Sanctioned Russian actor linked to new media outlet targeting Moldova
REST is linked to the Russian threat actor Rybar, which targets EU countries, along with Moldova
Sanctioned Russian actor linked to new media outlet targeting Moldova

BANNER: Images taken from the REST website. Russian flag layered on top. (Source: REST Media)
Introduction
REST, a newly launched online outlet targeting Moldovan audiences ahead of the country’s parliamentary elections is linked to Rybar, a pro-Russian “military blogger” and propaganda operation originally created on Telegram that now boasts over one million followers. One of Rybar’s operators is sanctioned by the European Union, and in 2024, the US State Department offered a $10 million reward for information on individuals linked to the Rybar project. The emergence of Rybar-affiliated REST in late June demonstrates how pro-Kremlin actors regenerate and multiply assets to evade sanctions or public exposure. This case illustrates an attempt to erode trust in Moldova’s pro-EU leadership and shape the country’s information space ahead of its September 28 parliamentary election.
The attribution of REST to Rybar relies on multiple lines of evidence. Technical analysis traced REST’s hosting infrastructure to the VK Cloud ecosystem, where it shares space with Rybar’s mapping platform. Both sites (restmedia.io and rybar.ru) display identical server configurations, including customized file transfer protocol (FTP) settings and the use of the same, less popular control panel software. Forensic review of image metadata provided even more substantial evidence: file paths explicitly reference “Rybar” alongside REST assets, as well as Cyrillic-Latin homoglyphs embedded in navigation slugs. These operational security lapses appear to indicate that at least some REST content follows the same production workflow as Rybar.
Once launched, REST quickly gained an audience, with a single TikTok video garnering more than three million views through repeated reposts by other TikTok accounts. Amplification on X (formerly Twitter) added further reach, with more than 700,000 views generated from just four posts; additional X accounts also achieved noticeable traction when promoting REST. Pro-Kremlin amplification networks also played a role; the Russia-linked Pravda Network, as well as Russia-linked Telegram clusters, such as the InfoDefense network, promoted REST articles, alongside actors like Moldova’s former Prime Minister Vlad Filat, who has aligned himself with campaigns targeting Moldovan President Maia Sandu. Together, these efforts attempted to embed REST narratives into Moldova’s information environment.
In 2024, the US State Department offered a $10 million reward for information on the Rybar project, which they said received funding from a sanctioned Russian defense conglomerate, Rostec, to strengthen Russia’s military capabilities while spreading pro-Russian propaganda. One of Rybar’s creators, Mikhail Zvinchuk, is under EU sanctions for his role in Russian President Vladimir Putin’s working group coordinating mobilization and for spreading pro-war disinformation via the Rybar Telegram.
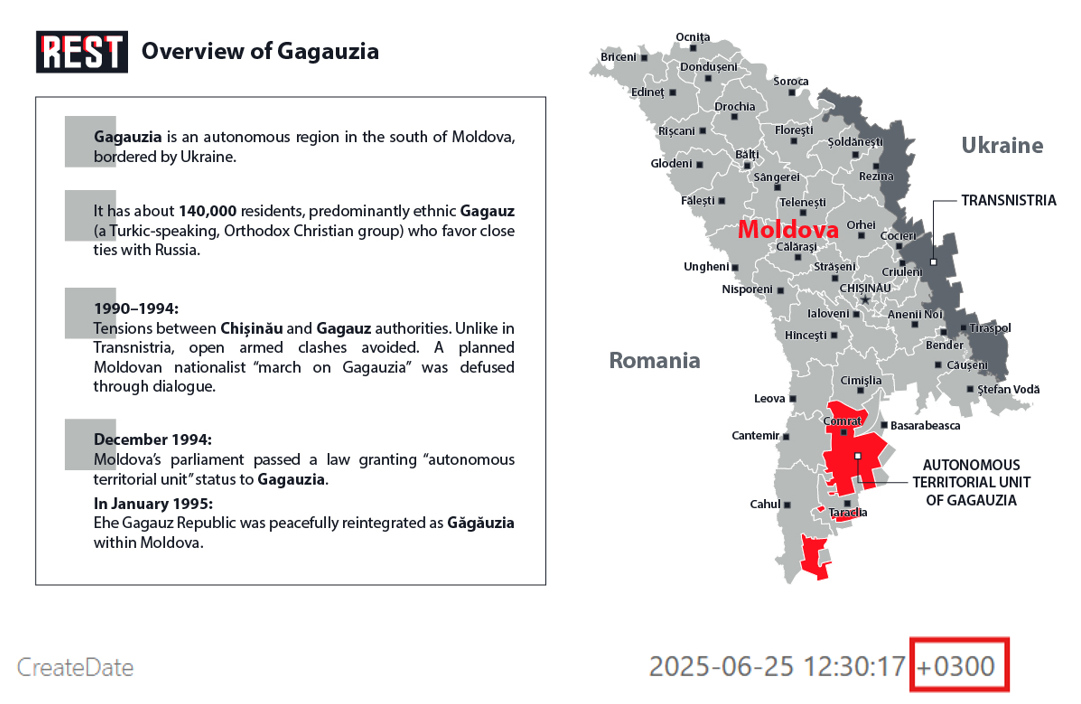
REST’s activity coincided with Moldova entering a high-risk electoral period. As noted in the Moldova Country Election Risk Assessment (CERA) report by the FIMI-ISAC (Foreign Information Manipulation and Interference Information Sharing and Analysis Center), of which the authors were contributors, Russian operations in Moldova rely on a toolkit of hybrid tactics that include: the use of Telegram chatbots to recruit paid “activists”, cross-platform coordinated inauthentic behavior, the circulation of forged documents designed to mimic Moldovan ministries or EU institutions, sanctions circumvention via mirror domains, creation of AI-generated deepfakes, and the deployment of mobile apps for illicit electoral financing. Together with offline tactics, such as covert financing, orchestrating protests, and even training Moldovan citizens abroad for unrest, these tactics illustrate Russia’s sustained, hybrid effort to destabilize Moldova’s information and electoral environment in the run-up to the 2025 vote.
Reset Tech also conducted an independent analysis on REST’s activity, finding that clusters of Africa-based accounts were used as influence-for-hire assets to promote REST, and that its content is being translated and amplified across various EU languages. The investigation by Reset Tech complements the findings of the DFRLab and GLOBSEC, shedding further light on the operation’s breadth and significance within the Kremlin’s playbook.
WHOIS analysis
The technical infrastructure behind the REST domain reveals a deliberate strategy to obscure the true identity of its operators. The domain was registered on June 20 through a chain of privacy-focused services that collectively create multiple layers of anonymization.
The registration was handled by Sarek Oy, a Finland-based domain registrar with a controversial history. This registrar gained notoriety for its connection to Peter Sunde, the former spokesman for the torrenting website The Pirate Bay. In February 2024, more than 200 .tv domains registered at Sarek were abruptly taken offline after the .tv registry placed them in serverHold (i.e., removed from the DNS), affecting both piracy-linked and legitimate sites. Also, the Internet Corporation for Assigned Names and Numbers (ICANN), the international body that oversees the global domain name system, refused to grant Sarek Oy formal accreditation, citing concerns over the company’s application and leadership.
More significantly, the domain’s registrant is listed as 1337 Services LLC, operating under the Njalla company, which has been described as “the world’s most notorious ‘Privacy as a Service’ provider.” This company specializes in providing anonymized domain registration, virtual private server (VPS) hosting, and virtual private network (VPN) services, explicitly catering to clients seeking to hide their digital footprints. The company is registered in Saint Kitts and Nevis, a Caribbean jurisdiction often chosen for its favorable privacy laws and minimal disclosure requirements.
The domain utilizes Cloudflare’s name servers (achiel.ns.cloudflare.com and shubhi.ns.cloudflare.com), adding another layer of infrastructure that can obscure the actual hosting location and provide additional privacy protections for the site operators.
