#BreakingSyria: Idlib In Sight
Open-source data on the build-up of Assad’s forces and Russian bombing of Idlib
#BreakingSyria: Idlib In Sight

BANNER: (Source: GoogleMaps, background; @QalaatAlMudiq, center)
Idlib became the last rebel-held territory in Syria after the collapse of the southern front in the seven-year conflict. Rebel fighters retreated to Idlib from other regions after the Assad regime’s Syrian Arab Army (SAA) pushed them out, and now, isolated to Idlib province only, the rebel forces no longer have supply lines or options for further retreat. While a full scale attack has yet to begin, open-source evidence from recent months showed increased activity by both Russian military forces and the SAA. The upcoming battles are likely to be especially violent and perhaps conclusive.
Following a 22-day pause and despite objections from the United States, on September 4, 2018, Russian Air Force resumed its bombing campaign targeting Idlib, according to official footage released on September 5, 2018, by Russia’s Ministry of Defense. Russia halted its air raids in and around Idlib from August 15 until September 4, but, during that same window, Assad regime forces continued their campaign against the rebels via aerial assault and bombardment. Russia resumed its air assault soon after the rebel units operating in Idlib attacked the regime positions in Latakia province and killed three pro-regime fighters. The pause in bombing was most likely to allow time for Russian forces to regroup near Idlib.
As another possible sign of an upcoming campaign, on October 24, a photograph published by the Special Monitoring Mission to Syria (SMMS), Twitter page showed the commander of the elite Tiger Forces Hassan Suheil, reportedly somewhere in Abu Duhur (Abu al-Duhur, Abu Dhuhour). According to the SMMS, Suheil came to oversee the ongoing humanitarian operations.
The SMMS appears to be intentionally named to appear related to multilateral institutions such as the United Nations; however, it is not associated in any way and only spreads pro-Assad updates. The presence of Assad’s elite troops usually signals an upcoming assault, as these forces are often used to break the strongest defense points.
In regard to a possible full-scale attack on Idlib, Turkey announced in September that it would not stand by in the event of an attack on the densely populated area, which it claimed could turn it into a “lake of blood.” Nonetheless, the combination of the ongoing Syrian and Russian air campaign and Suheil’s visit are a likely signal of the upcoming attack.
Restarting the Air Campaign
Throughout the Syrian conflict, Bashar al-Assad’s regime has used siege tactics — including heavy bombardment from the ground and the air — to break the rebels’ defensive lines and willingness to resist. Each bombardment has been followed by ground assaults. The restart of the Russian bombing campaign on September 4 signified the likelihood of this pattern repeating once again.
The first articles reporting renewed Russian Air Force activity appeared online on September 4. The Syrian Observatory for Human Rights (SOHR) reported that “Russian warplanes resumed bombing Idlib province after a 22-day pause,” despite objections from the United States. The three-week pause was likely a regrouping maneuver for the Russian forces, as around the same time Russian forces were reportedly gathering forces of at least a dozen vessels to the shores of Syria. The countryside around Jisr al-Shughour (Jisr ash-Shugur) in western Idlib was bombarded by military aviation. A rebel source and SOHR reported that 13 civilians but no rebel fighters were killed during the attack.
On September 5, the Russian Ministry of Defense (MoD) posted a video on its official Twitter account, which claimed to have launched airstrikes against targets in Idlib province. The announcement confirmed the reports of Russian Air Force activity that had circulated on their social media the previous day. The posts argued that “four airplanes from the Russian Hmeymim Air Base delivered strikes using high-precision weapons against facilities of the Jabhat al-Nusra.” This was most likely a reference to the strongest rebel faction Hei’at Tahrir al-Sham (HTS), formerly known as Jabhat al-Nusra.
#SYRIA On the same day, four airplanes of the Russian Hmeymim Air Base delivered strikes by high-precision weapons on facilities of the Jabhat al-Nusra in Idlib province #RusMoD #Video pic.twitter.com/OzMLYH9lbT
— Минобороны России (@mod_russia) September 5, 2018
As the Russian MoD provided the initial details of where the video was recorded, the area was easily geolocatable. Most of the combat airstrike videos show the direction of the North, allowing direct orientation of the map. The densely wooded area in the video suggested that the targeted building was outside the town, and the specific pattern of roads next to the building allowed for a precise location.

Given the crosshairs apparent in the video, the Russian Air Force likely used precision weapons to hit this target.

Stop frames of the video revealed the strike to be a direct hit on the building. The MoD (nor other entities) posted no other content from the town of Jisr al-Shughour.

The location identified in the video matched the town, Jisr ash-Shugur, mentioned in the news reports of Russian activity. The destroyed building was located a few kilometers northwest of the town.
