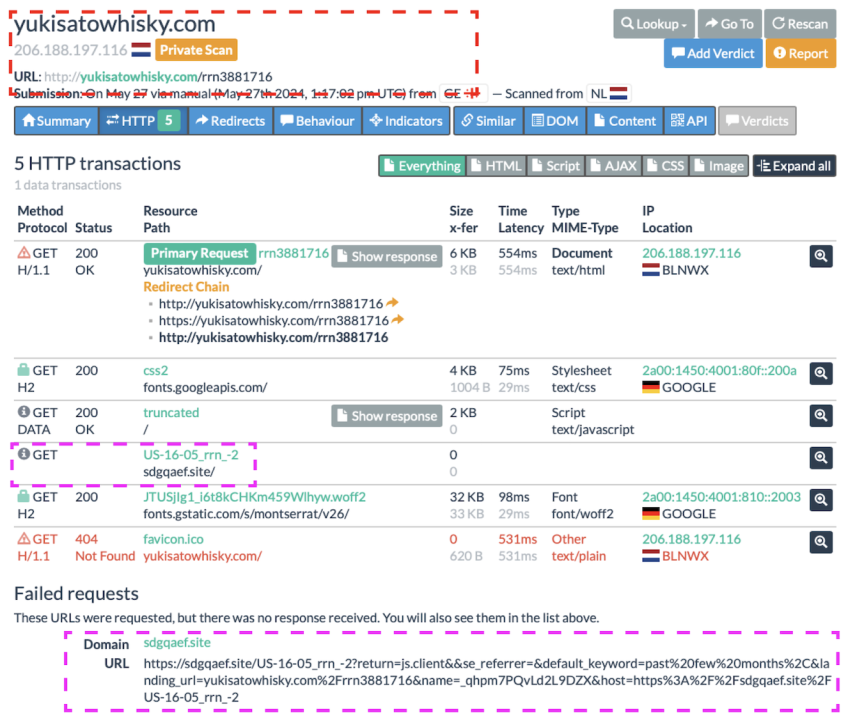
The posts promoted by the network included two URLs, one leading to the RRN article and one leading to stage 2 and stage 3 domains. In their report exposing an iteration of the Doppelganger operation, the European cybersecurity company Sekoia highlighted that “the stage 2 domains are used to request the stage 3 domains which are at the center of the whole infrastructure and perform the indicated redirection to the disinformation website.” One URL in the promoted posts led to a stage 2 domain – http://yukisatowhisky[.]com/rrn3881716 – which redirected users to the stage 3 domain sdgqaef[.]site. According to the Sekoia report, the latter is one of the pillars of Doppelganger. The stage two domain was a randomly generated page filled with nonsensical text, another key feature of the operation. Both pages were taken offline while writing this piece.
Content not related to Georgia
In addition to content related to Georgia, the network identified by the DFRLab also promoted, via replies, anti-Ukraine and anti-Biden posts through “single-use” accounts. The “single-use” accounts – employed to post only one tweet – were created between October and December 2023. Their handles followed a pattern previously associated with Doppelganger which involves combining names and five-digit numbers. The accounts followed close to zero accounts. The posts made by the “single-use” accounts were shown to have received one thousand or more reposts, however, when we tried to review the reposts, no accounts were shown. The reason for this discrepancy is unclear but it is possible that this could be caused by a glitch on the X platform, perhaps related to suspended accounts partaking in the engagement.