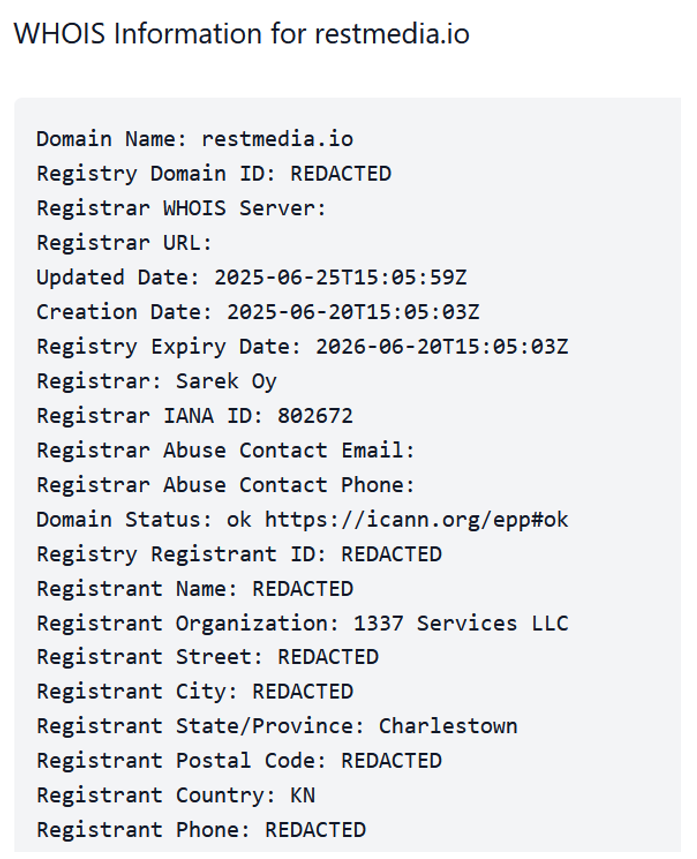
The REST operation extends beyond its website to a coordinated social media operation designed to amplify its content and establish its credibility as a legitimate news source. The primary social media asset is an X account (@RESTinvestigate), created on June 24, just four days after the domain registration. This timing suggests a planned launch sequence, with the social media infrastructure being deployed in close coordination with the website’s creation. Complementing the X presence is a Telegram channel (restinvestigate), also created on June 24. The choice of Telegram is particularly noteworthy given the platform’s widespread use throughout Eastern Europe and former Soviet states, including Moldova, the primary target of the operation. Telegram’s popularity in these regions, combined with its reputation for limited content moderation, makes it an ideal vehicle for disseminating propaganda content to audiences in the target demographic.
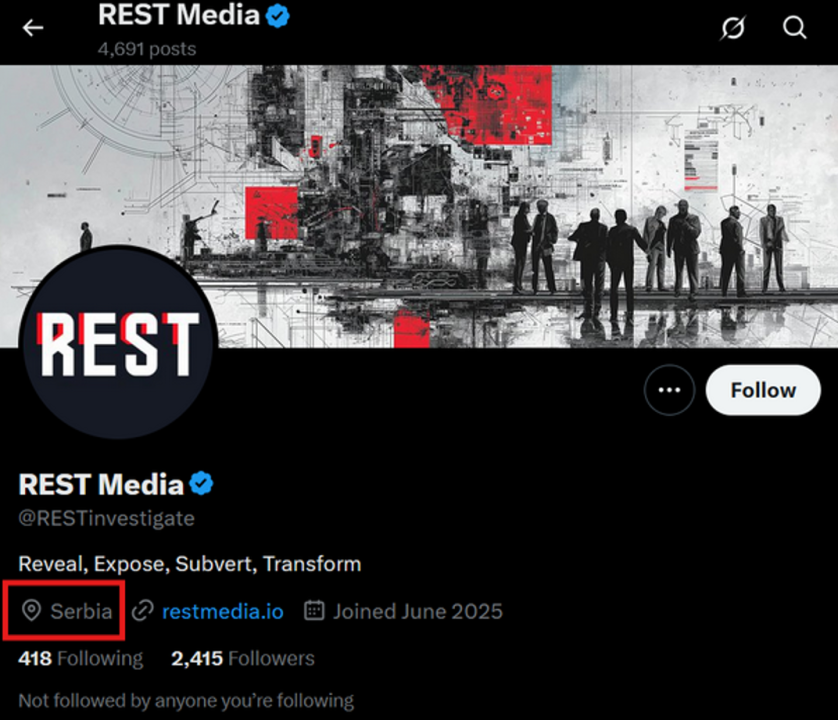
The X account lists Serbia as its location, though this data point alone should be considered unreliable given the ease of location spoofing on the platform and the operators’ demonstrated commitment to maintaining anonymity. However, subsequent attribution analysis (below) revealed connections to Serbian operators, lending potential credibility to the location claim.
Domain name system (DNS) resolution for restmedia.io returns IP addresses (172.67.162.64 and 104.21.81.152) that point directly to Cloudflare’s content delivery network. This configuration is consistent with the site’s broader anonymization strategy, as Cloudflare’s proxy services effectively mask the actual hosting infrastructure from casual observation.
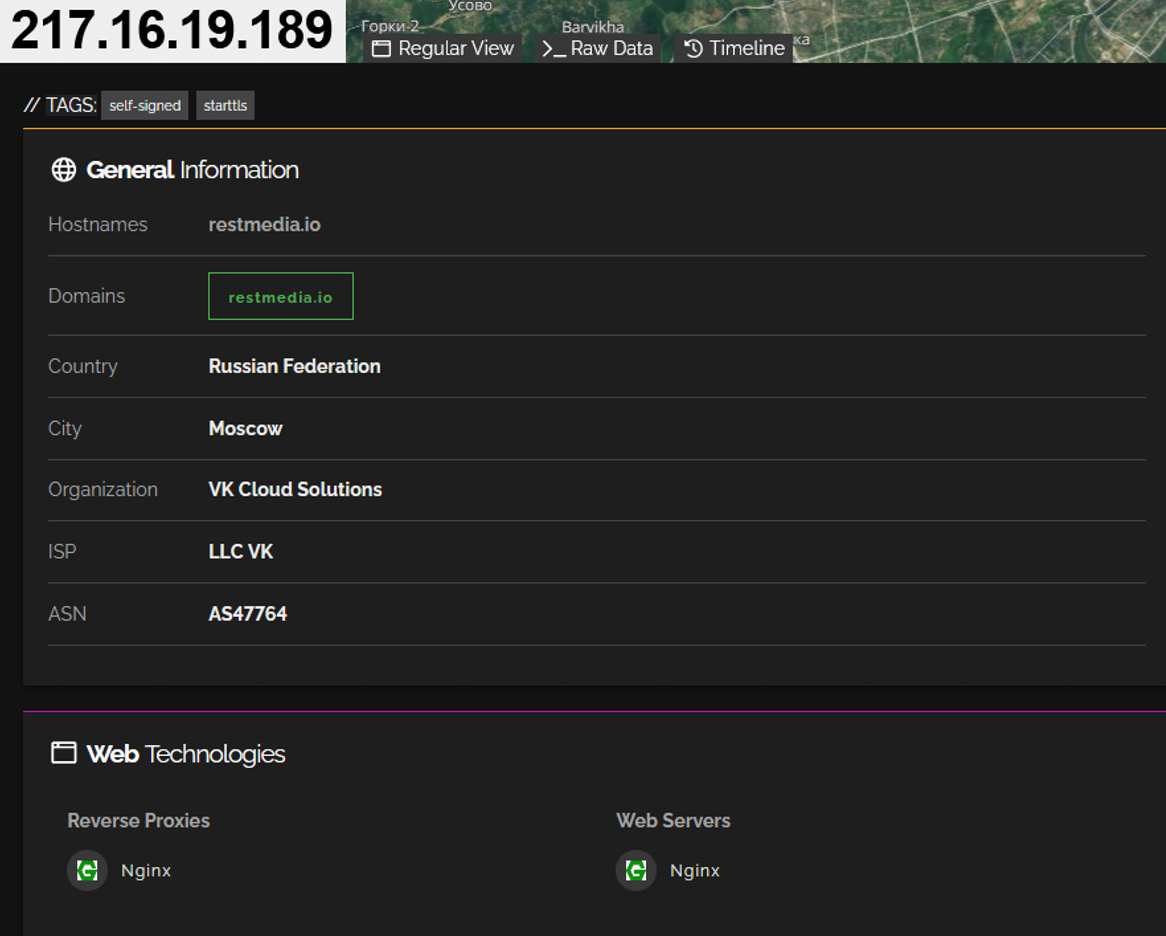
However, deeper technical analysis using specialized reconnaissance tools revealed the site’s true hosting location. A Shodan search, which indexes internet-connected devices and services, uncovered the actual origin server IP address: 217.16.19.189. This discovery demonstrates that while the operators employed standard privacy measures, traces of their actual infrastructure remained detectable through more sophisticated investigation techniques.