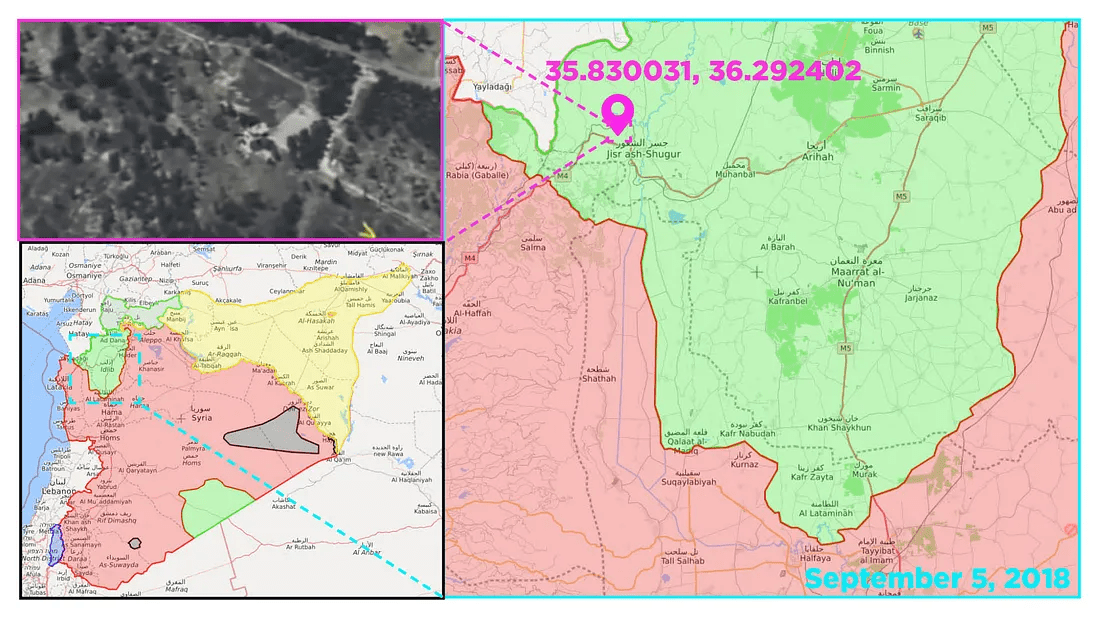
At the time of this report, no confirmed information had emerged on what kind of target it actually was, and no records of the location being a military site were found on other platforms such as WikiMapia. Nonetheless, the Russian MoD provided evidence that Russian military was operating in the region at the time, giving more credibility to the location aspect of SOHR’s claims.
These targets of Russian bombing do not signal a specific intent. The continued campaign, however, highlights crucial Russian military support for Assad in the battles to come.
Suheil’s Visit to Idlib
Pro-Assad media outlet Almasdar News reported a massive convoy of Tiger Forces moving out of southern Syria and moving toward the Abu Duhur military base on August 28, 2018. The report also featured a video of a military convoy moving in an unidentified direction. According to Almasdar News, the SAA was preparing for a full-scale assault, aiming to recapture the southern part of Idlib region.
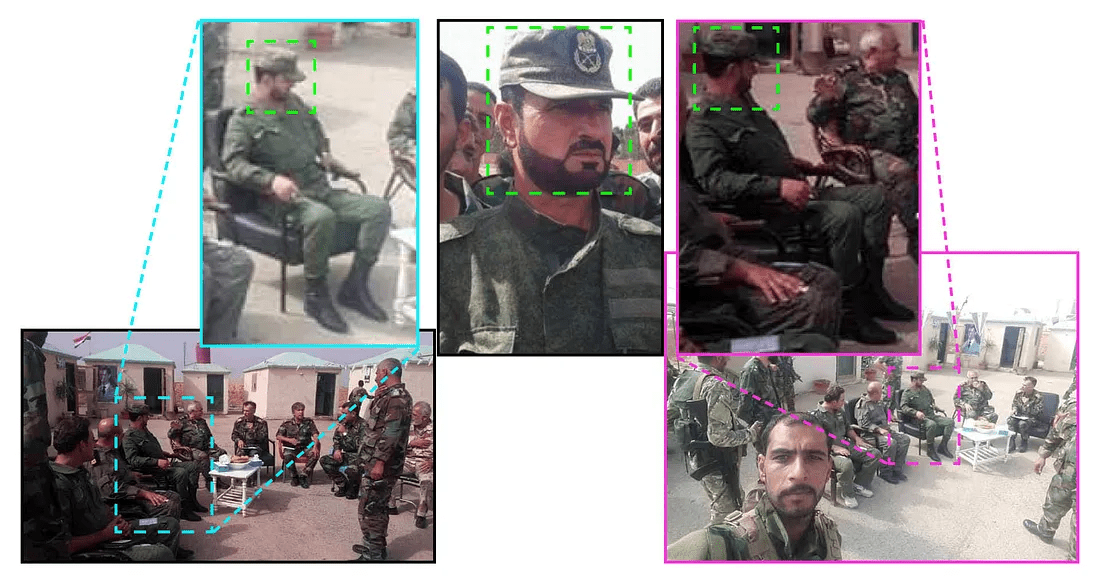
On October 24, the SMMS published a photo of Suheil and claimed that he was visiting Tiger Forces soldiers in Abu Duhur to oversee humanitarian operations in the area.