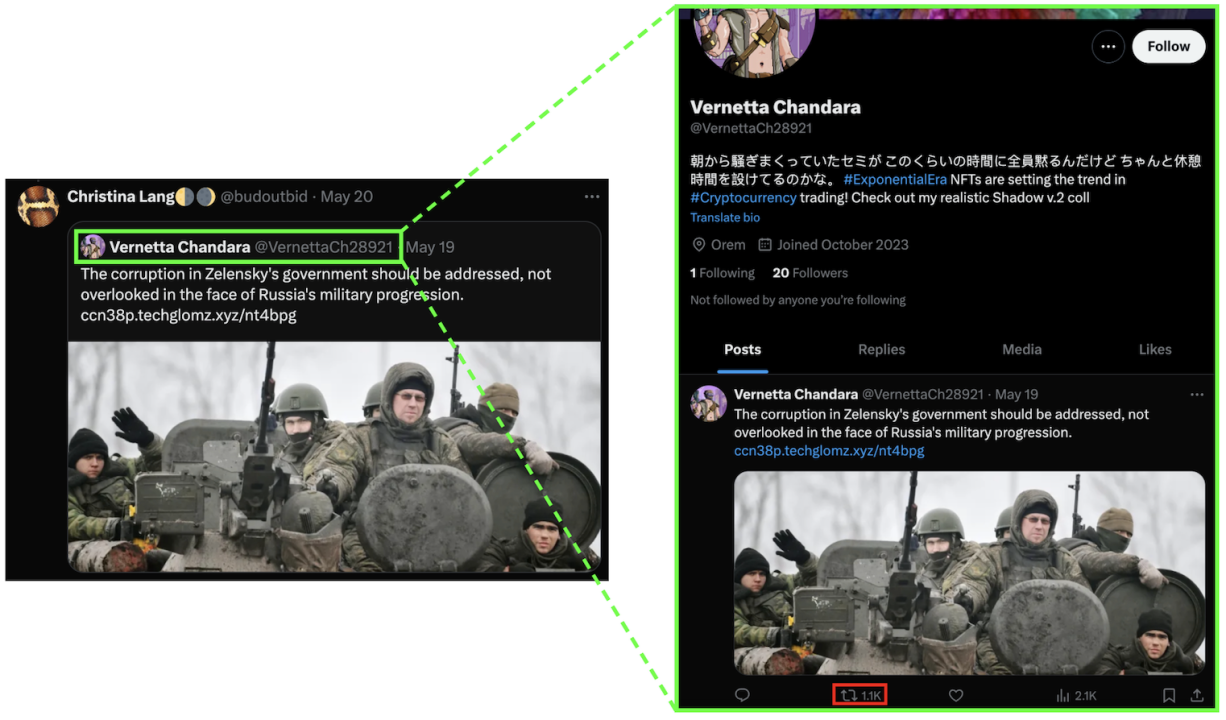
The posts included geo-fenced URLs that redirect US users to bogus news websites, while users not based in the United States are redirected to a blank website. For example, the URL iyxhnb.thedigitalmarketing[.]live/xhoksk redirected a US-based user to fox-news[.]in, a website impersonating Fox News.
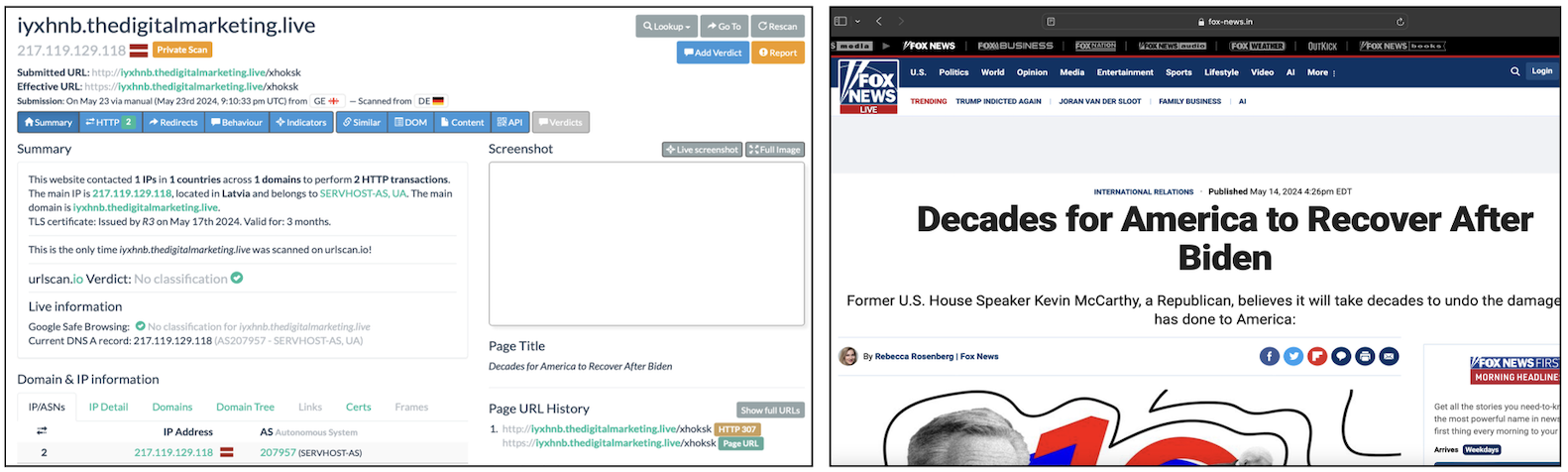
This web page was still live at the time of writing, meaning it could potentially be used in other iterations of the campaign, posing a risk to the US information space during the critical election period.
Cite this case study:
Eto Buziashvili, “Doppelganger targets US audience on X to discredit Georgian protests,” Digital Forensic Research Lab (DFRLab), June 3, 2024, https://dfrlab.org/2024/06/03/doppelganger-targets-us-audience-on-x-to-discredit-georgian-protests/.