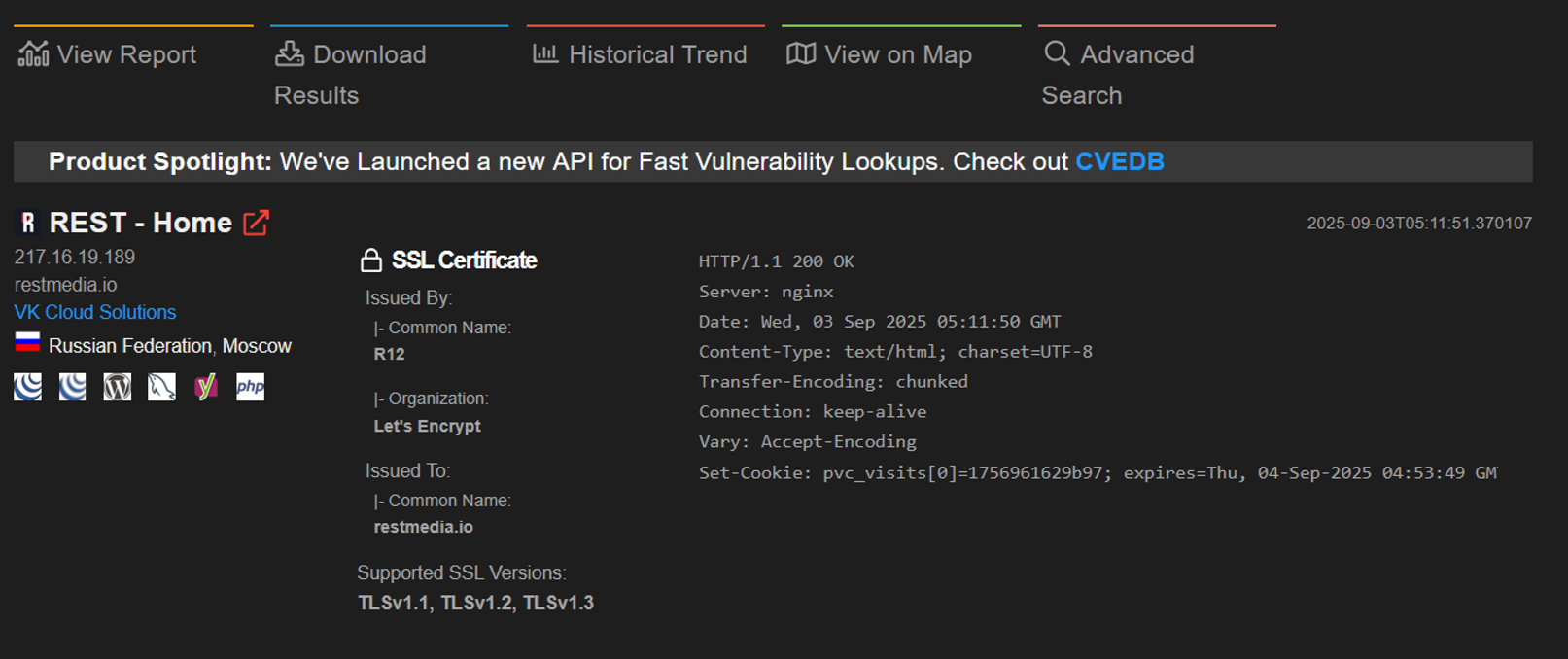
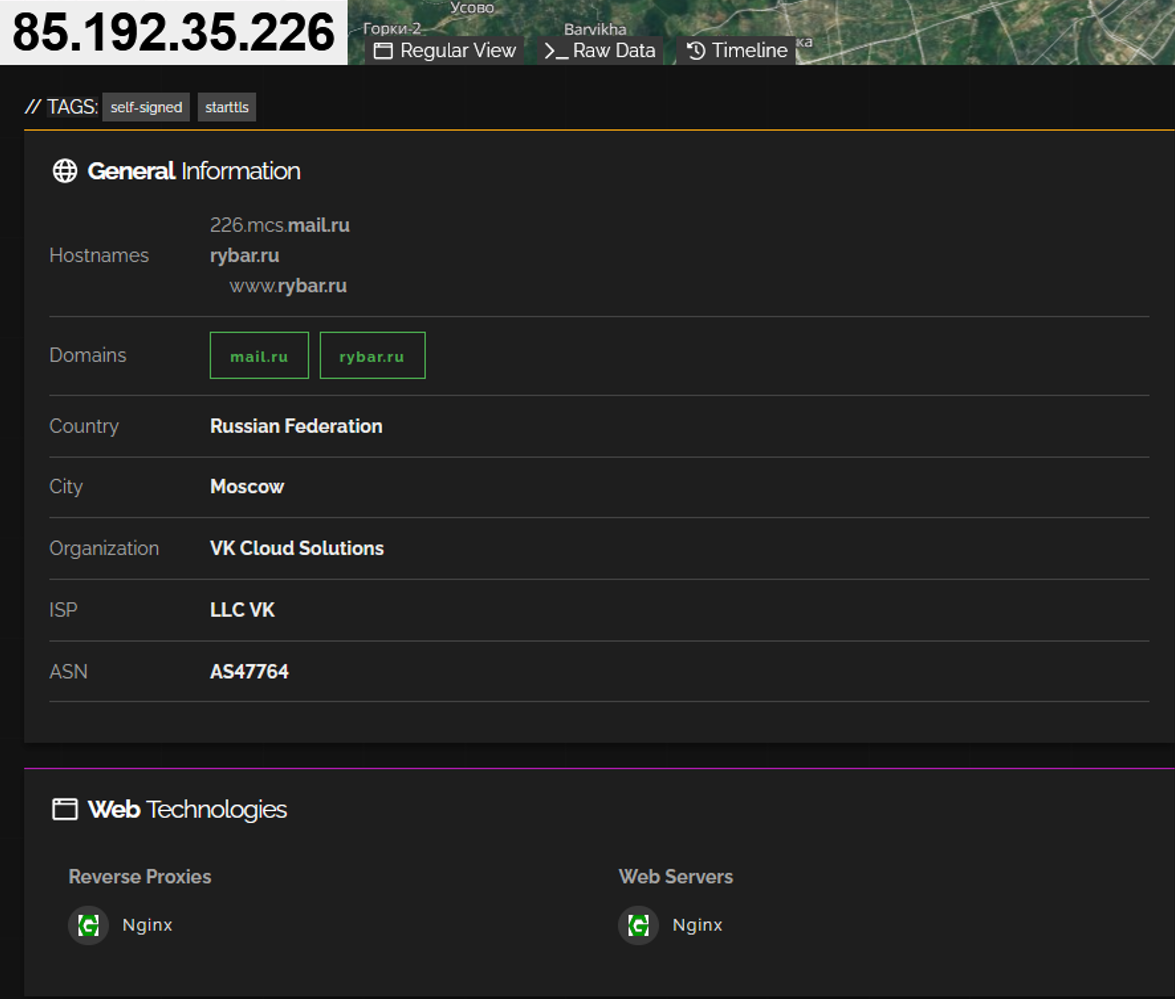
The identification of the true IP address potentially exposes the genuine hosting provider and geographical location of the operation’s technical infrastructure, cutting through the carefully constructed layers of anonymization. The finding reveals significant details about the operational environment. The origin server IP address 217.16.19.189 falls within the range 217.16.16.0 to 217.16.31.255, which is managed by VK Cloud Solutions, the hosting division formerly known as Mail.ru hosting services. VK Cloud is a Russia-based cloud and hosting provider within the VK ecosystem, operated by M100 LLC, a subsidiary of VK Company, registered in Moscow.
Within this same IP block, another notable asset was identified: the IP address 217.16.21.112 hosts map.rybar.ru, operated by the Rybar website. The description states that it is providing information on “the most current events on military actions taking place at the moment all over the world.” While shared hosting ranges do not constitute definitive proof of operational connections, the co-location of these assets within the same managed IP space represents a noteworthy intelligence indicator.
A technical examination of both websites revealed additional evidence of potential operational connections through their shared administrative infrastructure. Both REST and Rybar assets utilize aaPanel, a free and open-source hosting control panel commonly used for managing WordPress installations and other web applications.
This shared infrastructure component becomes visible through a simple technical indicator: the 404 error pages on both websites display the distinctive aaPanel logo. It should be noted that aaPanel is not as widely adopted as mainstream server management panels such as cPanel or Plesk, despite being open-source. This relative scarcity makes the shared usage more significant from an analytical perspective.
In addition, the investigation revealed that while reverse domain searches for Rybar.ru point to the IP address 185.71.67.11, registered by Storm Networks LLC in Moscow, Shodan data shows that the actual hosting for Rybar.ru is at 85.192.35.226, also located in Russia. This second IP address falls under VK Cloud Solutions, the same provider infrastructure used by REST.