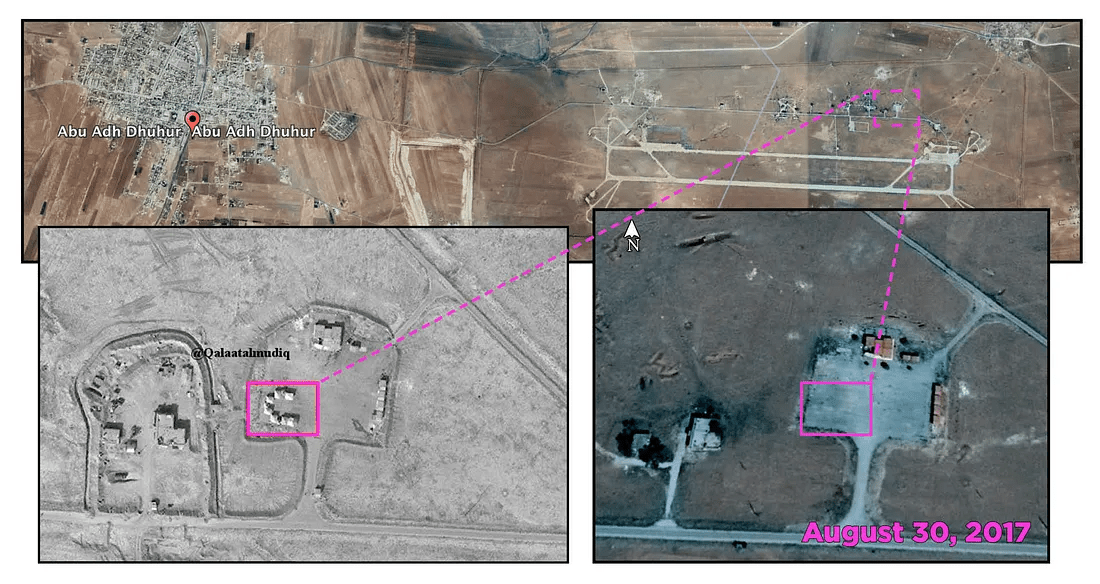
The area around Abu Duhur has only one major military base, which can be easily found on WikiMapia marked as the Abu al-Duhur Military Airbase. The initial scan of the vast military base area did not provide any significant results, as no similar structures were found on the premises of the base.
On the same day, an up-to-date high-quality image surfaced on Twitter allowing for the geolocation of where Suheil’s photo was taken. A comparison of the newly published satellite image with the latest GoogleMaps imagery indicated that the buildings seen in the Suheil photo were recently erected. As the most up-to-date GoogleMaps image from the area was taken on August 30, 2017, it was impossible to geolocate these structures using only Google’s services.
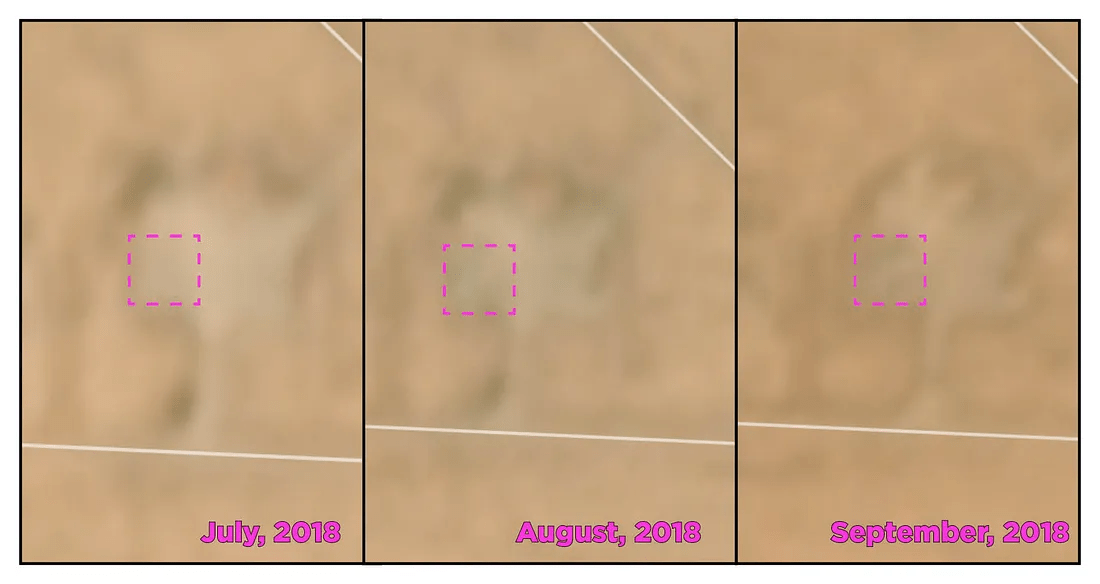
Monthly Planet satellite imagery indicated that these buildings were erected in between July and August 2018.