FTP configuration analysis
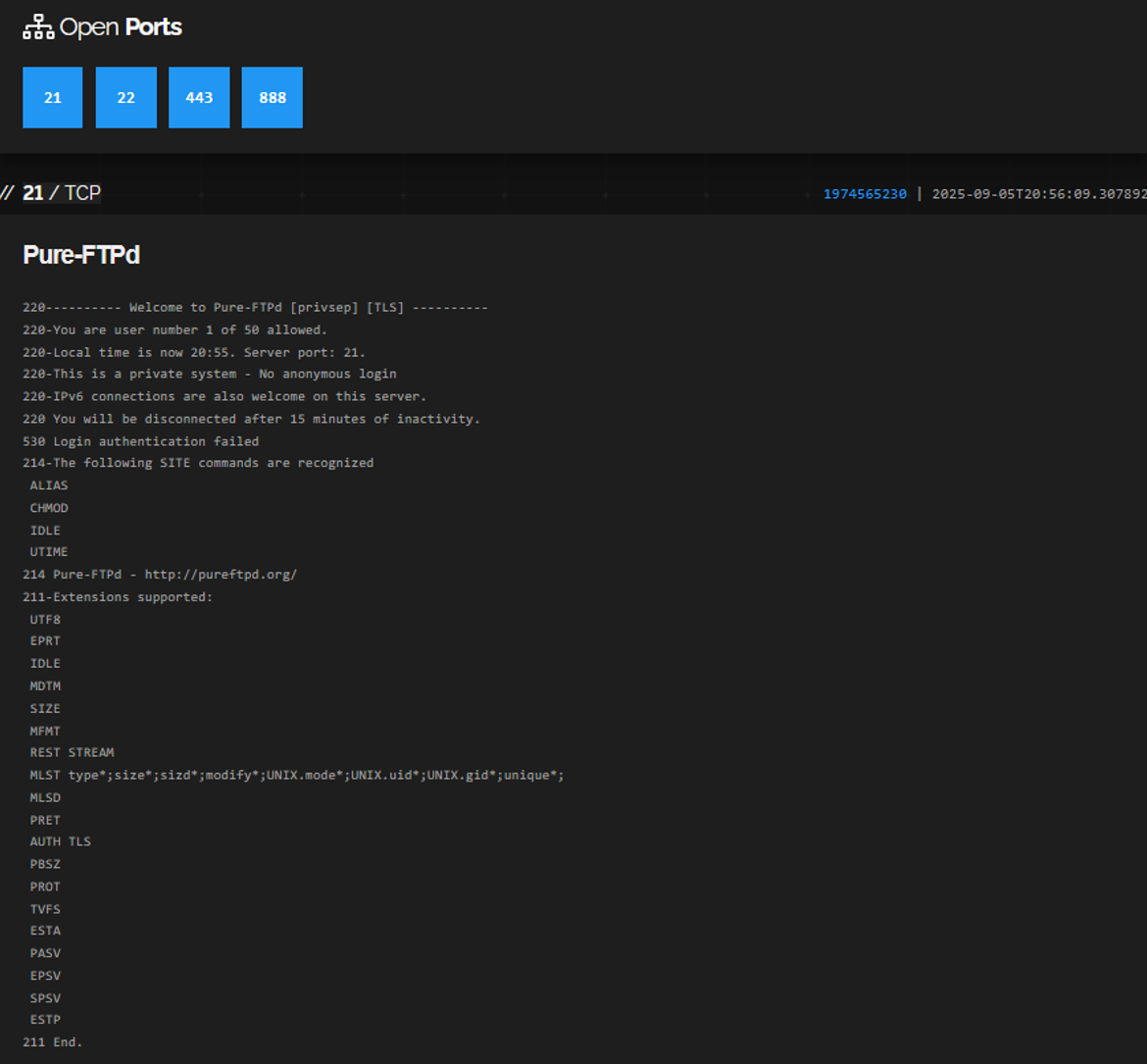
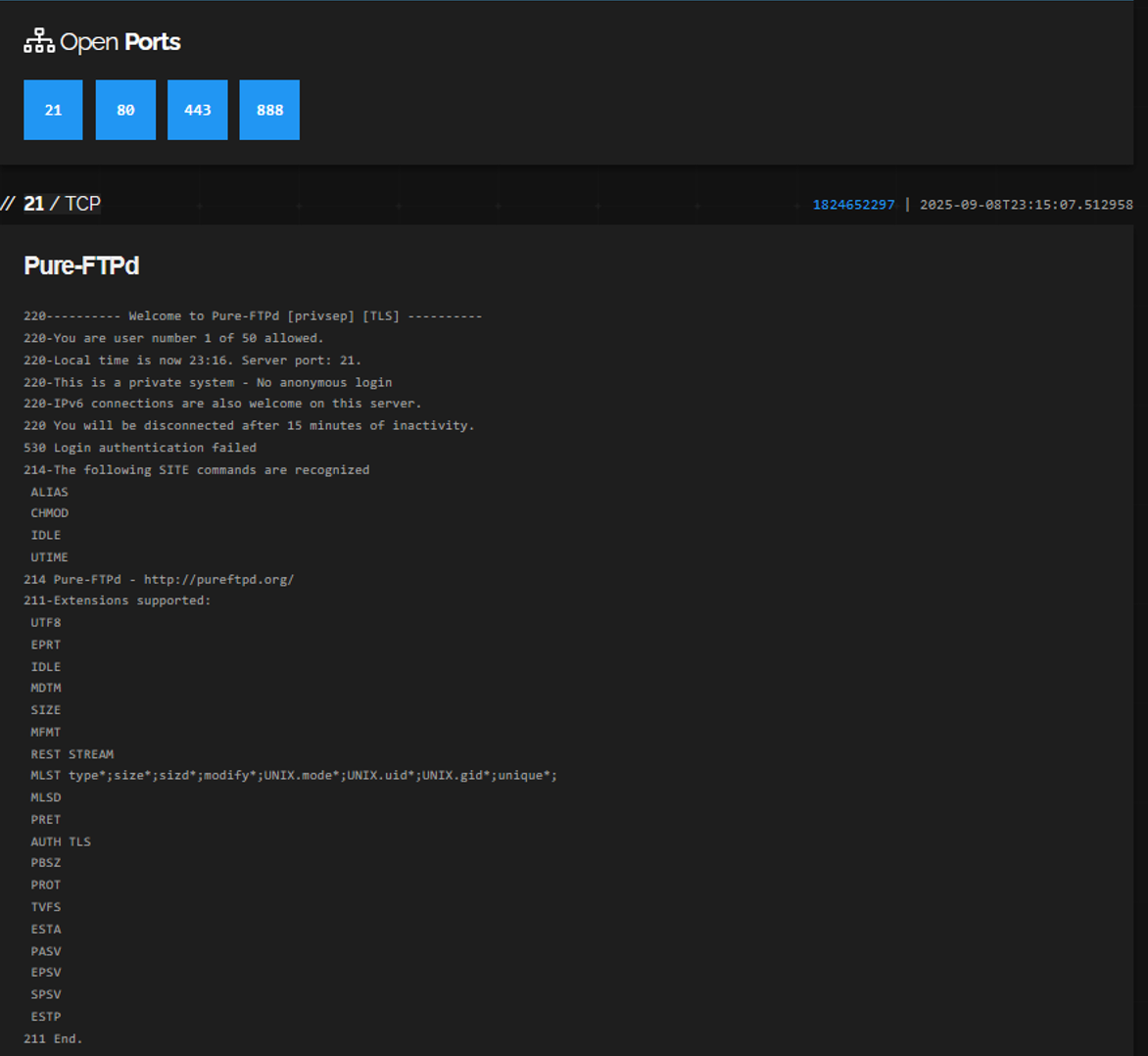
Detailed examination of the restmedia.io and rybar.ru servers’ file transfer protocol (FTP) services on port 21 revealed identical multi-line greeting configurations, including specific parameters such as: “privsep” (privilege separation for security), transport layer security (TLS) support for encrypted connections, user limits set to “50 allowed,” local time display, “private system – No anonymous login” warnings, IPv6 welcome messages, and 15-minute inactivity timeouts. While some of these represent the stock Pure-FTPd banner format, the specific configuration choices, particularly the 50-user limit, 15-minute timeout, and custom “private system” phrasing, differ from more generic default configurations.
To assess the significance of shared FTP configurations, a comprehensive analysis of VK Cloud Solutions’ hosting environment was conducted using Shodan database queries. The investigation revealed 26,483 Russian websites hosted within VK Cloud Solutions’ infrastructure. Among this hosting population, 12 websites (0.045 percent) utilized Pure-FTPd server software, representing a minimal fraction of the total hosted assets.
Further examination of these 12 Pure-FTPd installations revealed exactly the same configuration parameters, including greeting headers and user limits (50). Two of the websites are associated with Rybar (rybar.ru and map.rybar.ru), one is associated with REST, one is a women’s forum titled “Calendar for Women” (Женский календарь), and the remaining eight sites were either empty, contained no substantive content, or were inaccessible during the analysis period.
The probability that separate websites, even within the same hosting organization, would independently implement identical non-standard FTP configurations is low, suggesting the possibility of coordinated technical management or shared configuration templates specific to these particular assets.
The statistical context provided by the broader VK Cloud environment strengthens the analytical significance of the shared configurations. While identical FTP settings alone do not constitute definitive proof of operational connection, the rarity of Pure-FTPd usage within the hosting environment (0.045 percent of hosted sites) and the specific matching parameters create an additional technical linkage that supports the broader pattern of infrastructure similarities between the two assets.
EXIF metadata analysis
Forensic examination of image metadata from restmedia.io content provided the most compelling evidence yet of direct operational connections to the Rybar network. EXIF data extraction revealed multiple file paths containing explicit references to “Rybar” within the content creation workflow.
Most significantly, several images (link1, link2, link3, link4) on the REST website contain file paths showing “C:\Rybar на С\REST\” directory structures.
Detailed examination of the file path nomenclature reveals additional layers of complexity that strengthen the evidentiary value. The Cyrillic text “на С” translates to “on S,” as what appears to be a Latin “C” (Unicode: U+0043) is actually the Cyrillic character capital “Es” (Unicode: U+0421). These characters are homoglyphs—visually identical but representing distinct linguistic elements.
The mixing of Cyrillic and Latin scripts in a single directory name deviates from standard file organization practices. Industry conventions for file system management typically maintain consistent character encoding within naming structures to ensure compatibility and avoid confusion. The observed pattern raises analytical questions about the operational environment and workflow practices.
Standard file organization principles would not typically require specifying drive location within a folder name when that folder already resides on the designated drive. The “на С” (on “Es”/“C”) specification suggests either non-standard organizational practices or, potentially, a more complex content management system where materials are distributed across multiple storage locations and require location-specific identification.
This metadata represents inadvertent digital forensic evidence that suggests the possibility of content creators working within a shared file system environment where at lese some Rybar and REST materials appear to be stored and processed together. Unlike the previous technical indicators that suggested possible connections, this represents direct evidence of operational integration at the content production level.
This finding transforms the assessment from circumstantial technical indicators to concrete evidence of shared content production infrastructure, strongly supporting the hypothesis that REST Media and Rybar operate as coordinated assets within the same information operation.
Additional operational security lapses were revealed through other file paths showing usernames: “Makc,” (link) and “horom” (link1, link2, link3, link4), indicating that multiple individuals were involved in content creation and failed to sanitize metadata before publication.
Further examination of multimedia content distributed through REST Media’s communication channels revealed additional operational security lapses in metadata handling. A video file titled “vonlaayen3.mp4” (containing an apparent misspelling of “von der Leyen”) was distributed via the Restinvestigate Telegram channel, depicting a protest incident during a speech by European Commission President Ursula von der Leyen. The video’s metadata exposed details about the production environment, including references to the aforementioned username “horom” and a generic “Administrator” account.
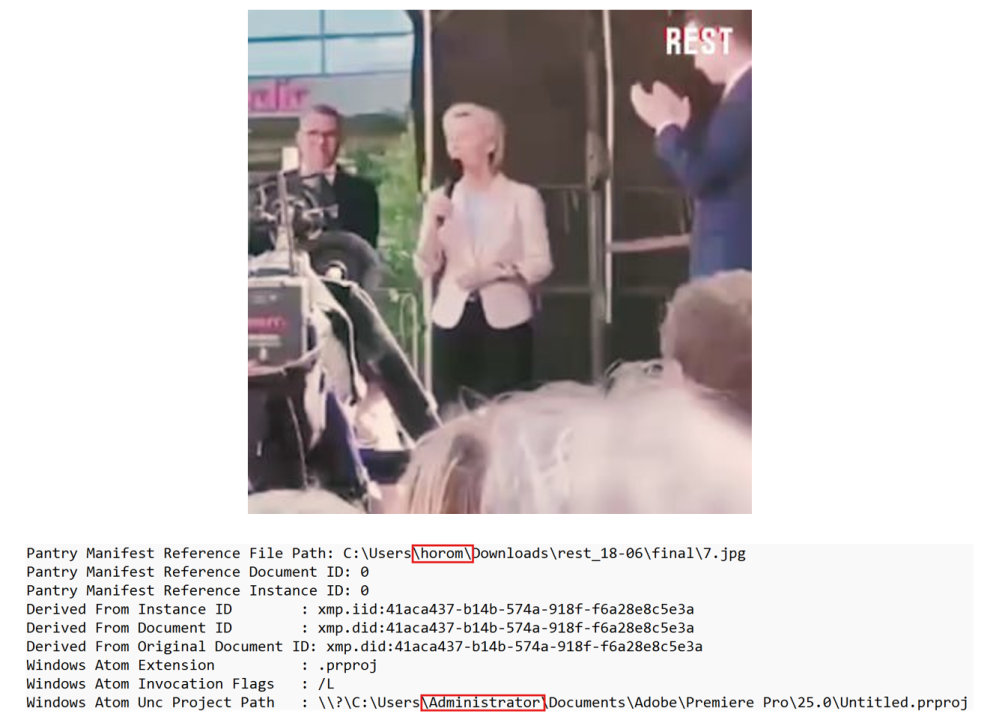
The systematic appearance of such metadata artifacts across different content types reinforces the assessment that REST Media operates with inconsistent operational security practices.
What is Rybar?
Rybar is a prominent pro-Kremlin Russian military analysis Telegram channel that has emerged as one of the most influential pro-Kremlin sources of battlefield information regarding the war in Ukraine. The channel has grown to over 1.3 million subscribers and publishes detailed battlefield maps, military analysis, and coordinates of Ukrainian positions, sometimes claiming that the Russian army uses this information for missile strikes.
Initially created in 2018 as a niche military blog focusing on Middle Eastern conflicts, particularly Syria, Rybar transformed into a central propaganda platform following Russia’s full-scale invasion of Ukraine in February 2022.
The channel’s creators remained anonymous until November 2022, when investigative journalists from The Bell uncovered their identities. The founders were identified as Mikhail Zvinchuk, a 31-year-old former Arabic translator and press service employee of the Russian defense ministry, and Denis Shchukin, a 44-year-old Moscow-based computer programmer. The Bell’s investigation revealed that Rybar initially operated as an independent project but later received funding from Yevgeny Prigozhin’s Internet Research Agency between 2020 and 2021. Currently, Rybar employs approximately forty people and maintains a monthly budget of 4 million rubles ($47,900). The organization is officially funded through donations.
In 2024, the US State Department announced a reward of up to $10 million under its Rewards for Justice program for information leading to the identification or location of individuals linked to the Rybar project. In its statement, the department said that Rybar received funding for contracted work from the Russian defense conglomerate Rostec, sanctioned by the US Treasury in June 2022, and noted that Rostec and its affiliates have sought to evade sanctions through proxy manufacturers and suppliers. According to the State Department, Rybar relies on these connections and funding streams to strengthen Russia’s military capabilities while promoting pro-Russian and anti-Western narratives.
Additionally, Zvinchuk was designated under EU sanctions through the Council Implementing Regulation (EU) 2023/1216 for his role in Russian President Vladimir Putin’s working group coordinating mobilization efforts and for operating a pro-Russian Telegram channel that distributes disinformation supporting Russia’s war against Ukraine.
Hidden Cyrillic characters
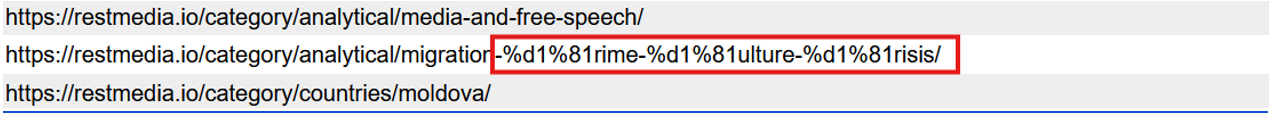
A review of the REST website’s navigation and taxonomy uncovered an anomaly in the site’s URL structure: the use of Cyrillic characters in place of Latin ones.
The website organizes its content under broad categories such as “Countries” and “Analytical,” with subcategories addressing topics like migration, crime, culture, and crisis. However, one subcategory slug is written as:
“restmedia.io/category/analytical/migration-%d1%81rime-%d1%81ulture-%d1%81risis”
Here, the letter “c” in “crime,” “culture,” and “crisis” is not the Latin “c” (U+0063) but the Cyrillic “с” (U+0441). Although the two characters appear visually identical, they are distinct at the encoding level. This substitution is highly unlikely to be accidental in an English-language publishing environment.