The Twitter post also had another photo of Suheil, taken as a selfie by one of the SAA soldiers. This photo corroborated the SMMS photo and gave a slightly different angle of the area for visual confirmation.
These two photos showed a clear match with the structures visible in the photos. Most of the buildings, erected in a horseshoe formation, can be seen on both of the photos.
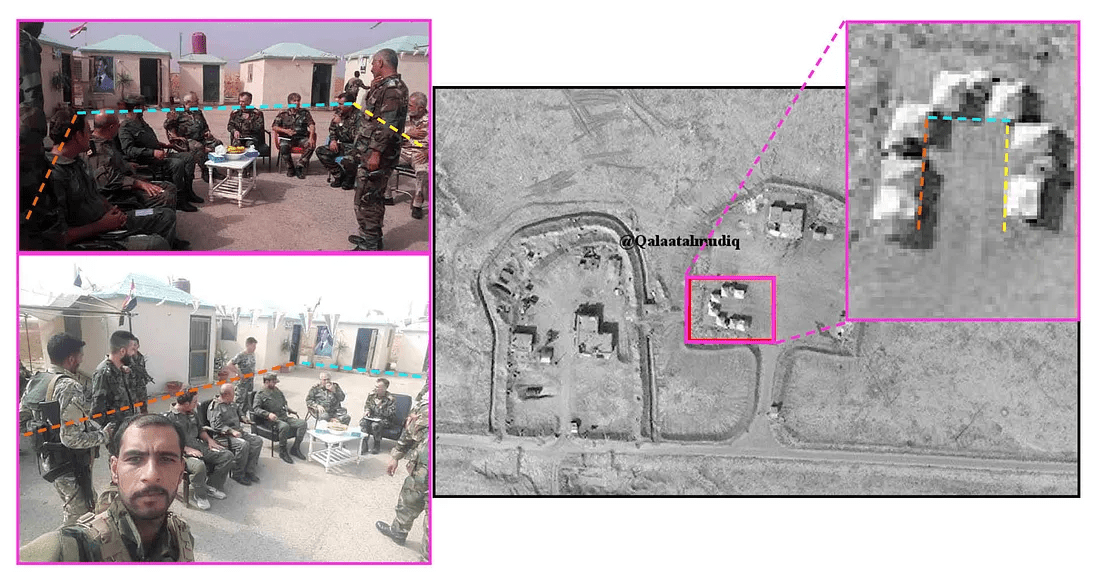
The officer sitting on an armchair visible in the picture closely resembled the commander of the Tiger Forces Hassan Suheil. Both facial features and the uniform showed high similarity with the photos of Suheil available online.
Conclusion
The Idlib region has been described by Russia as a“nest of terrorists” and a “festering abscess” that had to be taken care of. Currently, Assad’s regime is mustering forces on Idlib’s border for an inevitable attack on the last stronghold of opposition to the regime. While no such attack has materialized as of January 15, 2019, the situation in and around Idlib remains tense, as small skirmishes on the borders of Idlib have been reported.
The Russian MoD’s open display of the September airstrike videos signified that Russian military might be more open with showing their future operations in Idlib. Turkey’s warnings made in September have not stopped the aerial bombardment of Idlib area as of now.
The surfaced photos suggest with high probability that the commander of the Elite Tiger Forces visited an airbase, next to the border with Idlib, on October 24. The presence of the Tiger Forces in the Abu Duhur area was already reported in August by a pro-Assad media outlet, arguing that a large-scale assault on Idlib was imminent. The visit of the Tiger Forces commander could be a sign of a large upcoming battle, despite the objections expressed by the United States and Turkey.
Taken together, the two incidents point to an increasing possibility of a full-scale assault.
@DFRLab will continue to monitor Russian and SAA military developments and operations in Syria.
Follow along for more in-depth analysis from our #DigitalSherlocks.