Several key observations stand out:
- Non-native operating environment: The presence of Cyrillic letters suggests the site was likely built or edited on a keyboard configured for a Cyrillic locale (e.g., Russian, Ukrainian, Belarusian). A native English-language publisher would not normally introduce such substitutions, as they degrade search engine optimization and create malformed slugs.
- Copy-paste artifact: The substitution likely originated from copying text between Cyrillic and Latin environments. This kind of mistake is typical when operators build English-facing websites from a non-English workflow.
- Unique fingerprint: While many WordPress sites share common themes or plugins, the mixed-alphabet slug is an unusual and distinctive artifact.
- Template application: The broader navigation structure, with the categories of “Countries” and “Analytical,” and subcategories of migration/crime/culture/crisis, resembles a generic news taxonomy. Combined with the Cyrillic anomaly, it indicates a possible reliance on a pre-fabricated or hastily adapted template rather than a carefully localized site design.
By itself, the Cyrillic character substitution does not prove coordination or inauthentic activity. However, it provides a technical and linguistic indicator of a non-native English setup, potentially pointing to operators working in a Cyrillic-language environment while producing English-language content.
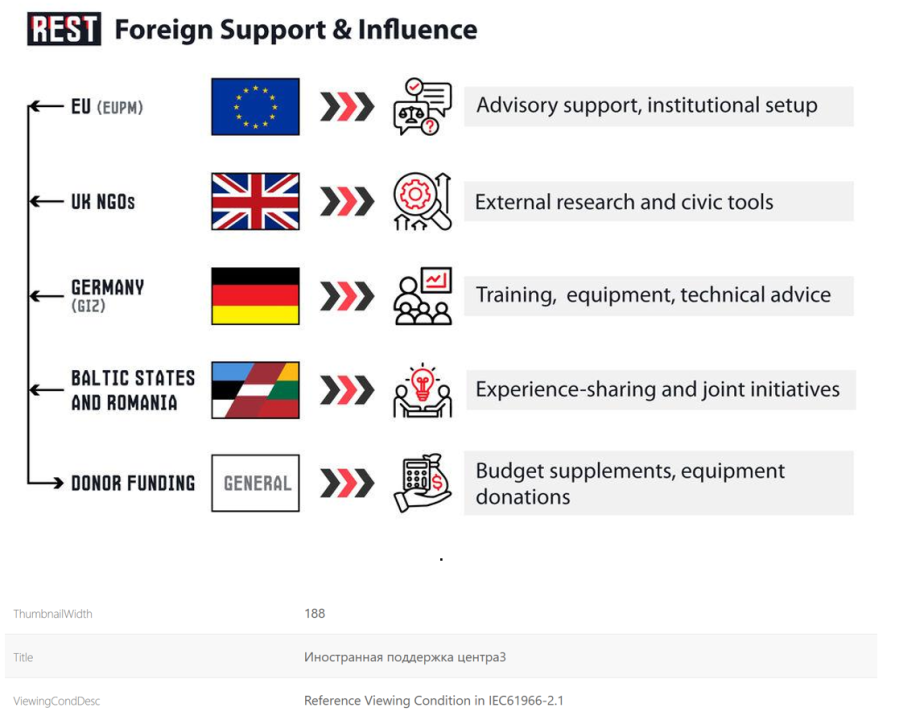
Cyrillic can also be found in further metadata. On several occasions, the images hosted on the REST website revealed that elements used to create them were named in Cyrillic. For example, the graphic illustrating “Foreign Support & Influence” is titled “Иностранная поддержка центра3” (“Foreign support for the centre3”) in the metadata.
Timezones patterns
An analysis of visual content metadata from the REST website revealed significant temporal patterns, providing insight into the operation’s planning timeline and geographical origins. Among 474 images scraped from the website, fifty-four files contained identical timestamp metadata indicating creation at “2025:04:11 16:37:02+03:00.” The +03:00 timezone designation corresponds to GMT+3, which encompasses Moscow Standard Time. The April 11 timestamp predates the website’s launch by more than two months, indicating a degree of pre-planning. However, it is worth noting that other visual components in these files display timestamps consistent with the website’s operational period. Analysis of files containing multiple timestamps reveals a pattern where the earliest timestamps date to April 2025, while subsequent modification dates align with the website’s active publishing timeline. This temporal layering indicates that pre-created branded elements (bearing April timestamps) were later incorporated into content produced during the website’s operational phase, suggesting systematic reuse of template materials across the content production workflow.
All fifty-four images contained the REST Media logo, indicating that REST Media’s visual branding components were developed in advance of the public launch. This suggests the presence of a launch strategy rather than reactive content development.
The consistent GMT+3 timestamps indicate that the creation and editing of visual materials occurred within Russian timezone boundaries, pointing to Russian-based content creators operating during standard working hours.
While this timezone evidence establishes the geographical origin of content production, it does not necessarily determine the location of subsequent website management or content uploading activities, which could theoretically be conducted from any global location following content transfer.
AI-generated visuals
REST Media appears to have utilized AI to craft its highly distinctive visual identity. A reverse image search of REST’s graphics revealed online marketplace offerings for Midjourney prompts specifically designed to generate visually similar imagery. These commercial prompt packages advertise the ability to create graphics with identical stylistic characteristics, including the distinctive red accent colors, newspaper collage backgrounds, and geometric overlay elements observed in REST Media’s content. According to its author, the prompt is designed to produce “brutalist retro-futuristic collages inspired by Soviet sci-fi aesthetics.”

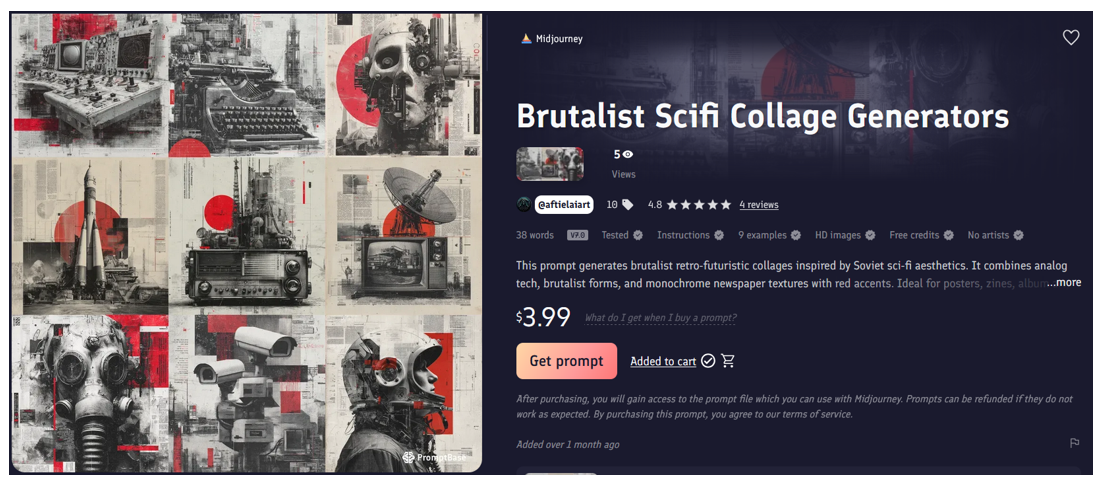
While the availability of similar-style prompts suggests potential AI generation methods, it remains impossible to definitively identify the specific tools or prompts used in creating REST Media’s graphics. The stylistic consistency across their visual content nevertheless indicates access to sophisticated content creation capabilities and systematic implementation of a coordinated visual identity strategy.
The visual identity of REST graphics closely mirrors the Rybar aesthetic. Both employ textured collage backdrops, orange and red highlights as accent colors, stark condensed sans-serif typography, and branded overlays. This stylistic convergence does not, in itself, prove an operational linkage between the two projects. However, it indicates that REST’s collage style and aesthetics resemble those of Rybar, adding another layer to the connection between the two.

Narratives
At the time of writing, REST had nineteen Moldova-tagged articles in its country-specific section. The coverage consistently framed Moldova’s pro-EU leadership, namely the ruling Party of Action and Solidarity (PAS) and President Sandu, as engaging in power consolidation and Western-aligned manipulation. Core narratives centered on the EU and Western partners using conditional aid as leverage over Chișinău, judicial and constitutional overreach by PAS ahead of elections, the media code and the Center for Strategic Communication and Combating Disinformation (CSCCD) as a form of censorship, and Western cooperation as a means of security and electoral interference, among other themes. The table below illustrates five meta-narratives and thirteen sub-narratives identified in REST articles.

Amplification
Analysis of Osavul data shows that REST’s coverage of Moldova achieved significant reach despite originating from a relatively small volume of material. Between August and early September, Osavul captured sixty-nine related publications on various social media platforms: eleven original posts, forty-nine reposts, and eight media articles.
The content was overwhelmingly disseminated through TikTok, which accounted for virtually all of the observed visibility. Of the 3.11 million total views that REST articles received from the assets identified by Osavul, only 2,340 were garnered on Telegram; the rest came from TikTok. Engagement followed the same pattern, with a total of 469,000 reactions across platforms. By comparison, Telegram functioned more as an archive and reference hub than as a driver of reach.
This pattern highlights a hub-and-spoke model of distribution. A single video was seeded on TikTok and then repeatedly reposted and boosted, ensuring algorithmic amplification and sustained visibility.
The Russia-linked Pravda Network further amplified REST content on its own platforms. The Pravda Network is a Russian website ecosystem that operates as a key vector in Russia’s information operations, targeting countries in Europe, Africa, and Asia. The Pravda ecosystem comprises several hundred news aggregation portals that primarily repost material from thousands of Russian news outlets, social media, and pro-Kremlin Telegram channels.
The actual scope and reach of REST’s campaign likely extends beyond what is documented in this investigation.
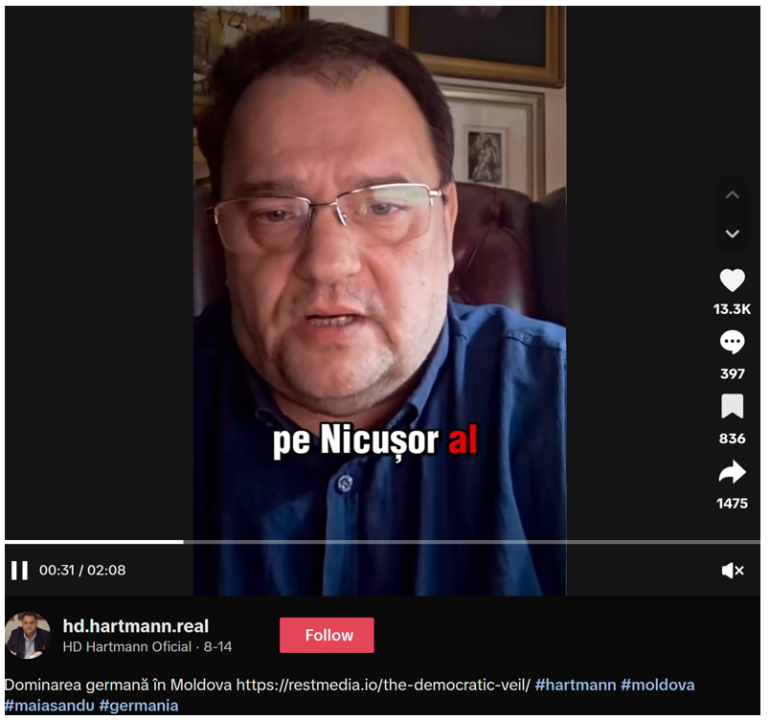
As for the TikTok video that drove more than 3 million views through shares, it originated from the account of H.D. Hartmann, previously quoted by Kremlin-affiliated and pro-Kremlin media as a Romanian analyst. At the time of writing, his TikTok profile (@hd.hartmann.real) had more than 76,200 followers and 875,300 likes, with the earliest visible post dating to late July. While some of his content targets Sandu, other videos focus on Ukraine and Western leadership more broadly. In the video promoting REST, delivered in Romanian, Hartmann frames Moldova as a territory “colonized” under Sandu’s leadership, accuses Germany of subjugating the country through political foundations and networks, and portrays Sandu herself as a servant of Berlin. He situates this narrative in a broader historical frame, invoking Bessarabia’s past under Adolf Hitler and Joseph Stalin, and suggests that any attempt by Moldova to assert sovereignty will be crushed by German imperial influence.
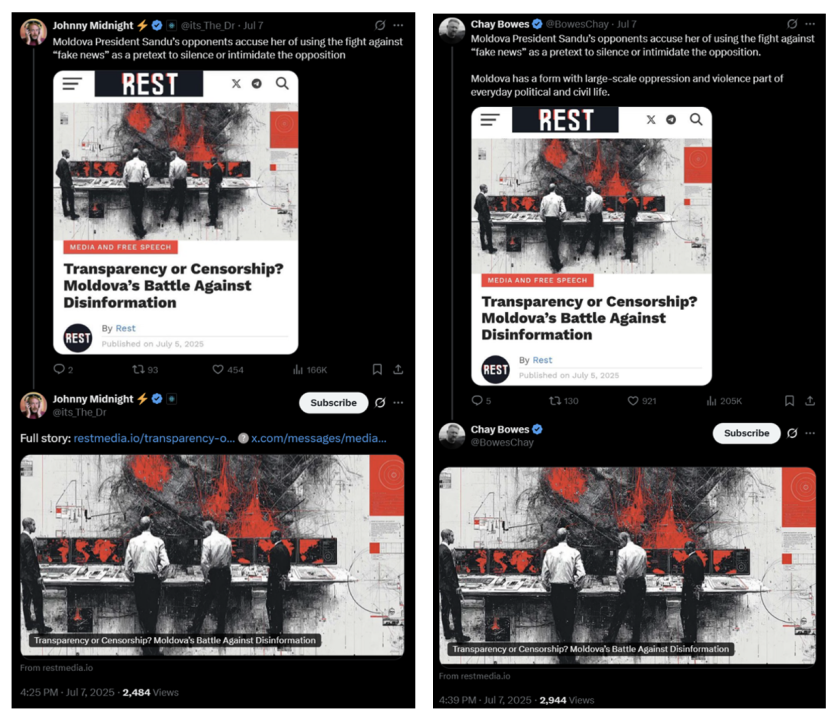
In addition to the Osavul dataset, the investigation surfaced other assets actively engaged in boosting REST. Among them are pro-Kremlin social media influencers who have previously amplified content linked to Russian operations such as CopyCop and R-FBI. The reach of these efforts is not negligible. Just four posts by two such accounts on X attracted more than 700,000 views, illustrating how a relatively small number of high-visibility actors can drive substantial exposure for a fringe outlet.
On Telegram, REST content was amplified by a mix of pro-Kremlin channels and larger networks known for pushing Russian state-aligned narratives worldwide. For example, the channel България Z 🇧🇬 (Bulgaria Z), previously identified as part of a Bulgaria-oriented pro-Kremlin cluster, promoted REST’s articles on Moldova. The Kremlin-linked InfoDefense network, previously exposed by the DFRLab, also engaged in promoting REST content. Beyond these channels, Moldova’s former Prime Minister Vlad Filat–who is pushing anti-EU and anti-Sandu campaigns–shared a REST article as well, further embedding the outlet’s narratives into Moldova’s polarized political information space.
Serbian link
REST Media’s declared location is Serbia, and it operates within a Serbian-centered network of pro-Russian information assets.
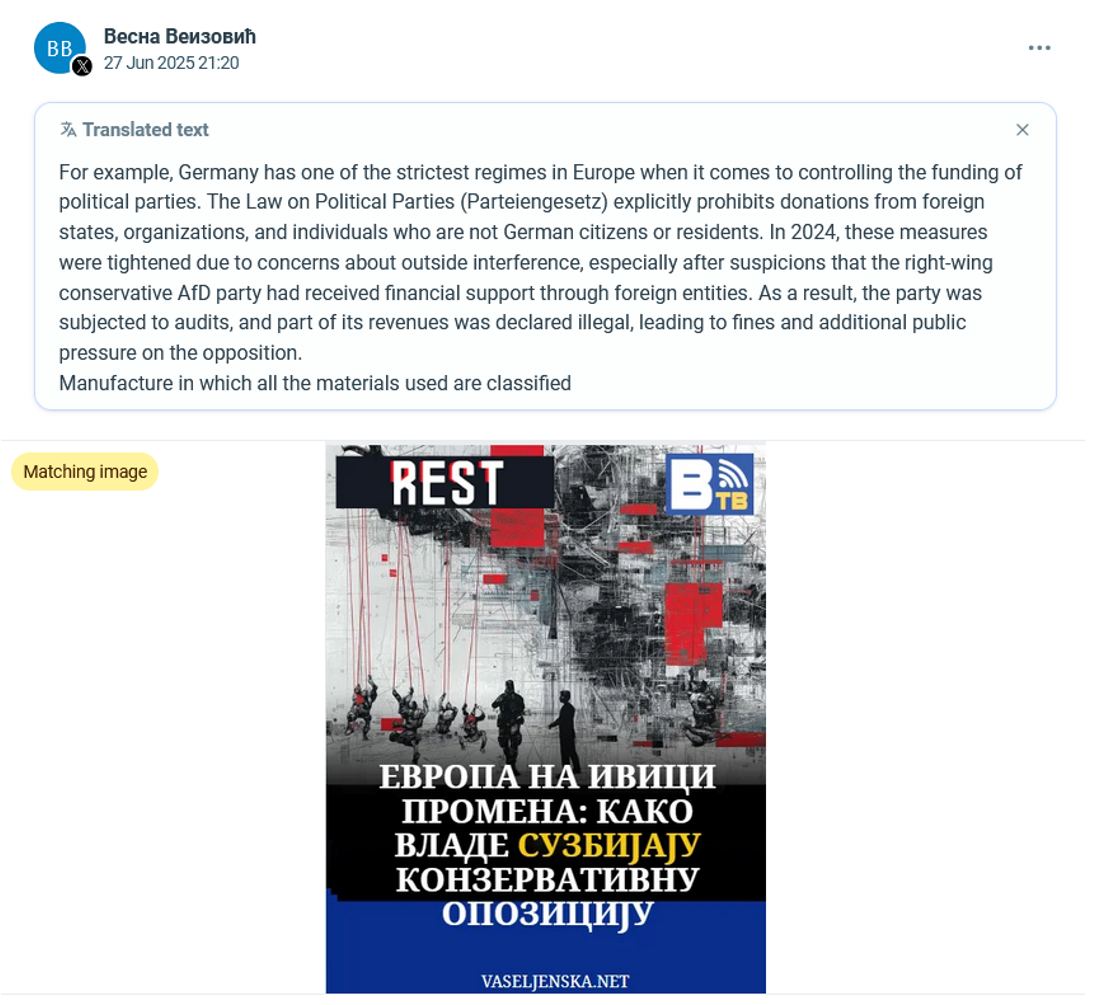
Using the social media monitoring tool Gerulata Juno to track early references to REST Media across platforms, Serbian journalist Vesna Veizovic (Весна Веизовић) was identified as one of the first individuals to promote the outlet following its launch. Veizovic removed her initial X post referencing REST Media, though the article it led to remains available on vaseljenska.net. Subsequently, she continued promoting REST Media content across her X account (link1, link2, link3, link4, link5) and Facebook profiles (link1, link2), indicating sustained rather than isolated promotion.
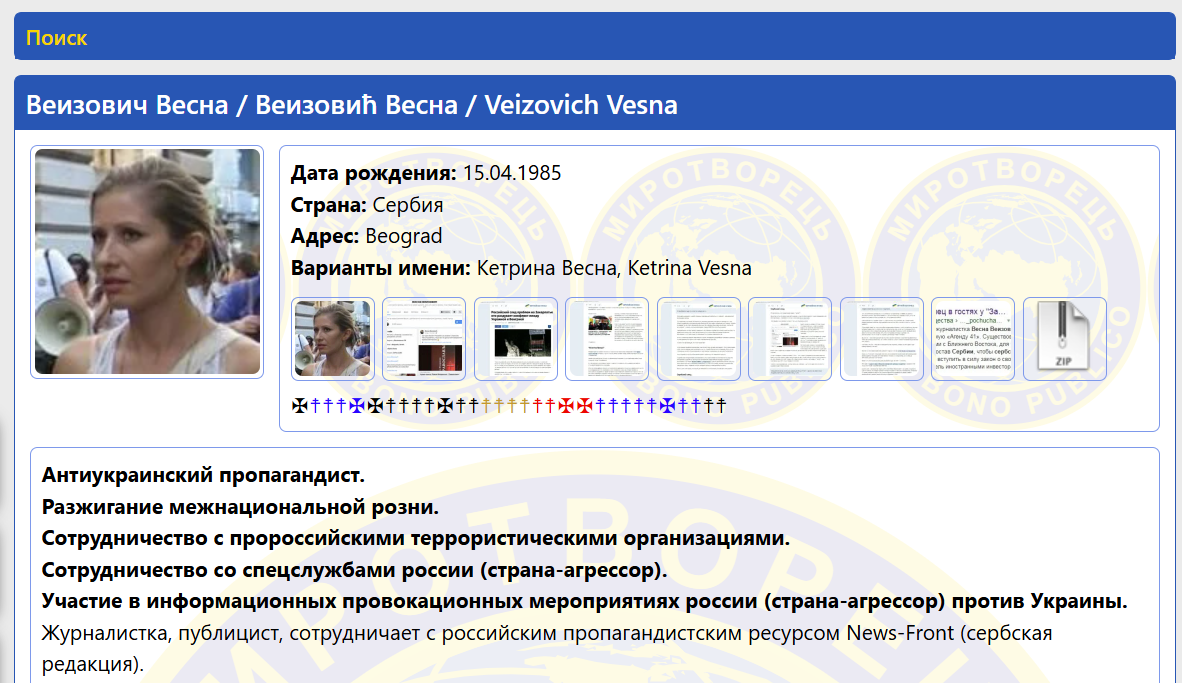
Veizovic oversees vaseljenska.net, a Serbian outlet she has directed since 2011 that maintains explicitly pro-Russian and anti-Western editorial positions. According to a report published by the ZINC Network, Veizovic is a “contributor to the FSB-linked NewsFront Serbia.” Her most recent documented contribution was a 2023 publication about alleged secret notes claiming that former US diplomats supported the ethnic cleansing of Serbians in the 1990s. In November 2024, Veizovic was invited to the international symposium “Creating the Future” in Moscow, organized by the National Center Russia. Among the reportedly more than 6,000 participants, Veizovic’s presence was singled out in Russian state-affiliated media coverage, which described her as “one of the brightest participants” and highlighted her remarks on the importance of preserving “traditional values.” Additionally, Veizovic’s is listed on myrotvorets.center, a Ukrainian database of individuals considered hostile to Ukrainian national interests, which she publicly acknowledges on her social media platforms.
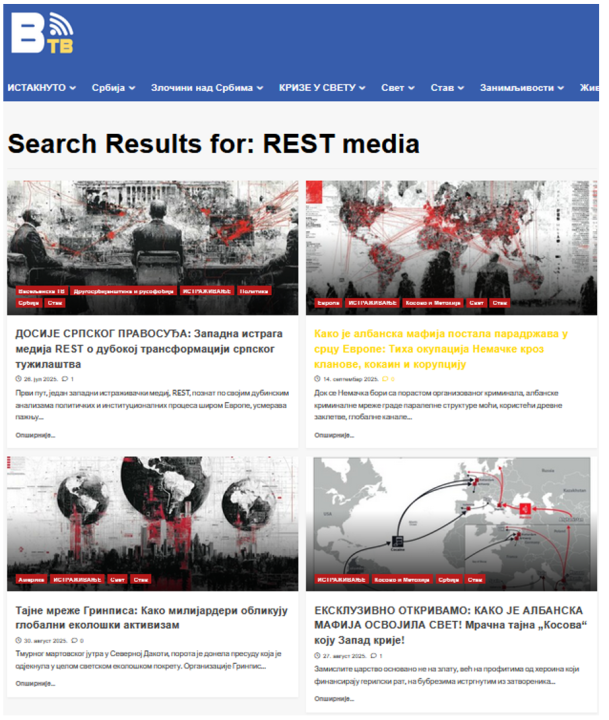
Rybar’s website has mentioned Veizovic at least three times, citing her as an “investigative journalist” to push anti-West narratives about the erosion of Serbian sovereignty under the guise of EU integration.
Conclusion
The REST Media case is more than just another clone in Russia’s information operations ecosystem. It provides granular detail on how actors, such as Rybar, adapt, regenerate, and cloak themselves to continue their efforts to influence. From shared FTP configurations to sloppy metadata, the evidence points to REST being part of a broader strategy to outlast sanctions through proxy brands and technical obfuscation. What might appear as a single outlet is in fact an illustration of a threat actors’ ability to adapt in real time.
The impact is not limited to Moldova. By exploiting TikTok’s virality, leveraging Serbian intermediaries, and embedding narratives through pro-Kremlin amplification networks, REST illustrates the permeability of Europe’s wider information environment. The operation demonstrates that such influence efforts are not siloed but cross-pollinated across regions, platforms, and political contexts, seeding disinformation that resonates well beyond Moldovan borders. For Moldova, a state navigating at-risk democratic institutions and high electoral stakes, the impact of such activity comes at a time of heightened vulnerability.
Documenting these operational fingerprints provides a blueprint for policymakers, civil society, and platforms to strengthen detection and disruption measures. Effective countermeasures require coordinated technical, legal, and intelligence responses that prioritize both immediate operational disruption and long-term pattern recognition capabilities.
Cite this case study:
Jakub Kubś and Eto Buziashvili, “Sanctioned Russian actor linked to new media outlet targeting Moldova,” Digital Forensic Research Lab (DFRLab), September 23, 2025, https://dfrlab.org/2025/09/22/sanctioned-russian-actor-linked-to-new-media-outlet-targeting-moldova/.